Understanding Cloud Networking: A Complete Guide
Vaibhav Gramni
Jan 13, 2026
Cloud networking is the layer that determines how everything else behaves—performance, security, availability, and cost. It doesn’t announce itself when it’s working, but every scaling issue, latency spike, and security exception eventually traces back to network design choices.
As organizations move toward distributed architectures—spanning regions, cloud providers, edge locations, and remote users—the network stops being a static foundation and becomes a living system. Policies are enforced through software, connectivity is defined by identity rather than location, and traffic paths change dynamically based on demand and health.
Understanding cloud networking today means understanding how virtual networks are built, secured, connected, and operated at scale. This guide breaks down those fundamentals in practical terms, covering architectures, models, tools, and real-world considerations for building cloud networks that remain reliable as environments grow more complex.
What is Cloud Networking, and How Does it Work?
Cloud networking is the way you connect applications, data, users, and services inside and across cloud environments. Instead of relying on fixed hardware in a single data center, a cloud network uses virtual routers, firewalls, gateways, and load balancers that run in the cloud and are controlled through software.
You still have the same basic goals as traditional networking, such as secure connectivity and predictable performance, but everything is built and managed more flexibly.
Think of it as a set of building blocks you assemble to match how your applications work. Virtual private clouds create isolated segments where workloads live. Subnets organize those workloads by function or security level. Cloud network services like DNS, VPNs, and application gateways handle how traffic flows between internal systems, on-premises environments, and the public internet.
The real advantage comes from being software-defined. Network policies, routes, and security controls are written as code and deployed through automation, which means you can roll out changes quickly and keep environments consistent across regions. The flip side is that mistakes can scale just as fast if the design is not thoughtful, making careful planning essential from the start.
Security works differently in cloud environments. Instead of relying only on perimeter firewalls, modern cloud security network approaches combine micro segmentation, identity-based access, and encryption in transit. These layers protect data without slowing teams down when aligned with your overall cloud network architecture.
Cloud networking today rarely exists within a single provider. Most organizations run hybrid environments that connect on-premises systems to the cloud, or multi-cloud architectures spread across providers. Without consistent policies and dependable connectivity, these environments fragment quickly, making it difficult to operate them as one unified system.
Why is a Cloud-Based Network Critical for Modern Enterprises?
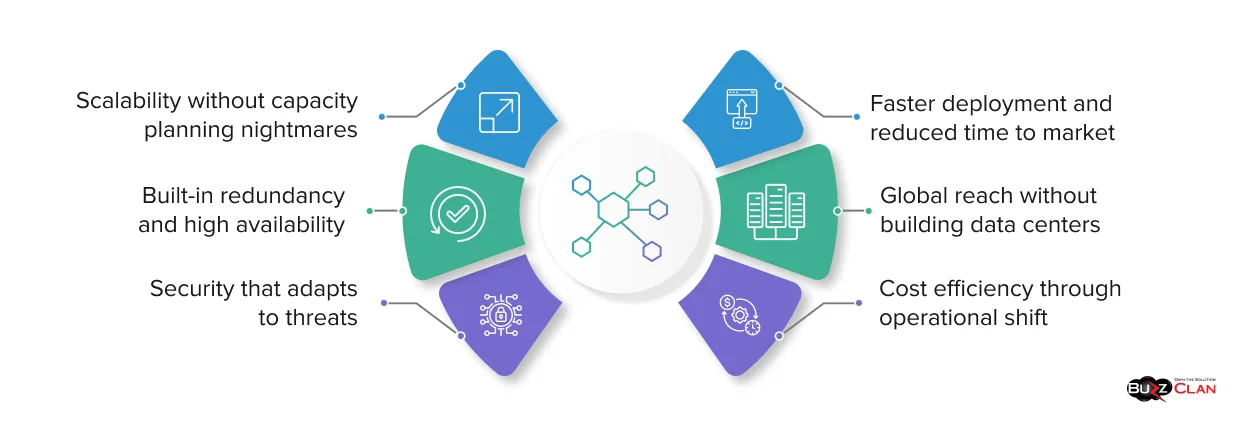
Cloud migration fails to deliver its full value when the network strategy stays rooted in legacy design. Traditional networks cannot keep pace with elastic scaling, globally distributed users, or dynamic security requirements. Cloud-based networking is built specifically for these conditions, enabling performance and control that on-premises infrastructure cannot replicate.
- Scalability without capacity planning nightmares – Traditional networks required you to estimate peak capacity months in advance, purchase hardware, and hope your projections were accurate. Cloud networking lets resources scale up or down automatically based on actual demand, expanding during traffic spikes and contracting when things quiet down, so you’re not paying for unused capacity. This is a core principle of elasticity in cloud computing that transforms how infrastructure responds to real-world usage patterns.
- Faster deployment and reduced time to market – Provisioning a new network segment in a traditional environment could take weeks between procurement, installation, and configuration. With cloud network management, teams can spin up entire environments in minutes using infrastructure as code, which matters when your business needs to launch new services quickly without waiting for infrastructure teams to catch up.
- Built-in redundancy and high availability – Cloud providers build redundancy into their network infrastructure across multiple availability zones and regions. Your applications can automatically failover if one zone experiences issues, keeping services running without manual intervention. Understanding cloud deployment models helps organizations choose the right architecture for their availability requirements.
- Global reach without building data centers – Expanding to new geographic markets used to mean building or leasing data center space in those regions. Cloud networking gives you presence in dozens of locations worldwide without the capital expense or lead time, enabling true global operations through modern digital infrastructure.
- Security that adapts to threats – Network security in cloud computing evolves with the threat landscape. Cloud providers continuously update security capabilities, and you can apply patches or policy changes across your entire environment simultaneously. Implementing comprehensive cloud security best practices ensures your network defenses stay ahead of emerging threats.
- Cost efficiency through operational shift – A cloud network shifts spending from capital expenses on hardware to operational expenses that scale with actual usage. You eliminate costs around physical maintenance, power, cooling, and specialized staff needed to manage proprietary networking equipment. Organizations practicing effective cloud cost optimization see immediate returns from this operational model.
Designing a Secure Cloud Network Architecture for High Performance
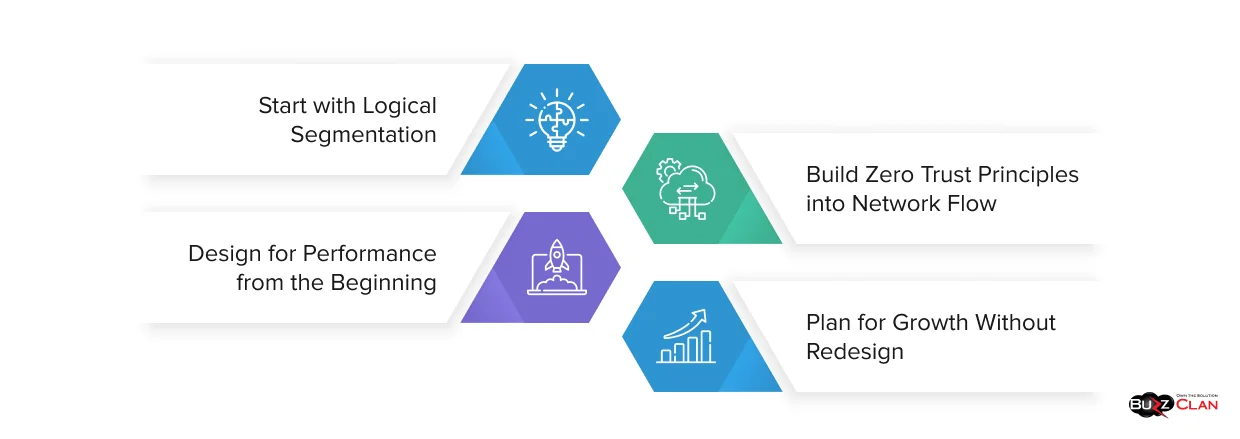
A well-designed cloud network architecture determines whether your applications can scale during demand spikes, whether security teams can enforce policies consistently, and whether performance stays reliable as complexity grows. Getting the architecture right early prevents expensive redesigns that happen when networks become bottlenecks. Security and performance often get treated as competing priorities, but modern cloud network architecture builds security into the foundation rather than layering it on afterward, which means controls reinforce performance instead of fighting against it.
Start with Logical Segmentation
Cloud networks benefit from clear boundaries that separate workloads by function, security level, and data sensitivity. Virtual private clouds provide isolated environments where applications run independently, while subnets within those VPCs organize resources based on their role in the overall system. Production workloads stay separated from development and testing, customer data remains isolated from internal analytics, and external-facing services operate in different network segments than backend databases. This approach supports both compliance-driven cloud networking requirements and operational clarity when troubleshooting issues.
Build Zero Trust Principles into Network Flow
Traditional network security assumed everything inside the perimeter could be trusted. Cloud network architecture works better when you verify every connection, regardless of where it originates. Identity-based access controls determine which services can communicate, micro segmentation limits lateral movement if something gets compromised, and encryption protects data in transit between components. Organizations adopting serverless computing benefit particularly from these patterns because serverless functions need fine-grained permissions without traditional network boundaries.
Design for Performance from the Beginning
Network latency compounds across distributed systems, where a database query that takes milliseconds becomes noticeably slow when multiplied across hundreds of service calls. Place compute resources close to data sources, use content delivery networks to reduce geographic distance between users and applications, and implement caching strategies that minimize repeated network requests. Understanding types of cloud computing services helps you choose the right architecture patterns for your specific workloads.
Plan for Growth Without Redesign
A network that works perfectly at the current scale can become a constraint when traffic doubles or new regions get added. Cloud network technology, like software-defined networking, allows policies and routes to scale horizontally without manual reconfiguration. IP address schemes should accommodate future expansion, naming conventions need to stay consistent across environments, and monitoring must provide visibility regardless of how large the infrastructure becomes.
How BuzzClan Optimizes, Secures & Operates Your Environment
Building a cloud network is one thing. Keeping it optimized, secure, and running smoothly as your business evolves is where most organizations struggle. Networks that performed well at launch start showing strain under increased load, security configurations drift as teams make quick fixes, and operational complexity grows until simple changes require cross-team coordination and days of planning.
BuzzClan’s approach focuses on continuous optimization rather than one-time implementations. The goal is building networks that improve over time instead of degrading as demands increase.
Performance Tuning Based on Actual Usage Patterns
Most networks are designed around theoretical requirements that don’t match how applications actually behave in production. BuzzClan monitors real traffic flows, identifies bottlenecks before they impact users, and adjusts routing, capacity, and caching strategies based on observed patterns rather than assumptions.
Security that Evolves with Threats
Network security in cloud computing requires constant attention because attack methods change faster than static configurations can address. BuzzClan implements automated threat detection, enforces least privilege access across all network segments, and maintains compliance through continuous monitoring rather than periodic audits. Security policies adapt as new services get added, ensuring protection stays consistent even as your environment expands. Teams benefit from cloud migration strategies that build security into every phase rather than treating it as a final checkpoint.
Proactive Operations that Prevent Incidents
The best operational support addresses problems before users notice them. BuzzClan establishes monitoring that surfaces anomalies early, automates routine maintenance tasks that previously required manual intervention, and maintains runbooks that accelerate response when issues do occur.
Capacity Planning that Matches Business Growth
Cloud networks need to scale in step with business expansion without requiring complete redesigns. BuzzClan forecasts capacity needs based on growth trends, implements auto-scaling policies that respond to actual demand, and ensures new regions or services integrate smoothly into existing architecture. This planning prevents the performance degradation that happens when networks reach capacity limits unexpectedly.
Key Components Every Business Must Understand
Cloud networks function through several interconnected components that work together to keep applications running, data flowing, and users connected. Understanding what each piece does helps you make better decisions about architecture, troubleshooting, and where to invest resources as your environment grows.
Virtual Private Cloud (VPC)
A VPC creates an isolated network environment within the cloud where your resources live and communicate. Think of it as your private section of the cloud provider’s infrastructure, where you control IP addressing, routing, and which resources can talk to each other. VPCs let you replicate traditional network topologies in the cloud while gaining the flexibility to modify them through code rather than physical rewiring.
Subnets
Subnets divide your VPC into smaller segments that organize resources by function or security requirements. Public subnets typically host resources that need internet access, like load balancers or web servers, while private subnets contain databases and internal services that should never be directly accessible from outside. This separation makes it easier to apply security controls and troubleshoot issues because workloads with similar requirements live together.
Load Balancers
Load balancers distribute incoming traffic across multiple servers or containers so no single resource gets overwhelmed. They monitor the health of backend systems and automatically route requests away from anything that’s failing, which keeps applications available even when individual components have problems. Modern cloud network services include application load balancers that make routing decisions based on content rather than just distributing requests evenly.
Gateways and VPN Connections
Gateways control how traffic flows between your cloud network and external systems. Internet gateways allow resources in public subnets to communicate with the public internet, while NAT gateways let private subnet resources initiate outbound connections without exposing themselves to inbound traffic. VPN connections create encrypted tunnels between your cloud environment and on-premises data centers, which is critical when implementing effective hybrid cloud advantages across distributed infrastructure.
DNS and Traffic Management
Domain Name System services translate human-readable names into IP addresses that networks actually use for routing. Cloud DNS goes beyond basic name resolution by enabling intelligent traffic routing based on geographic location, health checks, or weighted distributions.
Security Groups and Network ACLs
Security groups act as virtual firewalls that control traffic at the instance or service level based on rules you define. Network Access Control Lists provide an additional layer that operates at the subnet boundary, filtering traffic before it even reaches individual resources. Together, these create defense in depth where multiple checkpoints protect your cloud security network rather than relying on a single control point.
Content Delivery Networks
CDNs cache static content like images, videos, and scripts at edge locations around the world so users can retrieve them from nearby servers instead of traveling back to your origin infrastructure. This reduces latency, lowers bandwidth costs, and improves performance for global audiences.
Exploring Cloud Networking Models
Cloud networking models determine how resources connect, how traffic flows, and what level of control you maintain over infrastructure. Choosing the right model affects everything from operational complexity to cost structure, and most organizations eventually use multiple models depending on what different applications need.
Public Cloud Networking
Public cloud networking runs entirely within a cloud provider’s infrastructure, where multiple organizations share the underlying hardware while maintaining logical isolation through virtualization. Your applications connect through the provider’s network fabric, benefiting from their global backbone and built-in redundancy without needing to build or maintain physical infrastructure. This model works well when applications are cloud-native, compliance requirements allow shared infrastructure, and teams want to minimize operational overhead.
Private Cloud Networking
Private cloud networking dedicates infrastructure exclusively to your organization, either hosted in your own data centers or through a provider offering dedicated resources. You gain complete control over network design, security policies, and how traffic moves between components, which matters when regulatory requirements prohibit shared infrastructure or when applications need customized network configurations that public clouds don’t support. The trade-off is higher operational complexity because your team owns more of the management responsibility.
Hybrid Cloud Networking
Hybrid cloud networking connects on-premises infrastructure with public cloud resources so workloads can move between environments based on performance needs, cost considerations, or compliance requirements. Applications might process sensitive data on premises while using cloud resources for analytics, or keep core systems local while extending capacity to the cloud during peak demand. Making this work requires secure connectivity between environments, consistent identity management across platforms, and clear policies about which data lives where.
Multi-Cloud Networking
Multi-cloud networking spans multiple cloud providers where different workloads run on AWS, Azure, Google Cloud, or other platforms simultaneously. This approach prevents vendor lock-in, lets teams choose the best platform for specific use cases, and provides redundancy if one provider experiences issues. The complexity comes from managing different networking models, security controls, and tooling across providers while maintaining visibility into how everything connects. Successful multi-cloud networking requires strong automation, centralized monitoring, and clear architectural standards that work regardless of which cloud hosts a particular service.
Choosing the Right Model
The choice between networking models depends less on abstract principles and more on practical constraints around compliance, existing investments, team capabilities, and how quickly your environment needs to evolve. Many organizations start with public cloud networking for new applications while maintaining private or hybrid models for systems that can’t move yet. What matters is having a clear strategy that matches business requirements rather than adopting models because they seem technically interesting.
Cloud Connectivity Options Explained
How you connect cloud resources to each other, to on-premises systems, and to end users directly impacts performance, security, and cost. Different connectivity options solve different problems, and understanding when to use each one prevents the bottlenecks that happen when networks are over-engineered or under-provisioned.
Public Internet Connectivity
The simplest approach routes traffic over the public internet using standard protocols and encryption to protect data in transit. This works well for applications where latency variability is acceptable, bandwidth requirements are moderate, and cost control matters more than guaranteed performance. Public connectivity makes sense for web applications serving distributed users, development environments that don’t need dedicated links, or backup and disaster recovery traffic that runs during off-peak hours. The downside is unpredictable performance during network congestion and exposure to internet-based threats that require additional security layers.
Direct Connect and Dedicated Links
Dedicated connections bypass the public internet entirely by establishing private links between your data center and cloud provider infrastructure. These connections deliver consistent latency, higher throughput, and better security because traffic never touches the public network. Organizations use dedicated links when moving large datasets regularly, running latency-sensitive applications like real-time analytics, or meeting compliance requirements that prohibit sensitive data from traversing public networks.
VPN Connections
Virtual Private Networks create encrypted tunnels over existing internet connections, providing secure connectivity without the cost or lead time of dedicated circuits. Site-to-site VPNs connect entire networks together so on-premises systems can communicate with cloud resources as if they were on the same local network. VPNs work well for hybrid cloud networking scenarios where security matters more than maximum performance, or when dedicated links aren’t justified by traffic volume.
Peering Connections
Peering links different virtual networks together within the same cloud provider or across providers, allowing resources to communicate privately without going through public gateways. This reduces latency, eliminates data transfer costs between peered networks, and simplifies security because traffic stays within controlled environments. Organizations use peering when running multi-tier applications split across different VPCs, connecting production and shared services networks, or building multi-region architectures where resources need fast, secure communication across geographic boundaries.
Service Endpoints and Private Links
Service endpoints and private links let cloud resources access platform services like storage, databases, or APIs through private network paths instead of routing through public endpoints. This matters when compliance policies prohibit sending data over the internet, even encrypted, or when minimizing the attack surface is critical. Private connectivity to managed services also improves performance by reducing hops and keeping traffic on the provider’s backbone network rather than the public internet.
Transit Gateways and Network Hubs
Transit gateways act as central connection points that simplify network topology by letting multiple VPCs, VPNs, and direct connect links communicate through a single hub rather than requiring mesh connectivity between every pair. This approach scales better as environments grow because adding new networks only requires one connection to the gateway instead of establishing links to every existing network. Organizations implementing FinOps in the cloud benefit from transit gateways because they reduce the number of connections to manage and optimize data transfer costs across complex architectures.
Cloud Networking for Hybrid Workforces & Remote Teams
The shift to distributed work changed what networks need to accomplish. Applications that used to serve users within office buildings now need to reach people working from home offices, coffee shops, airports, and co-working spaces scattered across different cities and countries. Traditional VPNs that assume everyone is connected from a few known locations don’t work well when your workforce is distributed everywhere.
Cloud networking solves these challenges by moving security and access controls closer to where users actually connect rather than forcing all traffic through centralized data centers. This approach improves performance because users access applications directly instead of routing through corporate networks first, and it strengthens security by verifying identity and device health before granting access to specific resources.
Zero Trust Network Access
Zero-trust networking assumes no connection is automatically trustworthy regardless of where it originates. Every user and device gets verified before accessing applications, permissions are granted based on identity and context rather than network location, and access is limited to exactly what someone needs rather than opening broad network segments. This model works better for remote teams because it doesn’t require everyone to connect through a central VPN that becomes a bottleneck. Organizations adopting cloud adoption frameworks often implement zero trust as part of modernizing security for distributed workforces.
Cloud-Based Application Delivery
Modern cloud network architecture routes users directly to cloud-hosted applications through optimized paths rather than forcing traffic through on-premises data centers first. This reduces latency for remote workers accessing SaaS platforms, cloud-based collaboration tools, or applications migrated to public cloud infrastructure. Content delivery networks cache frequently accessed content close to users globally, making application performance consistent regardless of geographic location.
Secure Access Service Edge (SASE)
SASE combines network connectivity and security functions into a cloud-delivered service that protects users regardless of where they connect. Instead of routing traffic through corporate firewalls, SASE inspects and secures connections at the network edge close to users. This architecture provides consistent security policies whether someone is accessing resources from a home office, traveling, or working from a branch location. Cloud network management becomes simpler because security follows users and applications rather than being tied to specific physical locations.
Managing Performance for Distributed Teams
Network performance matters more when teams are distributed because slow application response directly impacts productivity. Cloud networking addresses this through intelligent routing that directs traffic over the fastest available paths, quality of service policies that prioritize business-critical applications over background traffic, and monitoring that identifies performance issues before users complain. Organizations implementing cloud observability gain visibility into how network performance affects distributed teams and can optimize accordingly.
Enabling Collaboration Without Compromising Security
Hybrid workforces need to collaborate across tools, share data, and access systems without security becoming an obstacle. Modern cloud network solutions balance accessibility with protection by implementing granular access controls, encrypting data in transit and at rest, and providing secure channels for sharing resources with external partners. The goal is to make legitimate work friction-free while blocking unauthorized access, which requires networks designed around how people actually work rather than how offices used to be structured.
Cloud Networking Use Cases Across Industries
Cloud networking solves different problems depending on what industry you operate in and what business challenges your infrastructure needs to support. The technical components stay mostly the same, but how they get configured and prioritized shifts based on regulatory requirements, performance expectations, and what happens when networks fail.
Healthcare and Life Sciences
Healthcare organizations use cloud networking to connect electronic health records systems, medical imaging platforms, telemedicine services, and research databases while meeting strict HIPAA compliance requirements. Networks need to isolate patient data properly, encrypt everything in transit, and maintain audit trails showing who accessed what information and when. Performance matters because clinicians making treatment decisions can’t wait for systems to load, and reliability is critical because network outages directly impact patient care. Organizations in this space benefit from cloud compliance solutions that embed regulatory requirements into network architecture from the start.
Financial Services and Banking
Financial institutions run trading platforms, payment processing systems, customer portals, and fraud detection services that demand high availability and predictable low latency. Cloud networks for financial services implement strong segmentation to separate customer-facing applications from internal systems, use dedicated connections for high-value transactions that can’t tolerate public internet variability, and maintain geographic redundancy so services stay available during regional outages. Security controls need to prevent unauthorized access while supporting the real-time processing speeds that modern financial systems require.
Retail and E-Commerce
Retail organizations rely on cloud networking to handle traffic spikes during sales events, connect point-of-sale systems with inventory management, and deliver consistent website performance to customers worldwide. Networks need to scale automatically when demand surges during holiday shopping or product launches, route traffic through content delivery networks so page load times stay fast regardless of customer location, and maintain secure payment processing that meets PCI DSS requirements.
Manufacturing and Supply Chain
Manufacturing companies use cloud networks to connect factory floor systems with supply chain platforms, enable real-time monitoring of production equipment, and support collaboration between design teams distributed across different locations. Networks must handle industrial IoT devices generating sensor data continuously, provide reliable connectivity to remote facilities that might have limited internet options, and maintain security boundaries that prevent operational technology systems from being compromised through IT networks. Hybrid cloud networking becomes essential when legacy manufacturing systems need to integrate with modern cloud-based analytics.
Government and Public Sector
departments across different locations, and maintain security for sensitive data while enabling appropriate information sharing. Networks must meet specific compliance frameworks like FedRAMP, implement strong access controls that align with security clearance levels, and maintain availability for critical services that citizens depend on. Multi-cloud networking often appears in government because different agencies might use different cloud providers while still needing to collaborate securely.
Cloud Networking Tools & Platforms
Managing cloud networks effectively requires tools that provide visibility into traffic flows, automate configuration changes, enforce security policies, and help troubleshoot issues before they impact users. The right platform choices determine whether network operations stay manageable as environments grow or become increasingly difficult to control.
Native Cloud Provider Tools
AWS, Azure, and Google Cloud each provide their own networking management tools that integrate tightly with their respective platforms. AWS offers VPC management, Route 53 for DNS, CloudFront for content delivery, and Transit Gateway for connecting multiple networks. Azure provides Virtual Network, Azure DNS, Front Door for global load balancing, and Virtual WAN for simplified wide-area connectivity. Google Cloud includes VPC networking, Cloud DNS, Cloud CDN, and Network Connectivity Center. These native tools work well when staying within a single cloud ecosystem, but managing multi-cloud environments requires either learning multiple platforms or adding third-party tools that provide unified management.
Software Defined Networking Platforms
SDN platforms abstract network control from underlying infrastructure, letting teams define policies and routing through software instead of manual device configuration. Solutions like VMware NSX, Cisco ACI, and open-source options like OpenStack Neutron provide centralized management, automated provisioning, and consistent policies across different environments.
Network Monitoring and Observability Tools
Understanding what’s happening across distributed cloud networks requires monitoring that shows traffic patterns, identifies bottlenecks, and surfaces anomalies before they cause outages. Tools like Datadog, New Relic, and CloudWatch provide visibility into network performance metrics, while flow analysis platforms like VPC Flow Logs or Azure Network Watcher help troubleshoot connectivity issues. Effective monitoring integrates with incident response workflows so teams get alerted about problems automatically rather than discovering issues when users complain.
Security and Compliance Platforms
Cloud network security requires tools that enforce policies consistently, detect threats in real time, and maintain compliance with regulatory frameworks. Cloud-native options like AWS Security Groups, Azure Network Security Groups, and Google Cloud Firewall rules provide basic traffic filtering. More comprehensive platforms like Palo Alto Networks Prisma Cloud, Check Point CloudGuard, and Fortinet FortiGate offer advanced threat detection, unified policy management across multi-cloud environments, and compliance reporting that maps network configurations to specific regulatory requirements.
Infrastructure as Code Tools
Managing cloud networks through code rather than manual configuration prevents drift, enables version control, and makes changes repeatable across environments. Terraform allows defining network infrastructure across multiple cloud providers using a common language. AWS CloudFormation, Azure Resource Manager templates, and Google Cloud Deployment Manager provide provider-specific options that integrate deeply with their respective platforms. Teams using infrastructure as code can spin up entire network environments from templates, test changes in isolated environments before production deployment, and recover quickly from failures by redeploying known configurations.
Network Automation Platforms
Automation tools reduce operational overhead by handling repetitive tasks, enforcing standards, and responding to common issues without manual intervention. Ansible, Puppet, and Chef can automate network device configuration and policy enforcement. Cloud-native automation like AWS Lambda or Azure Functions triggers network changes based on events, such as automatically adjusting security rules when new services get deployed. Successful cloud modernization efforts rely heavily on automation that keeps networks aligned with application changes without requiring constant manual updates.
Choosing Tools That Actually Work Together
The challenge isn’t finding tools but selecting ones that integrate well, scale with your environment, and match your team’s expertise. Native cloud tools work great within their ecosystems but create gaps in multi-cloud setups. Third-party platforms provide consistency across providers but add another layer to learn and manage. BuzzClan helps organizations navigate these decisions by evaluating current toolchains, identifying integration gaps, and implementing solutions that actually support how teams work rather than creating new operational burdens.
The best approach often combines native tools where they excel with specialized platforms that fill specific gaps, creating a toolchain that supports how your teams actually work rather than forcing workflows to match tool limitations.
The Future of Cloud Networking: AI, Edge, 5G & Autonomous Networks
Cloud networking is evolving beyond connecting resources and enforcing policies to becoming an intelligent infrastructure that adapts automatically, predicts problems before they happen, and optimizes performance without human intervention. Several converging trends are reshaping how networks operate and what they can accomplish.
AI-Driven Network Operations
Artificial intelligence is moving from monitoring dashboards into active network management. Machine learning models analyze traffic patterns to predict congestion before it impacts users, identify security anomalies that rule-based systems miss, and recommend configuration changes that optimize performance based on actual usage rather than static policies. Networks are starting to self-heal by automatically rerouting traffic around failures, adjusting capacity in response to demand shifts, and isolating compromised resources before attacks spread.
Edge Computing Integration
The edge brings computation and data storage closer to where information gets generated rather than forcing everything back to centralized cloud regions. This matters for applications like autonomous vehicles, industrial IoT, and augmented reality, where milliseconds of latency make the difference between working and failing. Cloud network architecture is adapting by extending connectivity to edge locations, managing distributed workloads that span core data centers and edge nodes, and maintaining consistent security policies regardless of where processing actually happens. Hybrid architectures that combine centralized cloud resources with edge computing require networks designed for this distribution from the start.
5G Network Convergence
5G networks deliver higher bandwidth, lower latency, and support for massive numbers of connected devices, which changes what cloud applications can accomplish. Cloud networking is converging with 5G through network slicing that dedicates virtual network segments to specific applications, edge computing deployments at 5G base stations, and APIs that let applications request specific network performance characteristics. This convergence enables use cases like remote surgery, factory automation, and smart city infrastructure that depend on guaranteed network performance rather than best-effort connectivity.
Autonomous Network Management
Autonomous networks use AI, automation, and intent-based policies to manage themselves with minimal human intervention. Instead of configuring individual routers and firewalls, teams define high-level business objectives, and the network figures out how to implement them. Systems automatically provision capacity, apply security controls, optimize routing, and adapt to changing conditions without waiting for manual approvals. Organizations implementing cloud infrastructure are moving toward this model, where networks become self-operating platforms rather than infrastructure that requires constant hands-on management.
Multi-Cloud and Hybrid Complexity
As organizations adopt multi-cloud strategies and maintain hybrid environments, networks need to provide consistent experiences across fundamentally different platforms. Future cloud networking abstracts away provider differences so applications can move between AWS, Azure, and Google Cloud based on cost, performance, or regulatory requirements without manual reconfiguration. Software-defined networking and service mesh architectures enable this portability by creating unified control planes that work regardless of underlying infrastructure.
What This Means for Organizations Today
These trends aren’t distant possibilities but changes already happening in production environments. Organizations building cloud networks now should design for intelligence, automation, and distribution rather than assuming centralized control and manual management will remain viable. The networks that age well are those built with flexibility to incorporate AI-driven operations, edge integration, and autonomous management as those capabilities mature from experimental to standard practice.
Go Beyond the Cloud Limits with BuzzClan’s Network Solutions
Most cloud networking implementations follow default configurations that work but don’t excel. Networks perform adequately under normal conditions but struggle when demand spikes, and operational friction slows everything else down.
BuzzClan treats cloud networking as a strategic capability rather than infrastructure plumbing. The focus is on building networks that improve over time, handle growth without constant redesign, and enable innovation instead of constraining it.
What Makes BuzzClan Different
BuzzClan starts by understanding what your business actually needs from cloud infrastructure, looking beyond technical specifications to questions like how quickly new services need to launch, what compliance frameworks constrain decisions, and what happens when networks fail. This business context shapes technical designs that align with real priorities.
Networks get built based on how applications actually behave in production, implementing cloud performance optimization strategies that address latency and throughput based on measured data. Security is designed into architecture from the beginning through defense in depth that combines segmentation, encryption, and access controls without slowing teams down.
For organizations operating across multiple environments, BuzzClan designs networks that work across AWS, Azure, Google Cloud, and on-premises infrastructure while maintaining consistent policies and unified visibility. This includes establishing connectivity patterns that support cloud migration without requiring complete redesigns every time something moves.
The operational approach establishes monitoring that surfaces problems early, automation that handles routine changes, and documentation that helps teams operate independently. The goal is to build sustainable capabilities that your organization owns rather than creating permanent dependency.
How to Choose the Right Cloud Networking Partner
Selecting a cloud networking partner determines whether your infrastructure becomes a competitive advantage or a source of constant operational headaches. The wrong choice leads to implementations that look good in presentations but create problems in production, while the right partner builds networks that actually support how your business operates.
Look Beyond Technical Certifications
Certifications prove someone passed exams, but they don’t guarantee the ability to solve real business problems. The right partner demonstrates experience with environments similar to yours, understands the specific challenges your industry faces, and can explain how they’ve addressed comparable situations for other organizations. Ask about projects that went wrong and how they recovered, because learning from failures matters more than a perfect track record that probably isn’t.
Evaluate Business Understanding
Technical expertise matters, but partners who only think in terms of protocols and configurations miss the bigger picture. Strong partners ask about business objectives before recommending solutions, understand how network performance affects revenue and customer experience, and design architecture that supports your three-year roadmap rather than just solving immediate problems. They should be able to explain technical decisions in business terms that leadership actually cares about.
Assess Multi-Cloud and Hybrid Capabilities
If your strategy involves multiple cloud providers or maintaining on-premises infrastructure alongside cloud resources, verify that potential partners have real experience managing those complexities. Ask how they handle consistent security policies across different platforms, what tools they use for unified management, and how they’ve helped other organizations with similar hybrid requirements. A generic cloud experience doesn’t automatically translate to multi-cloud expertise.
Check for Operational Transfer
Partners who foster permanent dependency aren’t helping you build lasting capabilities. Instead, seek organizations that emphasize knowledge transfer, maintain clear documentation of decisions, train your teams to manage what’s implemented, and provide runbooks for routine operations. The ultimate goal is for your team to operate independently, with the partner stepping in only for complex challenges—not for everyday tasks.
Understand Their Automation Approach
Manual network management doesn’t scale, so partners should demonstrate strong automation capabilities using infrastructure-as-code, configuration management tools, and monitoring that triggers automated responses. Ask how they’ve helped other organizations reduce operational overhead through automation and what percentage of network changes require manual intervention in environments they manage.
Verify Security and Compliance Expertise
If your industry has specific regulatory requirements, the partner needs deep familiarity with those frameworks and how they affect network design. Generic security knowledge isn’t enough when HIPAA, PCI DSS, or FedRAMP compliance is mandatory. Ask for examples of how they’ve addressed compliance in network architecture and what audit artifacts they provide to demonstrate adherence.
Measure Communication and Responsiveness
Technical problems don’t wait for business hours, so understand how partners handle incidents, what response times they commit to, and how they communicate during outages. Clear, proactive communication during problems matters as much as technical skill in solving them. References from current clients provide the best insight into how partners actually behave when things go wrong.
Consider Long-Term Partnership Potential
Cloud networking isn’t a one-time project but an ongoing relationship as your environment evolves. Evaluate whether the partner invests in staying current with new technologies, how they handle changes to your requirements over time, and whether their business model aligns with supporting you long-term rather than just completing initial implementation and moving on.
The right cloud networking partner becomes an extension of your team, brings expertise you don’t need to build internally, and helps you avoid the expensive mistakes that come from learning through trial and error in production environments.
Conclusion
Cloud networking determines whether your infrastructure accelerates business or creates bottlenecks. The difference isn’t budget or technology but designing networks around how your business actually operates rather than replicating outdated patterns in new environments.
Traditional approaches built for centralized data centers fail under distributed cloud demands. Success comes from embracing automation over manual control, verifying every connection instead of trusting perimeters, and building architecture that adapts continuously rather than requiring periodic redesigns.
BuzzClan helps organizations move beyond generic implementations to networks designed for their specific growth trajectory, compliance requirements, and operational realities. The right architecture supports what you need to accomplish three years from now, not just what worked yesterday.
Your network either enables what comes next or forces you to work around its limitations. Build for the future.
FAQs

Get In Touch
Follow Us
Table of Contents
- What is Cloud Networking, and How Does it Work?
- Why is a Cloud-Based Network Critical for Modern Enterprises?
- Designing a Secure Cloud Network Architecture for High Performance
- How BuzzClan Optimizes, Secures & Operates Your Environment
- Key Components Every Business Must Understand
- Exploring Cloud Networking Models
- Cloud Connectivity Options Explained
- Cloud Networking for Hybrid Workforces & Remote Teams
- Cloud Networking Use Cases Across Industries
- Cloud Networking Tools & Platforms
- The Future of Cloud Networking: AI, Edge, 5G & Autonomous Networks
- Go Beyond the Cloud Limits with BuzzClan’s Network Solutions
- How to Choose the Right Cloud Networking Partner
- Conclusion
- FAQs