Cloud Migration Strategy: A Complete Implementation Guide for Enterprise Success
Munish Singh
May 1, 2025
$723.4 billion! Organizations are predicted to spend this sum on cloud services in 2025. Unfortunately, there is another side to the story. Close to 68% of organizations are yet to complete their cloud journey and have yet to enjoy the full potential of cloud computing. Don’t let that happen to your business! The key to cloudifying your business lies in analyzing your requirements, roping in experts, and developing a robust cloud migration strategy plan. This blog will discuss all the aspects of a strong cloud migration strategy and actionable tips to help you turn your business into a cloud powerhouse.
Defining Cloud Migration Strategy
Simply put, it is a roadmap that helps you navigate the migration process. While you might think it is complex, that is far from the truth. You need to keep your business goals and IT environment at the forefront. To ensure a smooth transition, invest ample time and seek the help of experts. You will also need to develop an understanding of cloud environments. This will help you make the best decisions and minimize performance issues.
Importance of a Cloud Migration Strategy
A comprehensive cloud migration strategy will help you ensure the success of your cloud adoption initiatives. Close to 76% of organizations use hybrid clouds, and cloud migration strategies play a huge role. When your plan is fool-proof, you can quickly achieve business objectives, optimize cloud costs, and mitigate risks. A strategic approach will help you ensure compliance with industry standards and boost application performance and overall user experience, allowing you to rake in huge profits and increase your clientele. AI, integration, strategic partnerships, and regional investments will favor their cloud migration efforts in the upcoming years. Still not convinced?
- 94% of enterprises use cloud services in some capacity.
- The global cloud computing market is expected to reach $1.2 trillion by 2028
- 80% of companies report improved productivity and higher ROI post-cloud migration.
- Organizations migrating to the cloud experience a 20-30% reduction in IT costs.
Key Benefits of Cloud Migration
Here is how you can benefit from cloud migration.
- Cost Efficiency: Cloud migration will help reduce operational costs, as you only pay for the necessary resources. This way, you can better plan your budgets and improve your organizational finances. Ashapura, a leading multi-mineral solutions provider, faced challenges with on-premises data management and inefficient infrastructure. Thus, they decided to migrate their operations to AWS. The results will surely shock you! They saw a 40% increase in overall performance and improved return on investment over six years. Cost reductions and improved overall efficiency were added benefits.
- Scalability and Flexibility: You can scale resources up or down based on the demand and ensure optimal performance with cloud elasticity. This much-needed flexibility will help you quickly launch new services and enter new markets. Moreover, when your engineers are free, you can look forward to creating innovative use cases. One such example is that of the leading web player Spotify, which shifted to Google Cloud Platform (GCP) in 2015, and the rest is history.
- Enhanced Security: With advanced security measures like threat detection, data encryption, data backup and recovery, and industry compliance, you can protect sensitive data and minimize risks due to cyber attacks. We all know Evernote, the popular cross-platform note-taking application. However, did you know they were finding it difficult to manage their servers? Not only did they shift to GCP in 2016, but they also successfully transferred 5 billion notes and 5 billion attachments in just 70 days! Not only did this boost performance, but also their disaster recovery processes.
- High Availability: Cloud platforms have multiple data centers that help you reduce latency and reduce downtime. This, in turn, enables you to build trust with customers. For the same, SmugMug, a photo and video-sharing service, migrated its services to AWS Cloud. Not only did they manage to save time on hardware management, but they also ensured a more reliable service for storing billions of photos and videos.
- Promotes Teamwork: Your employees can easily access files and applications anywhere. This is ideal for remote environments as they can be on the same page as their in-office teammates.
Further Reading
Core Components of a Cloud Migration Strategy
Knowing the core components of a good strategy is essential for creating a solid cloud migration plan. Let’s decode each one.
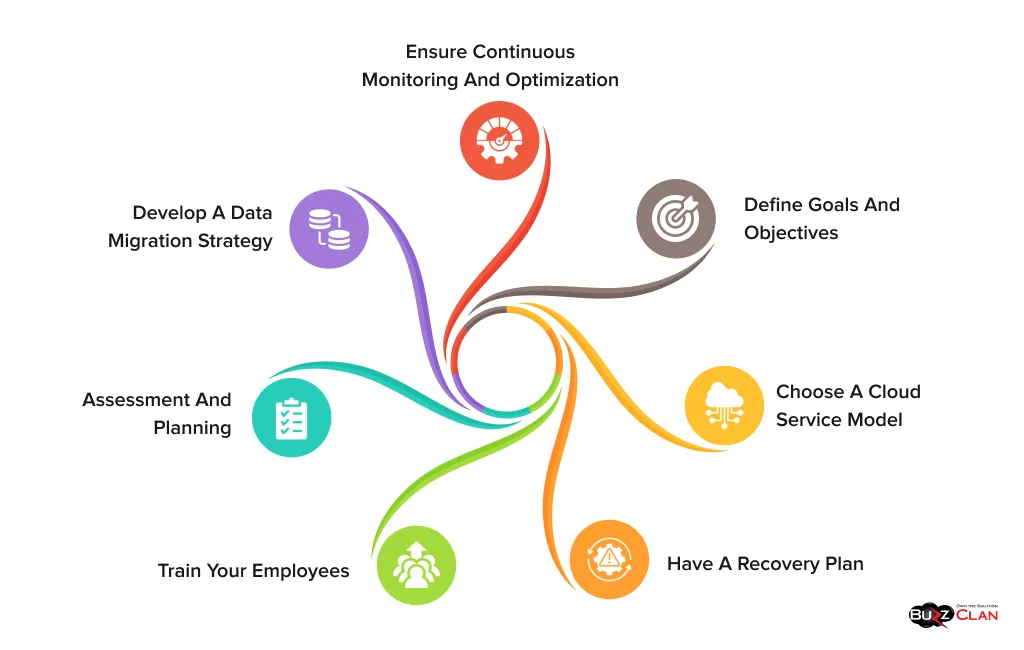
Assessment and Planning
Seldom was a strategy fulfilled without analyzing readiness—the same holds for your current IT environment. You cannot decide one day and implement cloud migration in the next hour. You need to analyze your dependencies, application compatibility, and understand your resource requirements before laying a plan of action. The list doesn’t end here. You must also check staff skills, compliance, and network bandwidth requirements.
Doing all these tasks manually will lead to multiple errors and take time. Thus, it is best to use automated discovery tools, as they will help you find the gaps quickly. Addressing these gaps can reduce the risks of unwarranted challenges during migration. Last but not least, a timeline and a clear roadmap will help you optimize your transition and say goodbye to disruptions.
Define Goals and Objectives
When your business goals are laid out, you can only look forward to cutting costs, improving scalability, and boosting performance. Thus, make it a point to align your goals and objectives to ensure that your deliverables will meet organizational priorities.
Choose A Cloud Service Model
The next step is to choose the right cloud service model. To ensure you collaborate with only the best, you must compare multiple providers to see which best suits your business needs. While some may offer various services, hidden costs might be associated with them. Thus, it is a must to read industry reports and testimonials to get an accurate picture and find the best fit for your business.
Develop A Data Migration Strategy
Now is the time to develop a plan for securely transferring data and minimizing downtime and data loss. A hybrid migration approach will be helpful if you need to transfer data in bulk. This approach allows you to balance costs while maintaining peak performance. However, you must maintain the integrity of your data and ensure encryption using the best standards.
Train Your Employees
If your team is not ready for the process, there is no point in migrating to the cloud. Before making a plan, ensure they know about it and address their concerns. Not all your employees may be technical geniuses and may require handholding. You can use experts’ help to conduct training sessions, help your employees transition smoothly, and adapt to workflows in cloud environments.
Ensure Continuous Monitoring and Optimization
Your job doesn’t end post-migration. You have to ensure that migrated workloads are in the best condition. This means conducting regular audits and implementing measures to reduce costs and enhance security. Wait, there is more to it! You must perform tests manually or use automated tools to detect anomalies and maintain service standards. While this may seem too much initially, it will only help you quickly fulfill your business requirements.
Have A Recovery Plan
The best part of using cloud solutions is that you get access to automated backups and replication features. A disaster recovery plan is a must to ensure that your applications remain accessible and protected from unforeseen outages or failures. So, how can you make one? Well, maintain your backups offline and lay down recovery strategies to ensure uptime even in case of data loss. You can even use real-time monitoring tools to better deal with potential threats during migration.
Selecting the Right Cloud Provider
Here is a comparison of the top providers to help you make a better decision.
| Feature | Amazon Web Services | Microsoft Azure | Google Cloud Platform |
|---|---|---|---|
| Pricing Model | Pay-as-you-go, reserved instances, savings plans | Pay-as-you-go, reserved instances, hybrid benefits | Pay-as-you-go, committed use discounts, free tier |
| Global Availability | 100+ availability zones in 30+ regions | 70+ regions spread across 200+ data centers | 38+ regions and 120+ edge locations |
| Compute Services | EC2, Lambda, ECS, EKS | Virtual Machines, Azure Functions, AKS | Compute Engine, App Engine, Cloud Run, GKE |
| Hybrid Cloud Support | AWS Outposts, Snowball | Azure Arc, Azure Stack | Anthos |
| Compliance Certifications | Extensive global certifications, including HIPAA, GDPR, IOS | Strong compliance focus. | Comprehensive compliance with a focus on privacy |
| User Interface | It is feature-rich but complex to use. | It is intuitive and integrates well with the Microsoft ecosystem. | User-focused and ideal for developers. |
| Strengths | Broad service offerings and an extensive ecosystem | Strong integration with enterprise tools like Office | Exceptional AI/ML, Kubernetes, and analytics capabilities. |
| Weaknesses | It can be overwhelming for beginners | Less mature in some open-source and DevOps areas | Smaller global network and fewer enterprise tools |
| Migration Capacity | It offers various migration services, such as AWS Migration Hub, CloudEndure Migration, and AWS Application Migration, for seamless lift-and-shift or re-platforming. | Provides Azure Migrate, a comprehensive workload assessment, migration, and modernization suite with strong VMware and Windows workload support. | It uses Migrate for Compute Engine, ideal for migrating VMware workloads, Kubernetes-based apps, and databases. |
| Benefits | Not only is it scalable and reliable, but it also easily supports hybrid and multi-cloud environments. You can easily integrate it with third-party tools and look forward to leveraging top-notch AI functionalities. | If you are looking for potent hybrid and on-premises compatibility, this is the best solution. You also get access to built-in cost estimation and analysis tools. | One of the most advanced migration tools, it offers competitive pricing and access to a Kubernetes-native migration approach. |
| Cost Comparison | The pay-as-you-go model is followed. While migration tools are primarily free, additional costs can add up. | The pay-as-you-go model is followed. Migration assessments are fee-free, but storage and network fees apply. | The pay-as-you-go model is followed. However, network egress and compute pricing may increase costs. |
| Best Use Cases |
|
|
|
Choosing the Right Deployment Models and Migration Framework
You must select a cloud deployment model that fits your business needs. Let’s understand their role one by one.
- Public Cloud: Resources are shared among multiple customers in this cloud model. If your goals revolve around cost reduction and scalability, then the public cloud can be your choice. Migrating to this cloud environment is relatively more straightforward as most cloud providers have standard tools that help you automate much of the migration process. The best part is that you can leverage advanced cloud solutions like AI, ML, and analytics without heavy investments.
- Private Cloud: These clouds are designed for a single organization or individual. They are best for handling sensitive workloads and providing extra privacy. However, there is a catch. You must prepare your environment according to private cloud providers’ specific needs and policies. While the process can be complicated and time-consuming, it will allow you to expand your customization capabilities and enjoy greater flexibility.
- Multi-Cloud: If vendor lock-in is a concern, consider solving it with a multi-cloud model! In this environment, multiple providers provide services to boost flexibility. You can leverage the best services and look forward to optimizing costs and performance. However, multi-cloud migration is complex; you must manage multiple platforms and services. However, it will easily cater to diverse needs.
- Hybrid Cloud: A hybrid cloud lets you enjoy the benefits of both public and private clouds. This means you get access to secure environments and flexibility. The best part is that migration to these environments is simple and ideal for phased migration. This helps you reduce migration-related risks and ensure business continuity.
Now that you know the different cloud deployment models, it is time to understand the 7Rs of cloud migration. They will help you find the best fit for your business.
Further Reading
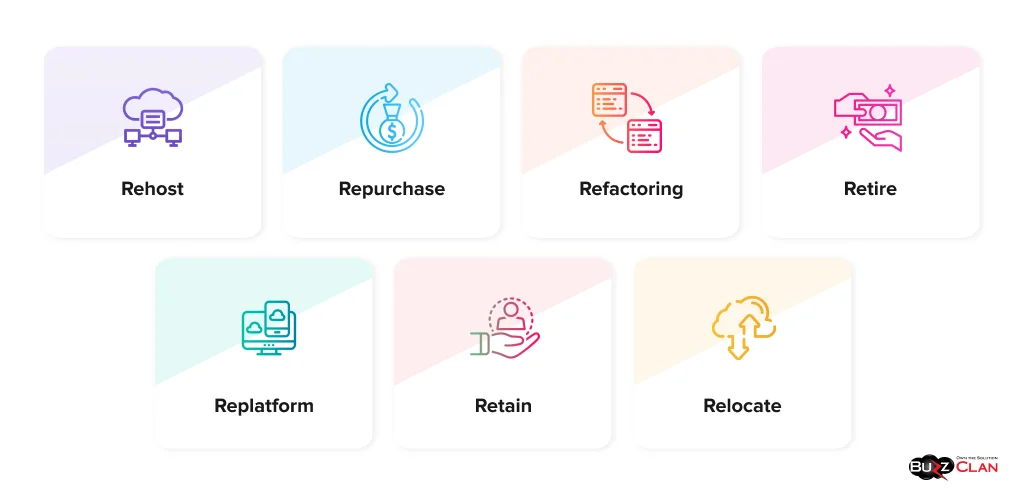
7 Rs of Cloud Migration – Key Approaches
The 7 Rs framework helps you solidify your migration strategy per specific business and technical requirements.
- Rehost (Lift and Shift): This approach moves applications to the cloud with zero modifications. It is essential if you are short on time and have a tight budget.
- Replatform (Lift, Tinker, and Shift): Slight changes are made to the applications to improve performance and fully utilize cloud features.
- Refactoring (Re-Architect): This approach involves tailoring applications per the cloud using functionalities like microservices and serverless computing.
- Repurchase: You replace an existing application with a cloud solution to reduce your maintenance burden and make the most of the cloud.
- Retire: No longer needed; applications are eliminated to cut costs and storage.
- Retain: Some applications are kept on-premise due to security issues or technical constraints.
- Relocate: This approach moves the entire system to the cloud without redesigning it. It is ideal for dealing with specific infrastructures.
Further Reading
How To Deal With Challenges In Cloud Migration?
Cloud migration is not free of challenges. However, you can address these issues and ensure a smoother transition.
Dealing With Legacy Systems
Many organizations still rely on outdated systems and may not have the needed compatibility with cloud environments. This makes cloud migration a time-consuming and expensive process. To ensure you don’t face these issues, conduct an in-depth analysis of your legacy systems and see if they should be replaced, refactored, or rehosted. Also, you must use modernization strategies and cloud-native solutions to eliminate compatibility issues.
Maintaining Data Integrity During Migration
When you transfer large data volumes, you need to take special care to maintain their integrity and accuracy. This is especially essential when taking initiatives to minimize downtime during the process. Thus, it is a must to conduct migration in pages and use secure and high-performance tools. They will help you maintain top-notch data accuracy before and after migration. Moreover, they will also help you implement backup plans seamlessly and avoid data losses.
Dealing With Downtime
If you have not planned your cloud migration well, it can lead to interruptions and poor user experience. No customer wishes to deal with a company that doesn’t provide 24/7 services and support. To prevent these issues from becoming a menace, ensure you have a migration plan that considers breakdowns and allows room for real-time monitoring.
Managing Costs
Be ready for a cost surge if you are not utilizing your resources well. Unexpected requirements or issues can also add to your workload. Thus, it is best to use cloud cost management tools and closely monitor your usage. This will help you better align your cloud needs.
Addressing Skill Gaps
You cannot expect your team to be experts in cloud operations. If you do not offer adequate training support, migration efforts can be delayed, and misconfigurations can occur. Thus, training should be introduced beforehand, allowing them to adapt to the changes gradually. To be on the winning end, partner with consultants to bridge the gap.
Vendor Lock-In Issues
Being dependent on a single cloud provider can lead to limited flexibility and make it difficult to switch providers in the future. To avoid these issues, you must follow a multi or hybrid approach. They will help you leverage the best of both worlds and ensure top-notch cloud security and performance.
Cloud Migration Fundamentals
Each cloud service plays a crucial role in the migration journey. Let’s understand them.
IaaS (Infrastructure as a Service)
IaaS helps you replicate your on-premise infrastructure in the cloud. You can quickly shift your workloads while completely controlling your operating systems. The best part is that you can manage resource scaling during and after migration and customize configurations. This, in turn, helps you reduce complexities and ensure a smoother transition to the cloud.
PaaS (Platform as a Service)
PaaS helps you streamline modernizing your legacy application or creating new software. Since you get access to pre-built tools and middleware, you can significantly reduce the time and effort required for development and testing.
SaaS (Software as a Service)
You know that SaaS helps you use software applications without the hassle of managing them. Consider replacing your on-premise solutions with SaaS solutions during cloud migration. The reason? You can look forward to seamless updates and enhanced user experience. It will also help you cut costs and improve efficiency as these tools help you leverage the best of both worlds.
Cloud Migration Tools
Here is a detailed comparison of cloud migration tools that your business must have.
| Feature | AWS Migration Hub | Azure Migrate | Google Cloud Migrate | Carbonite Migrate | CloudEndure Migration | VMware HCX |
|---|---|---|---|---|---|---|
| Provider | AWS | Microsoft Azure | Google Cloud | OpenText (Carbonite) | AWS (acquired) | Google Cloud |
| Primary Use Case | Multi-service cloud migration tracking | Workload assessment & migration to Azure | VM migration to Google Cloud | Minimal downtime server migrations | Automated lift-and-shift migrations | Hybrid cloud migration |
| Supported Workloads | Servers, databases, applications | Virtual machines, databases, web apps | VMs, databases, apps | Physical, virtual, cloud servers | VMs, databases, apps | VMware-based workloads |
| Cloud Compatibility | AWS | Azure | Google Cloud | Multi-cloud (AWS, Azure, GCP) | AWS | Multi-cloud (VMware Cloud, AWS, Azure) |
| Migration Type | Lift-and-shift, re-platform | Lift-and-shift, modernization | Lift-and-shift | Lift-and-shift | Lift-and-shift | Lift-and-shift, live migrations |
| Automation Capabilities | Limited automation | Automated discovery, dependency mapping | Automated workload migration | Automated reconfiguration | Continuous data replication | Live migration with minimal downtime |
| Downtime Minimization | Moderate | Minimal | Minimal | Near-zero | Near-zero | Minimal |
| Complexity | Medium | Medium | Medium | High | Low | Medium |
| Security Features | AWS IAM, encryption, compliance support | Azure Security Center integration | Google IAM, encryption, compliance support | Encryption, integrity checks | Secure replication, IAM integration | Network security policies, encryption |
| Cost | Free (AWS service charges apply) | Free (Azure service charges apply) | Free (GCP service charges apply) | Paid | Free (AWS service charges apply) | Paid |
| Best For | AWS-centric migrations | Enterprises moving to Azure | Businesses migrating to GCP | Businesses requiring multi-cloud flexibility | Large-scale AWS migrations | VMware-based workloads |
Phases in Cloud Migration
All the phases in cloud migration play a crucial role. Migration is done in phases to ensure no service lags and downtime. This way, you can stay on the same page as customers and offer the best services pre and post-migration. Let’s understand what happens in the different phases of migration.
- Assessment and Planning: This phase checks if your organization is ready for cloud adoption. Here, you need to identify challenges and lay down the business goals you wish to achieve from cloud migration.
- Develop A Migration Plan: In this step, you must create a detailed migration plan and select a migration approach based on your analysis.
- Execute The Strategy: The process is executed full-throttle in this phase, depending on your chosen migration strategy.
- Optimization Post-Migration: This phase ensures that your applications and infrastructure are in perfect condition and work as efficiently as before migration. You will also need to check your costs and address the issues that come post-migration.
- Ongoing Monitoring: This phase ensures the long-term success of cloud migration. It requires consistency, staying updated on the latest trends, from security to performance monitoring, and maximizing cloud capabilities. Experts can help devise a strategy for this phase.
Future-Proof Cloud Migration with BuzzClan’s Enterprise-Grade Expertise
Building a cloud migration strategy is not easy. However, you need not worry, as BuzzClan is here to help. We follow a transparent communication process that lets you stay on the same page and make better decisions. This has helped us maintain a solid competitive edge with our cloud solutions. We understand that monitoring and observability are the backbones of high-performing cloud environments. Thus, we help you implement real-time monitoring tools for smooth operations and faster resolutions. We also help you implement centralized logging and AI-driven anomaly detection. This way, you can maintain sound infrastructure health and enhance the cloud’s resilience, scalability, and operational efficiency. Here is what you can expect:
- The promise of 99.99% uptime
- Reduced cloud spending by 40%
- Improved data quality and reduced deployment risks
- Predictive scaling capabilities
- ROI-focused implementation
- Reduce deployment time by up to 60%
- Simplified cloud architecture and design
- Automated compliance and monitoring
- 24/7 monitoring and logging
Conclusion
Cloud migration isn’t just a technical transition—it’s a strategic business transformation that unlocks unprecedented opportunities for growth, innovation, and competitive advantage. By developing a comprehensive migration strategy based on the 7 Rs framework, selecting the right deployment model, and partnering with experts who understand your unique business challenges, you can confidently navigate the complexities of cloud adoption.
Remember that successful cloud migration requires more than just technical expertise. It demands a holistic approach that addresses data security, employee training, cost management, and continuous optimization. Organizations that embrace this mindset consistently outperform their competitors, achieving up to 40% reduction in IT costs, 99.99% uptime, and significantly enhanced operational agility.
As cloud technologies continue to evolve with AI integration, enhanced security capabilities, and specialized industry solutions, your migration strategy should remain flexible and forward-looking. Start by thoroughly assessing your current infrastructure, clearly defining your business objectives, and implementing a phased approach that minimizes disruption while maximizing value.
Whether considering a public, private, hybrid, or multi-cloud environment, aligning your cloud strategy with your long-term business goals is key. With proper planning, expert guidance, and a commitment to continuous improvement, your organization can join the ranks of cloud-powered businesses, redefining industries and setting new standards for innovation and efficiency.
The cloud journey doesn’t end with migration—it’s just the beginning of a new era of digital possibilities for your business. Take the first step today and position your organization for sustainable success in an increasingly cloud-centric world.
FAQs

Get In Touch
Follow Us
Table of Contents
- Key Benefits of Cloud Migration
- Core Components of a Cloud Migration Strategy
- Selecting the Right Cloud Provider
- Choosing the Right Deployment Models and Migration Framework
- 7 Rs of Cloud Migration – Key Approaches
- How To Deal With Challenges In Cloud Migration?
- Cloud Migration Fundamentals
- Cloud Migration Tools
- Phases in Cloud Migration
- Future-Proof Cloud Migration with BuzzClan’s Enterprise-Grade Expertise
- Conclusion
- FAQs