How Does a VPN Work? A Technical Deep Dive
Ramesh Rastogi
Nov 13, 2024
Network security has been a matter of concern since the birth of the Internet. Not securing one’s network and data has led to confidential data leakage, user identity exposure, misuse of credentials (ATM pins and passwords), and much more. The lack of robust security protocols leads cyber criminals to exploit your digital footprints, stealing and misusing your data.
If you don’t hide your digital footprints (the trail of data you leave using the Internet), you are at a greater risk of cybercrimes. Increased cyber attack vulnerability, high risks of disrupting privacy, and cyberbullying are some potential threats a user can suffer when not hiding their digital footprints. So, hiding your digital footprints is a necessity.
Over the years, many measures have been taken to eradicate security concerns, but VPN has emerged as one of the best security measures for protecting networks, data, and user identity. 93% of organizations currently use VPN worldwide because it can hide digital footprints and ensure anonymity on the Internet for safety.
This blog will explore how VPNs work, how they help users, how to host one, and how to choose the best one for your needs. But first, let’s understand what a VPN is.
What is a VPN?
A VPN is a virtual private network that users connect to ensure privacy, security, and anonymity. It encrypts data using VPN protocols and hides a user’s online presence, personal information, physical location, and other valuable data.
A VPN creates a safe tunnel through which your internet activity and data become gibberish, i.e., encrypted. This tunnel doesn’t allow hackers or cybercriminals to breach the network and also disallows ISPs, the government, or advertisers to watch or monitor your internet activities. If the data gets breached, individuals or businesses risk ransomware-as-a-service attacks, phishing, and DDoS attacks, illuminating the importance of VPNs.
Let’s explore how the VPN mechanism works and its importance in business as one of the best online privacy solutions.
How Does a VPN Work?
A VPN secures one’s data through an effective encrypted mechanism. First, a VPN host/client encrypts your data, such as your request, location, and IP address, making it complex gibberish that is nearly impossible to decrypt. Then, it goes to your ISP. Since the request is encrypted, your ISP cannot determine what you are typing to access.
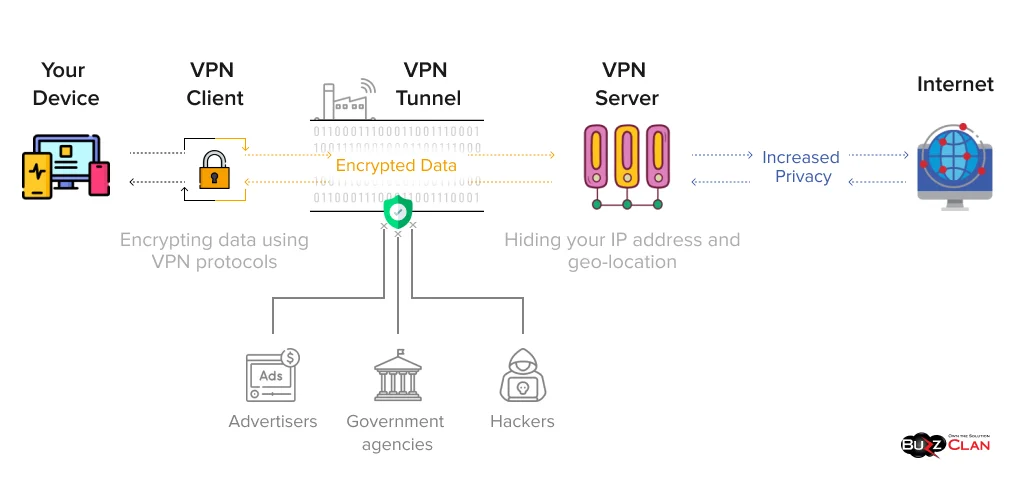
This encrypted data is sent to a private VPN tunnel by your ISP because of the incomprehensible nature of the data. This VPN tunnel is an encrypted and secured tunnel that disallows and restricts anyone from watching or monitoring your activities and data. Following the safe VPN tunnel, your encrypted data reaches the VPN server, where it gets decrypted with the encryption key only it has. From there, it reaches the Internet, sending the response from the requested website back to the connection.
Types of VPN
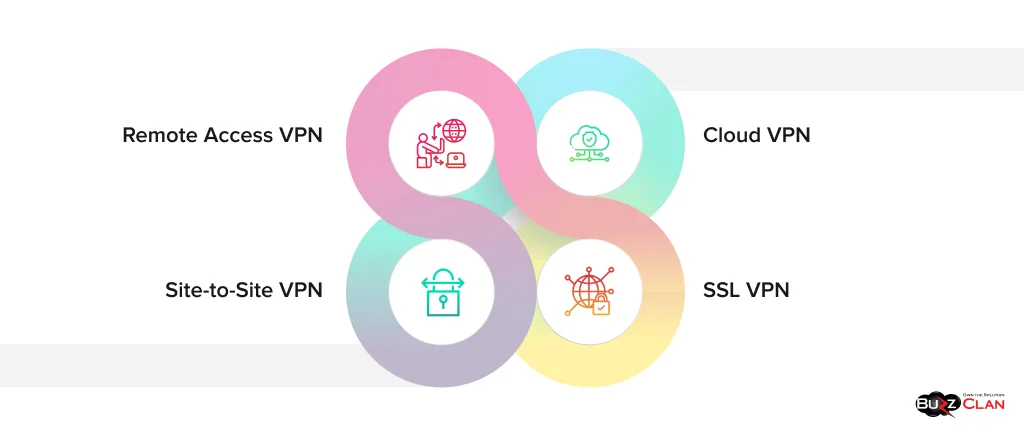
About eight types of VPNs exist, but four are primarily used worldwide. Let’s explore them in detail below and how they help individuals and businesses:
Remote Access VPN
- A remote access VPN allows users to connect to a private or company network via a safe and encrypted tunnel. Users surfing the internet from their locations can access regionally restricted content while hiding their location. Employees who work from home or in remote locations use this VPN to access their company’s files or documents privately. The safe tunnel doesn’t allow anyone to know their location or digital footprints, ensuring an anonymous and confidential route and process. Some companies that offer remote access VPNs are Perimeter 81, NordLayer, and ExpressVPN.
Site-to-Site VPN
- A site-to-site VPN, also known as a router-to-router VPN, connects several company offices, connecting one office location to another. Big companies commonly use it with multiple branches. The data stored in these branches can be accessed interchangeably using site-to-site VPN. For example, an employee can use this VPN to access the documents or files stored at “A” at location “B.” Palo Alto Networks, Cisco, and Fortinet offer site-to-site VPN services.
- Moreover, if the VPN is used to connect the offices of the same company, it is known as an intranet-based VPN. Conversely, when a company uses a site-to-site VPN to connect to another company’s offices, it is said to be an extranet-based VPN.
Cloud VPN
- Cloud VPN is a virtual private network used to connect systems to cloud infrastructure or services. It allows users to maintain a connection with cloud service providers, such as Microsoft Azure, Google Cloud, or AWS. Cloud VPN is also known as hosted VPN or VPNaaS (because it is typically offered as a service). It ensures that the data transmitted from an employee to the cloud database is safe, encrypted, and protected. It uses the same encryption as SSL or IPsec. Besides offering business benefits, such as centralized security management, interconnectivity, and mitigating risks, cloud VPN offers rapid configuration and deployment. AWS, Google Cloud, and Aviatrix are some companies that provide cloud VPN.
SSL VPN
- SSL VPN or secure socket layer VPN allows the user or an employee to access any private or company network. Users can access corporate resources remotely, such as e-mails, files, or documents from their company’s system. This type of VPN ensures a safe tunnel that encrypts the data flowing through the networks. Making sure no unauthorized entities intercept or alter it. SSL VPN or its successor Transport Layer Security (TLS) protocol uses SSL protocol.
- SSL VPN uses a browser rather than a VPN client to safeguard the confidentiality of data and activity. This makes it easy to use and deploy, as no other application/ VPN client needs to be installed on the device. SSL VPN surpasses traditional IPsec VPNs in encryption, as it uses similar encryption methods used in HTTPS. These methods secure online transactions, making them robust and highly secure. Barracuda Networks, Dell SonicWALL, and Juniper Networks offer SSL VPN solutions to organizations aligning with their needs.
Moreover, other types of VPNs, such as PPTP (Point-to-Point Tunneling Protocol), L2TP (Layer 2 Tunneling Protocol), and OpenVPN, satisfy diversified business and individual cybersecurity needs. One such type of VPN is mobile VPN, which is used for mobile devices. They maintain privacy and anonymity while the user switches connections (Wi-Fi to cellular).
Importance of VPNs in Business
VPNs are significant in businesses, from encrypting data to protecting privacy. Because of their enormous benefits, the market for VPNs will reach 350 billion dollars by the year 2032. Here are some reasons why VPNs are so important in the business world.
Encryption
VPN encryption turns your understandable data into inexplicable gibberish, which the ISP, gov., and advertisers cannot decrypt. It can only be read through an encryption key. Without the key, the hacker would take millions of years to crack what the data is about in the event of a brute-force attack. The VPN server has this key, which is used to decrypt the data and information, ensuring safe and secure activity. This encryption helps a business in several ways, such as:
- It saves users from DMCA notices and huge fines if they download torrents.
- Encryption aids in hiding user internet activities from the government if you are found engaging in illegal activities over the internet.
- Advertisers monitor your activity to send ‘personalized’ ads on your devices. VPN allows you to conceal your identity, thus blocking advertisers from using your data.
Anonymity
Anonymity is the state of being anonymous or unknown. A VPN hides one’s online identity from others by masking one’s IP address. IP address is the unique code given to every device on the Internet, like a return address on a handwritten letter. If someone knows your IP address, they can know which websites you surfed, your session duration, and your search history. Masking IP addresses is the cornerstone feature of a VPN. It masks your identity by providing a different IP address or the IP address of the VPN server itself (different from your IP address).
Dynamic and Static IP Addresses: Most VPN services offer dynamic IP addresses, which change whenever the user connects to the VPN. Some VPNs provide static IP addresses, which are helpful to business applications that need a fixed/single address to function. IP address masking helps businesses prevent online tracking, test websites from different locations, and protect data.
Location Spoofing
Location spoofing is changing a device’s location to another location using technology. VPN offers very effective location spoofing. VPNs allow users to switch countries, whichever they prefer, without changing their physical location. With VPNs, users can mask their IP address, leading to manipulation of their geo-location, which helps confuse outsiders to identify their actual location.
Another great benefit of location spoofing is accessing regionally restrictive content. Some websites or content are not available in some regions/countries. A VPN helps access websites, content, and services inaccessible in one’s country. This allows businesses to bypass geographical restrictions, access global markets, and improve online anonymity. Moreover, standard connections use local servers in the country to identify your location. This restricts people from accessing international content at home and while traveling.
Easier Administration
With flexible VPN software tools, businesses can easily add more users or groups to the network. This flexibility allows companies to expand their network footprints without needing extra network configurations, thus facilitating easier business administration. Additionally, VPNs align with cybersecurity trends that help advance encryption protocols, avoid bandwidth throttling, and centralize resource management.
Privacy
With VPN’s encryption and authentication tools, employees and users can ensure the privacy of their network. Their data goes through the safe tunnel made by the VPN host that goes to the VPN server in an encrypted way. Due to this, the ISP cannot determine what the user is browsing. Only its VPN knows that when they log information into their servers. This ensures the privacy of internet users, as well as their whereabouts, browsed websites, and content. In businesses, VPN ensures protection against data breaches, remote work security, reduced surveillance, and control over access.
How to Choose a VPN?
Choosing a good and secure VPN is a must for businesses or individuals. Many VPNs don’t provide several key factors, such as a kill switch, transparency over logging activities, specific blockades, etc. These factors may arise as a matter of concern and require extra caution to ensure the concealment of your identity and data.
So, consider the following ways to choose the best VPN according to your requirements and needs.
Security Measures
- No-logs Policy: Many free-to-use/ paid VPNs log users’ internet activities. One must opt for a VPN with a no-logs policy, which helps users leave no trace behind and leads to zero tracking.
- Kill Switch: Kill Switch is a feature built into many high-quality VPN service providers. It automatically disconnects your internet connection if the VPN connection drops, helping to prevent data leaks.
- Using Robust Encryption: A good VPN uses higher and more robust encryption standards rather than weaker protocols like PPTP. One such protocol is AES-256, which top VPN providers like NordVPN and Surfshark use.
Compatibility
- Device Support: Users must check whether the VPN they have connected to or subscribed to connects to their systems. For streamlined operations, a VPN should support Windows, iOS, MacOS, and Android.
- Multi-Device Connectivity: When buying a VPN subscription, check how many devices you can connect to simultaneously and whether it offers browser extensions.
Performance & Speed
- Unlimited Bandwidth: Unlimited bandwidth prevents a VPN user from being throttled by its ISP during peak times. It also prevents slow website loading times, buffering, and lags in content streaming and games.
- Diverse Server Locations: A VPN with several server locations increases its speed and access to geo-restricted content.
Reputation
Potential VPN users should read personal and professional reviews of the selected VPN to get a good overview. This gives them a clear idea of its functionalities and features. Since many fake VPNs are in the market, doing a thorough analysis before choosing a VPN is a wise decision.
Pricing and Planning
The selected VPN should offer value for money. Sometimes, some providers provide the required features at lower prices in extended subscription plans. Moreover, a money-back guarantee offers VPN testing without commitment to the services.
Other Important Features
- Split Tunneling: In split tunneling, users can choose which app should use a cellular connection and which should connect to a VPN.
- Ad Blocking and Shared IP Addresses: The ad-blocking feature in a VPN blocks malware that can infect your system and data. Moreover, adding a layer of protection is always a good idea. Shared IP addresses make your online presence amongst the other anonymously surfing internet users, shielding protection.
- Customer support: Whenever a VPN server goes down or something interrupts your VPN connection, helpful customer service always helps. So, choosing a VPN that provides 24/7 effective customer support is a prerequisite for a streamlined network connection.
Steps to Host a VPN
Hosting a VPN means setting up the necessary infrastructure for accessing VPN services. VPN hosting helps users achieve enhanced security and privacy, as the user doesn’t outsource VPN services from third parties. Instead, they build and set up their own VPN at home, in the office, or elsewhere.
The steps to host a VPN are as follows:
Deciding your Hosting Option
Hosting needs a device or third-party outsourced device to establish the VPN server. Here’s how you can host a VPN on these options:
Cloud VPS
A VPS is a virtual private server. Many cloud providers, such as AWS, DigitalOcean, and Google Cloud, offer VPS services for hosting your VPN by installing VPN software.
Home Router
You can easily install the VPN software on your home Wi-Fi router if it supports it. Hosting a VPN on a home router can facilitate remote access, but it isn’t best for external use while you are at home.
VPN Router
A VPN router is a type that already has a VPN installed. It gives smooth access to all the VPN capabilities without installing the software and doing additional manwork. VPN providers like
ExpressVPN offer VPN routers.
Selecting a VPN Protocol
Select a VPN protocol according to the individual or organizational requirements, considering the security and privacy offered by different VPN protocols.
PPTP
PPTP/L2TP are some of the oldest and most widespread VPN protocols. Windows PC has this in-build protocol in it. They use weaker encryption standards such as (MPPE) but are comparatively easy to set up and work best for legacy systems.
OpenVPN
OpenVPN is the most commonly used VPN protocol, enhancing privacy and security. In its OpenVPN library, OpenVPN provides the 256-bit AES encryption protocol. This protocol supports PFS (Perfect Forward Secrecy), which generates new keys for every session, so if a session gets compromised or hacked, then other sessions’ data doesn’t get affected.
WireGuard
WireGuard is a new-age VPN protocol. It offers strong cryptography and high performance over its predecessors, OpenVPN and IPSec. The WireGuard protocol facilitates cross-platform compatibility, easy configuration, and simplicity.
Setting up your VPN Server
We will use WireGuard Server because of its simplicity, high performance, and security.
- Update System
sudo apt update
sudo apt upgrade -y
- Install WireGuard
sudo apt install wireguard
- Enable IP Forwarding
sudo echo "net.ipv4.ip_forward = 1" »> /etc/sysctl.conf
sudo syscti -p
Configure WireGuard
- Generate Server Keys
ug genkey | sudo tee /etc/wireguard/private.key
sudo chmod 600 /etc/wireguard/private.key
sudo cat /etc/wireguard/private.key | wg pubkey | sudo tee /etc/wireguard/public.key
- Create Server Configuration
sudo nano /etc/wireguard/wg0.conf
Add the following:
PrivateKey = < server-private-key >
Address = 10.0.0.1/24
ListenPort = 51820
PostUp = iptables -A FORWARD -i wg0 -j ACCEPT;
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i wg0 -j ACCEPT;
iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
Client Configuration
- Generate Client Keys
ug genkey | tee client-private.key
cat client-private.key | me pubkey › client-public.key
- Add Client to Server Config
Add to wg0.conf:
Publickey - ‹client-public-key>
AllowedIPs - 10.0.0.2/32
- Create Client Configuration
Privatekey = ‹client-private-key>
Address = 10.0.0.2/32
DNS = 1.1.1.1
[Peer]Publickey = (server-public-key>
Endpoint =
AllowedIPs = 0.0.0.0/0
PersistentKeepalive = 25
Start the VPN Server
udo systemctl enable wg-quick@wg0
sudo systemctl start wg-quick@wg0
Security Considerations
- Firewall Configuration
sudo ufw allow 51820/udp
sudo ufw enable
- Regular Updates
sudo apt update && sudo apt upgrade -y
Testing & Maintenance of the Hosted VPN
After configuration and security considerations, connect the devices you want to enjoy VPN facilities. This can be done by using the configuration files generated during setup. Then, test whether the VPN is working correctly using the below-mentioned tests (later in the blog), such as the DNS leak and SSL/LTS tests.
Moreover, to check whether the VPN has been working correctly and for its prolonged maintenance, monitor its performance and log, and regularly update it to streamline tasks.
Apart from offering high security and more control over your internet activities, running your own VPN server has limited features, requires a time commitment, and requires a prior check of its legality. VPN hosting will always have a definite or fluctuating cost, depending on the extra device and the cloud service you use. So, according to your business needs and requirements, choose whether you need VPN hosting or a regular VPN from third parties.
VPN vs. Firewall
You have probably heard the term firewall while dealing with antiviruses, internet and cloud security, etc. VPN and firewall are subsets of network security technologies but aren’t the same in functionality and purpose. Let’s look at how VPNs and firewalls differ, how they work, and their use cases.
| Feature | VPN (Virtual Private Network) | Firewall |
|---|---|---|
| Function | Creates a private, secure tunnel over the internet | Acts as a security guard or barrier for your network |
| Purpose | Keeps your internet activity private and secure | Protects from unwanted visitors (hackers, viruses) |
| How it works | Encrypts data to keep it unreadable if intercepted | Monitors and blocks/allows internet traffic |
| User’s location | You can change or hide your actual location (appears in a different place) | It doesn’t affect your location; it only monitors traffic |
| Traffic Control | It doesn’t control traffic, only encrypts it | Controls what data goes in and out of your network |
| Use Case | People needing online privacy or secure remote work access | Everyone needs protection from threats on the internet |
While VPNs and firewalls differ in many ways, they are similar in some facets, such as network segmentation, integration with other security solutions, and compliance support.
Testing and Maintaining VPN
Testing and maintenance of a VPN is crucial as it helps:
- Catch problems before they become disasters or significant.
- Ensuring the VPN speed is optimal
- Checking and confirming the privacy
To test the VPN, the user must know some tests and tools to run those tests. Here are some of the critical tests and tools they require.
The Basic IP Test: This tool helps you check whether the VPN hides your IP addresses. WhatIsMyIP.com, IPleak.net, and IPX.ac are some essential IP test tools.
DNS Leak Testing: This testing checks whether the VPN securely protects the domain name system (DNS) from the internet service provider or third parties. It helps check an integral part of cybersecurity services. Users can do this testing on DNSLeakTest.com and IPleak.net.
Speed Test: Speed plays a major role in determining a VPN’s performance. Speedtest.net, Fast.com, and Google Speed Test can help you test your VPN’s speed. During the speed test, one must check the download, upload, ping, and connection stability.
SSL/TLS Test: SSL (secure sockets layer) and TLS (transport layer security) are protocols that help computers communicate with each other over the Internet. SSL/TLS test confirms whether the VPN’s connection encryption is safe and secure. Many tools that can do this test are Domsignal, Wormly web server tester, HowsMySSL, etc.
Conclusion
Opting for VPNs is considered an excellent choice. VPNs have immense benefits that help users and businesses remain anonymous and carry out their internet activities without leaving digital footprints. A VPN should be carefully chosen according to your business needs because choosing a mismatched VPN provider can cause cybersecurity concerns.
Moreover, your VPN must be tested and maintained regularly to ensure the security of your data and business. VPN has been a significant cornerstone in securing identities, IP addresses, and sensitive information. With emerging technologies, many advanced successors of VPNs have come into the network security market, improving network security strategies. Zero Trust Network Access (ZTNA), Secure Access Service Edge (SASE), and Next-Generation Firewalls (NGFW) are some examples of the same. One must consider their advantages and limitations before opting for a shielded network and security in business.
FAQs

Get In Touch

