A Quick Guide to Cyber Security
Sunita Singhania
Dec 22, 2023
What is Cybersecurity?
Cybersecurity protects computer systems, networks, and data from digital attacks, damage, or unauthorized access. It's a multidisciplinary field that touches on various aspects of technology, information science, and risk management to safeguard digital assets.
Why is Cybersecurity Important?

- Data Protection: We live in an age where data is the new gold. From personal information to financial records, everything is digital. A cybersecurity breach can lead to unauthorized access to sensitive data.
- Financial Loss: Cyber attacks can have a devastating impact on businesses. The average data breach cost continually rises, running into millions of dollars.
- National Security: Government agencies, infrastructure, and even elections can be disrupted through cyber attacks. Cybersecurity is crucial for national security.
- Consumer Trust: For businesses, a single breach can severely damage the trust and reputation built over years.
Relevance in Today's Digital Age
The digital age has brought unprecedented convenience and capabilities, but it's a double-edged sword. As businesses and individuals become more reliant on digital platforms, the importance of cybersecurity has increased exponentially. The COVID-19 pandemic further accelerated the adoption of remote work, online transactions, and digital communications, broadening the threat landscape.
Brief on the Threat Landscape
- Increasing Sophistication: Cybercriminals are getting more sophisticated, employing advanced techniques like machine learning to enhance attacks.
- Diverse Targets: No one is immune. Everyone is a potential target, from individuals and small businesses to multinational corporations and governments.
- Rapid Evolution: New threats are emerging at an alarming rate, making it crucial for cybersecurity measures to evolve accordingly.
Connection to IT Services and Consultation
In today's interconnected world, cybersecurity isn't just an "IT issue"—it's a business imperative. IT services and consultation are pivotal in shaping an organization's cybersecurity posture. Whether implementing the latest firewall technology, managing network vulnerabilities, or ensuring compliance with industry regulations, professional IT consultation can provide the expertise and resources to fortify your digital defenses.
Cybersecurity isn't just about installing antivirus software and hoping for the best. It's a complex, ongoing effort that requires strategic planning, expert guidance, and continual monitoring. To delve deeper into how you can secure your digital landscape, explore our cluster of detailed analyses, security technologies, and best practices.
Cyber Security Threats
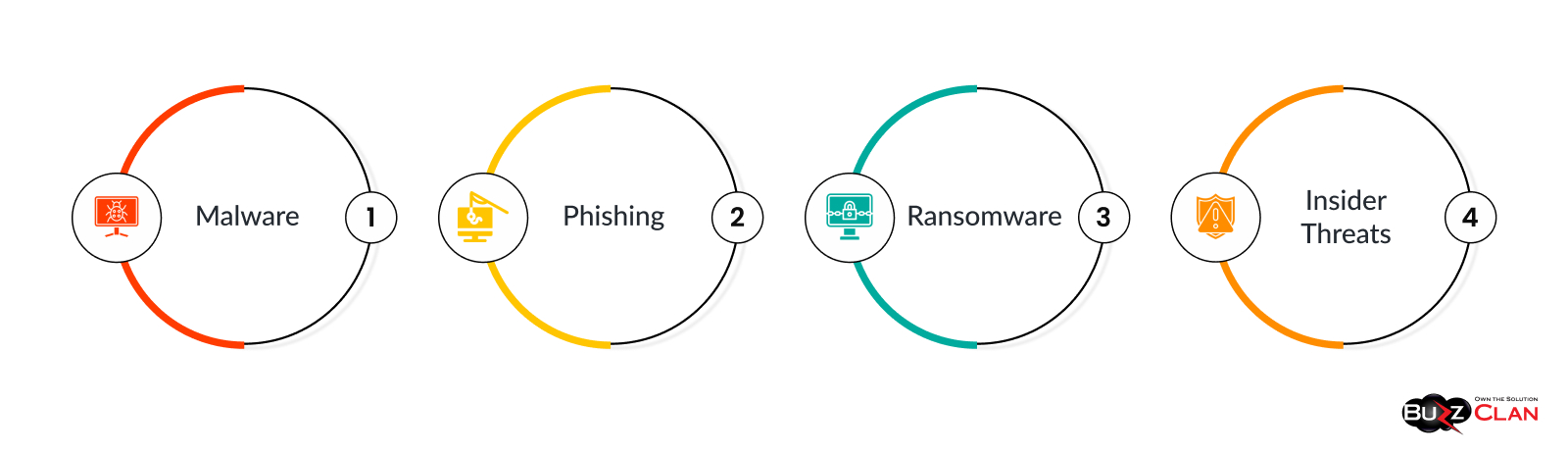
Malware
- What It Is: Malware, short for "malicious software," is designed to harm or exploit a computer, server, client, or computer network. Examples include viruses, worms, and Trojans.
- How It Spreads: Often via email attachments, malicious downloads, or infected websites.
- Protection: Use antivirus software, keep all systems updated, and educate employees on the dangers of downloading from suspicious sources.
Phishing
- What It Is: Phishing is the fraudulent practice of sending emails that appear to be from reputable companies to induce individuals to reveal personal information, such as passwords and credit card numbers.
- How It Spreads: Primarily through email, although other forms of communication like SMS can also be used.
- Protection: Email filtering solutions, employee training to recognize phishing attempts, and multi-factor authentication.
Ransomware
- What It Is: Ransomware is malware that encrypts a user's files and demands payment for their release.
- How It Spreads: Through phishing emails, malicious advertisements, or infected websites.
- Protection: Regular backups, updated security software, and strong, unique passwords.
Insider Threats
- What It Is: Insider threats come from individuals within the organization, such as employees, former employees, or contractors with inside information concerning security practices.
- How It Spreads: Through misuse of credentials, data theft, or intentional sabotage.
- Protection: Role-based access controls, regular audits, and employee monitoring.
Understanding your threats is the first step in building a robust cybersecurity strategy. From malware to insider threats, the landscape is complex but not insurmountable. For a more in-depth look at these threats, follow the links to our detailed analyses.
Essential Components of Cyber Security
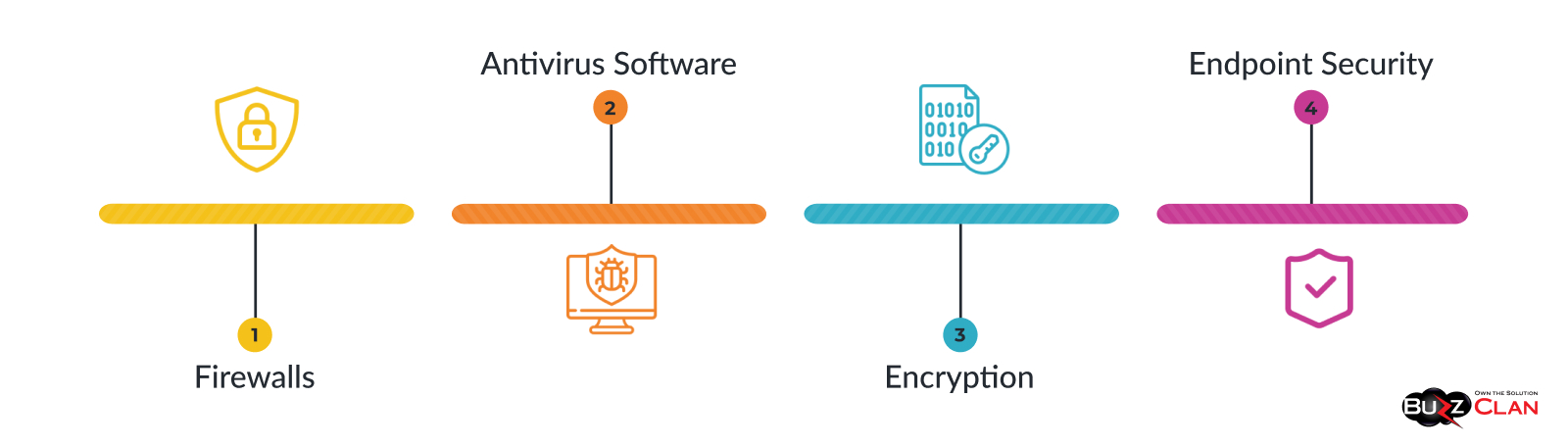
Firewalls
What They Are: Think of firewalls as digital bouncers. They stand between your internal network and incoming traffic from external sources (such as the internet), and determine whether or not to allow the traffic through based on a set of defined rules.
Importance: Firewalls are crucial for controlling traffic flow, limiting network vulnerabilities, and preventing unauthorized access to networked resources.
Antivirus Software
What It Is: Antivirus software scans your computer and network for known types of malware and removes or quarantines them.
Importance: This is the first line of defense against malware attacks and is essential for any individual or organization using digital systems.
Encryption
What It Is: Encryption converts data into a code to prevent unauthorized access.
Importance: It's the digital equivalent of a safe. Encryption is essential for protecting sensitive data, especially during transmission over unsecured networks like the Internet.
Endpoint Security
What It Is: Endpoint security ensures that all user devices, like computers, mobile devices, and network servers, are secure.
Importance: As the points of entry to your network, these devices are potential weak links that attackers could exploit.
The components of cybersecurity are like the instruments in an orchestra—each plays a vital role, but it's only when they work together that you get a harmonious, secure environment. For a detailed explanation of how these components contribute to your overall cybersecurity strategy, explore the in-depth cluster links provided.
Benefits of CyberSecurity
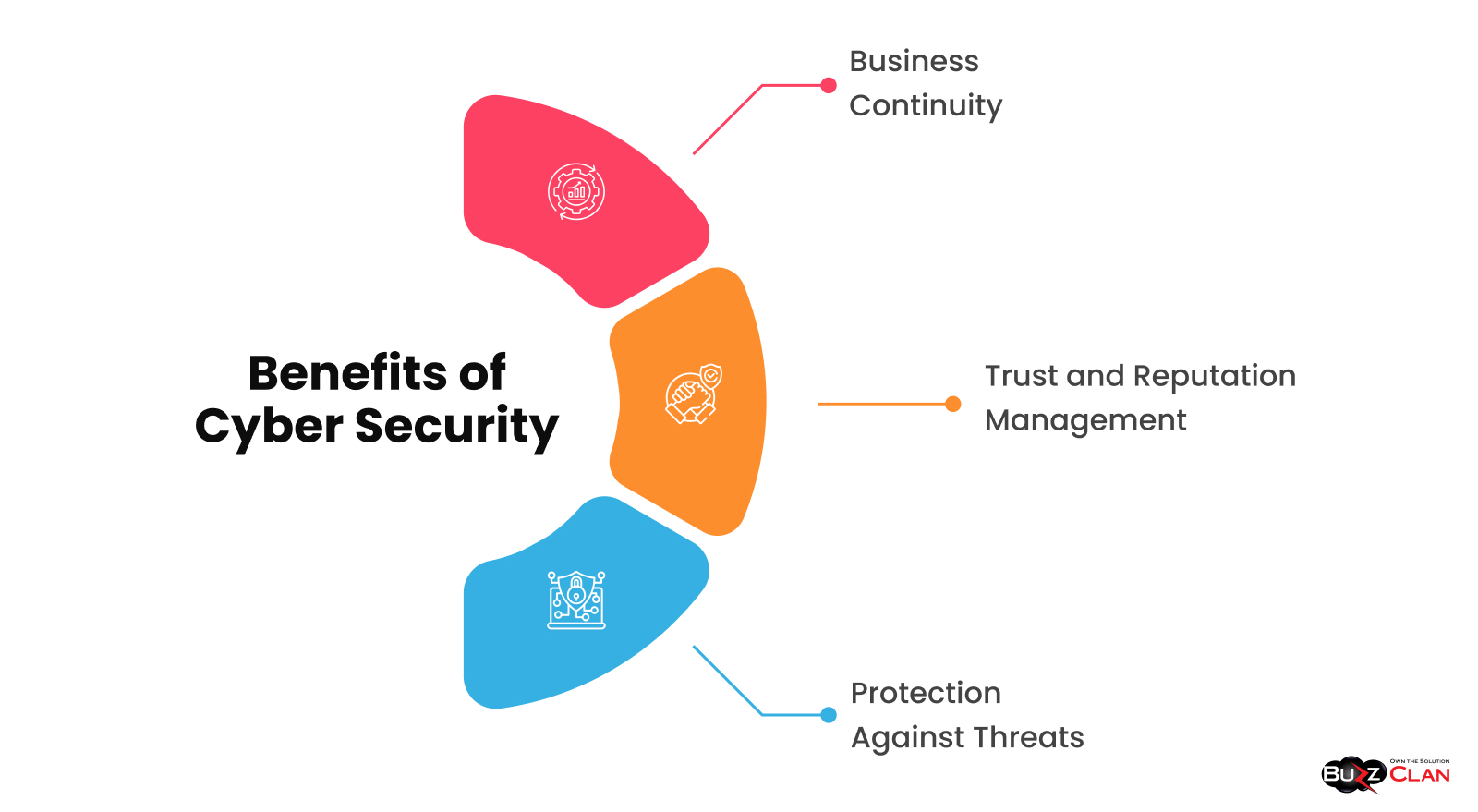
Protection Against Threats
What It Means: A robust cybersecurity framework is your digital fortress. It prevents unauthorized access, protects data, and thwarts attempts at disrupting or damaging computer-based systems.
Impact: By protecting against threats like malware, ransomware, and phishing, cybersecurity measures save businesses from financial losses and help maintain uninterrupted operations.
Business Continuity
What It Means: Cybersecurity safeguards the ability of an organization to continue its core business operations uninterrupted, even in the face of cyber threats.
Impact: Reduced downtime, maintained customer trust and sustained revenue streams. In short, it is business as usual—even when cybercriminals are knocking at your digital door.
Trust and Reputation Management
What It Means: Let's face it; nobody wants to do business with an organization known for security lapses. A robust cybersecurity posture protects your data and preserves your reputation.
Impact: Customer trust is hard to earn and easy to lose. Cybersecurity measures ensure you're seen as a reliable partner, thus enhancing your market position.
The benefits of cybersecurity extend beyond just keeping the bad guys out; they also play a vital role in your organization's longevity and reputation. As the saying goes, "An ounce of prevention is worth a pound of cure." Investing in cybersecurity is not an expense but an essential long-term investment.
Dangerous Cybersecurity Myths
Debunking Common Misconceptions
"We're Too Small to Be Targeted"
Reality: Cybercriminals often see smaller organizations as low-hanging fruit. Lack of resources and weaker security measures make them easier targets.
"Our Employees Can Spot a Phishing Email"
Reality: Phishing tactics are becoming increasingly sophisticated, making it difficult for savvy individuals to identify them.
"Antivirus Software Is All We Need"
Reality: While antivirus is crucial, it's just one layer in a multi-layered security approach. Firewalls, employee training, and regular updates are also necessary.
Realities of the Cyber Landscape
- Constantly Evolving Threats: The threat landscape is not static; it evolves rapidly. What worked yesterday might need to be more today.
- Insider Threats: Not all dangers come from the outside; sometimes, the threat is from within your organization.
- Compliance ≠ Security: Just because you've checked all the regulatory boxes doesn't mean you're secure. Compliance is a minimum standard, not a ceiling.
Myths and misconceptions in cybersecurity can be more dangerous than the threats they purport to address. They give a false sense of security and leave organizations vulnerable to attacks. So, next time someone in the office says, "We don't need to worry about cybersecurity," maybe send them our way for a reality check.
Key Cybersecurity Technologies and Best Practices
Regular Updates and Patch Management
What It Is: Keeping software and systems updated with the latest security patches and updates.
Why It's Important: Outdated software is a prime target for cybercriminals, as they often contain known vulnerabilities that can be easily exploited.
Multi-Factor Authentication (MFA)
What It Is: Using multiple methods—like a password and a mobile code—to verify a user's identity.
Why It's Important: MFA adds a layer of security, making it difficult for unauthorized users to gain access.
Employee Training and Awareness
What It Is: Educating employees about the importance of cybersecurity and how to recognize and prevent potential threats.
Why It's Important: Employees are often the weakest link in cybersecurity. A well-informed workforce can be your first line of defense.
Secure Backup Solutions
What It Is: Regularly backing up essential data to a secure, remote location.
Why It's Important: In a data loss or ransomware attack, secure backups allow you to restore your systems with minimal disruption.
The key to robust cybersecurity isn't just investing in the latest technologies and implementing a culture of security awareness and best practices. Think of it as a cybersecurity diet; it's not about the occasional detox but consistent, healthy choices.
Compliance, Ethical, and Legal Dimensions
GDPR, HIPAA, PCI-DSS?
What They Are: These are regulatory frameworks designed to protect personal and financial data. GDPR (General Data Protection Regulation) is European, HIPAA (Health Insurance Portability and Accountability Act) is American, and PCI-DSS (Payment Card Industry Data Security Standard) is global.
Why They Matter: Failure to comply can result in hefty fines, legal consequences, and reputational damage.
Ethical Considerations
What It Is: Ethical considerations go beyond legal requirements and involve doing what’s right, such as respecting customer data and using it responsibly.
Why It's Important: Ethical lapses can lead to loss of customer trust and tarnish your brand's reputation.
Legal Regulations
What They Are: These laws govern how data should be stored, processed, and protected. This could include data retention laws, reporting requirements for data breaches, and more.
Why They Matter: Ignorance of the law is no excuse. Non-compliance can result in legal action and financial penalties.
Navigating the labyrinthine world of compliance and legal regulations can be daunting, but it's crucial for any organization serious about cybersecurity. It’s not just about avoiding penalties; it’s about doing the right thing, ethically and legally. Remember, compliance is not a one-off task but an ongoing commitment.
Use Cases, Success Stories, and Case Studies in Cyber Security
Success Stories
What They Are: These are real-world examples of a robust cybersecurity framework that successfully thwarted attacks or minimized damage.
Why They Matter: Success stories serve as educational tools and confidence boosters, showing that effective cybersecurity is achievable.
Lessons Learned from Major Breaches
What They Are: These are analyses of high-profile cyber incidents, dissecting what went wrong and what could be different.
Why They Matter: As the old saying goes, "A wise man learns more from his enemies than a fool from his friends." Understanding failures can be as instructive as celebrating successes.
The best way to understand the impact and necessity of cybersecurity is through real-world examples. Success stories inspire, while lessons from major breaches serve as cautionary tales. Either way, there's a wealth of wisdom to be gleaned from the experiences of others. After all, why learn the hard way when you can benefit from the hindsight of others?
Choosing a Cybersecurity Provider
How We Protect Our Clients
What We Offer: From threat assessment to 24/7 monitoring, our cybersecurity services are designed to provide comprehensive protection. We implement multi-layered defenses that adapt to evolving threat landscapes.
Why Choose Us: Our team of experts is committed to staying ahead of cybercriminals by continually updating our knowledge and technologies.
Tailored Solutions for Different Industries
What We Offer: Cybersecurity isn't one-size-fits-all. We offer solutions tailored to specific industries, addressing the unique challenges and compliance requirements of each.
Why Choose Us: We don't just offer solutions; we provide the right solutions for your needs.
Testimonials and Client Feedback
What They Say: Our clients vouch for our effectiveness, professionalism, and dedication to customer service.
Why Believe Them: Real-world endorsements provide evidence of our capabilities and commitment to client satisfaction.
Choosing a cybersecurity provider is like choosing a guardian for your digital assets. It's a decision that requires careful consideration and, often, a leap of faith. But with us, it's a leap backed by a safety net of proven expertise and tailored solutions. So go ahead, take that leap.
Future Trends in Cyber Security
Artificial Intelligence in Security
What It Is: AI technologies are increasingly being used to automate threat detection and response.
Why It's Important: AI can analyze vast amounts of data for anomalies in real-time, something human analysts would need help to do.
Quantum Computing
What It Is: Quantum computing has the potential to break current encryption methods but can also lead to new, more secure forms of encryption.
Why It's Important: As this technology matures, it will bring challenges and opportunities for cybersecurity.
Threat Intelligence
What It Is: This involves collecting and analyzing data to better understand current and future threats.
Why It's Important: Understanding what you're up against, you can develop more effective security strategies.
The future of cybersecurity is a race between the shield and the sword, with new technologies being used to both defend and attack. Awareness of these future trends is not just insightful; it's essential for preparing for the challenges. As they say, "The best way to predict the future is to invent it."
Start by fortifying your cybersecurity today.
Conclusion
- Cybersecurity is not just an IT issue; it's a critical business concern.
- The threat landscape is diverse and constantly evolving, requiring comprehensive and up-to-date security measures.
- Essential components like firewalls, antivirus software, and encryption play vital roles in a robust cybersecurity strategy.
- The benefits of investing in cybersecurity are immense, from protecting against threats to ensuring business continuity and maintaining customer trust.
- Debunking common myths and understanding the natural landscape is critical to building a strong cybersecurity posture.
Compliance and ethical considerations are non-negotiable elements of a holistic cybersecurity approach. - Real-world use cases and success stories are valuable lessons for what to do—and what not to do.
- Choosing the right cybersecurity provider can make all the difference in your organization's digital safety.

Get In Touch
Follow Us
Table of Contents
- What is Cybersecurity?
- Why is Cybersecurity Important?
- Cyber Security Threats
- Essential Components of Cyber Security
- Benefits of CyberSecurity
- Dangerous Cybersecurity Myths
- Realities of the Cyber Landscape
- Key Cybersecurity Technologies and Best Practices
- Compliance, Ethical, and Legal Dimensions
- Use Cases, Success Stories, and Case Studies in Cyber Security
- Choosing a Cybersecurity Provider
- Future Trends in Cyber Security
- Conclusion
- Get In Touch