Why Network Security In Cloud Computing Is Vital To Prevent Breaches?
Gururaj Singh
Nov 11, 2024
The cloud is estimated to store 100 zettabytes of world data by 2025—that’s 100,000,000,000,000 gigabytes.
With so much enormous valuable data and over 45% of businesses worldwide experiencing cloud-based data breaches, the chances of cloud data breaches and cyber crimes become exponential.
Cloud cybersecurity breaches have become a significant concern. In 2020, 79% of companies worldwide experienced at least one breach, making cloud security necessary for safeguarding organizations against cyber crimes.
Cloud computing will have a market size of USD 680 billion in 2024 and a CAGR of 16.40%. It needs network security to prevent breaches. Want to know why?
In this blog, understand why network security in cloud computing is vital to prevent breaches and other cyber attacks and threats.
What is Network security?
Network security (a subset of cybersecurity) means securing the network boundary of computers or devices, i.e., the boundary in which data travels between two devices. It includes safeguarding users’ data, location, applications, and confidential information via several tools and technologies.
What is Cloud Network Security?
Network security in cloud computing is also known as cloud network security. It is a set of processes, techniques, and policies to fortify devices, servers, infrastructure, and all types of cloud networks (public, private, and hybrid) from outsiders, unauthorized access, and malicious actors.
Importance of Network Security in Cloud Computing
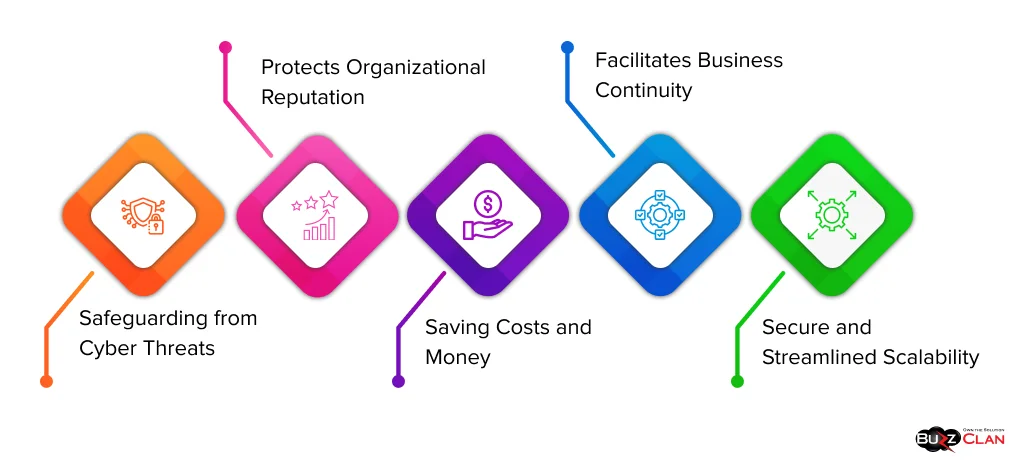
It holds utmost importance in cloud computing, helping prevent breaches and future cyber attacks; let’s see some of them:
Safeguarding from Cyber Threats
Network Security in cloud environments protects the organization, data, applications, and network operations from cyber-attacks.
Implementing several security measures, such as firewalls, VPNs, web security, etc., prevents cyber threats, such as DDoS attacks in cloud computing and CATO, from entering the organization’s security boundary.
Protects Organizational Reputation
Saving reputation by keeping the data confidential, whether its users’ location, financial information, or internet activity. Moreover, any unauthorized access or attack can significantly disrupt and destroy the reputation and goodwill of a business.
Saving Costs and Money
When data gets lost or someone else who doesn’t have any authority to access it breaches it, ransomware (a type of malware) can be launched, allegedly making you compelled to pay to save your data and reputation.
Even after paying the attackers, there is no defined chance of getting your data or intellectual properties. Applying network security in your cloud will strengthen your overall operations, eventually saving you money and costs.
Facilitates Business Continuity
Business Continuity is a term used to describe a business’s sustainability after a disruption. Cloud network security facilitates business continuity by minimizing downtime (when the system is unavailable due to technical issues). Constant uptime and service availability also increase customer and client trust, directing business growth and reliability.
Secure and Streamlined Scalability
When a business expands or shrinks cloud resources, robust network security ensures consistent protection without leaving scope for vulnerabilities. The expansion or shrinking also directly impacts the business’s network; thus, maintaining an effective and secured security posture and infrastructure are the key applications of secured and streamlined scalability of companies.
Network Security vs. Cloud Network Security
Let’s have a look at how network security is different from cloud network security with several differential components here:
| Aspects | Network Security | Cloud Network Security |
|---|---|---|
| Definition | Secures the in-house network, devices, and data from malicious activities. | Secures on-cloud servers and their applications, data, and infrastructure. |
| Scope | It protects internal hardware, software, and databases. | It protects cloud providers and the users who utilize the cloud services across devices. |
| Threat Detection | Uses techniques like IDS/IPS (traditional methods) to detect threats. | Goes one step further with AI, machine learning, and advanced threat detection tools. |
| Cost | A budget is allocated for businesses' network security. It is generally not expensive. | It uses a pay-as-you-go model. It doesn't require significant initial investments in network security, but it can be expensive on a massive business scale. |
| Disaster Recovery | More complex disaster recovery techniques and methods. | Built-in options for disaster recovery by the cloud providers. |
| Scalability | Low scalability, as it is limited by physical hardware and limited tech. | Highly scalable, as per demand, cloud network security can be facilitated. |
Components of Cloud Network Security
As blocks build up the whole castle, several components of cloud network security establish and ensure the safety and security of the activities in the cloud network.
Intrusion Detection and Prevention Systems (IDS/IPS)
IDS is a monitoring system that monitors and detects potential threats and malicious activities that can enter the network by unauthorized accessed entities. It uses an anomaly-detection system (unusual behavior identification) and signature-based detection (looking for previously happened attack patterns) to detect network traffic threats.
An IPS (Intrusion Prevention System) prevents attacks, breaches, and unusual behavioral activity by alerting and generating actions in real-time. For example, it blocks suspicious IP addresses, detects abnormal traffic flow, detects SQL injection, etc.
Security Information and Event Management (SIEM)
Security information and event management, or SIEM, is a technology that monitors network activities such as logins, errors, or file access. It logs the events or activities, collects data from various systems, and then analyzes it. If SIEM detects anything dodgy or shady, it will alert the team or the cloud provider to take safety measures, including compliance reporting and real-time monitoring and alerts.
Firewall
A firewall is a security system that protects data by establishing a wall (non-physical) between the network (your computer and the company’s system), restricting the entry of suspicious traffic or users. By blocking, i.e., establishing a barrier to unauthorized access, it controls and maintains the outgoing and incoming network traffic flow based on organizational policies, security guidelines, and rules. This aids in secure and safe activities happening on the cloud.
There are several components of a firewall that support robust security. Some of these are:
- Deep Packet Inspection (DPI) : DPI is an integral part of firewalls that deeply checks the network and its data. DPI reads and consumes the data to see if it contains threats.
- Stateful Inspection: Firewalls perform stateful inspections and track the records of data, including where it comes from and whether the source is trustworthy.
- Next-Gen Firewalls (NGFWs): As the name suggests, NGFWs go one step further than normal firewalls. Using advanced tech like AI, it detects threats and potential apps and websites that can harm the network.
VPN
You have heard of VPNs and must have used them sometime. But do you know what they do? A VPN, or virtual private network, covers your identity and encrypts your data and activities on the Internet.
With the magical cloak of VPN, your IP address gets hidden, allowing you to access the networks and the Internet without stressing about your footprints and identity.
VPN cloud establishes an encrypted connection between your device and the cloud provider’s infrastructure. Moreover, a VPN uses IPsec or a secure socket layer (SSL) to secure device communication.
Malicious actors can launch several types of malware, such as ransomware-as-a-service, trojan horses, and viruses. Still, they cannot find you on the Internet with a VPN, making your device and system unattainable.
Access Control
Access control in cloud security means controlling access to a company’s information or data. This means only allowing access to authorized users and restricting access according to role or attribute. Access control includes several components, such as:
- Identity and Access Management: With IAM, the organization allows access to the company’s database, emails, and applications to only those who have Work with them and restrict access to hackers or fishers, i.e., malicious actors.
- Password or Pin Protection: Passwords are an excellent way to access the respective person or system. They protect the file, document, or media and can only be accessed by someone who knows the key.
- MFA: MFA, or multi-factor authentication, is a type of access control that consists of multiple authentication factors other than passwords, such as biometrics scanning, Gmail OTP, or solving a puzzle. These factors determine whether the user is genuine or skeptical.
Encryption
Encryption means converting the data into an unreadable or gibberish form that makes it impossible for anyone to read. Unless the receiver decodes the cipher data by appropriate decoding methods, it eventually gains plain or normal data.
When the data travels in the network, it can be manipulated by attackers or cybercriminals. A protective shield across the system ensures potent data transfer from cloud to cloud or devices to cloud. That’s why encryption in cloud security is paramount.
Cloud Security Posture Management (CSPM)
What if there was a system that would check your overall cloud security and help eliminate any potential harm? Well, cloud security posture management (CSPM) does the same. CSPM is a set of several functions, tools, and techniques that manage cloud security’s macro and micro integral parts.
Its function is to identify and eradicate any possible or existing threats or weaknesses to their cloud systems. Whether handling misconfiguration risks, complying with rules and regulations, or identifying vulnerabilities, CSPM does it. CSPM, with the help of cloud security automation, scans the cloud environments with the cloud security best practices.
Data Loss Prevention (DLP)
As the name suggests, DLP facilitates data loss blockage, stopping sensitive or confidential data from spilling outside the organization’s boundary. This boundary is linked with the organization’s DLP policy (which defines how data is labeled, shared, and protected).
With the latest and ever-evolving technologies, such as AI and machine learning, DLP inspects information and filters any detected suspicious activity that can result in data loss using people and processes.
With data loss prevention, you can:
- Know your data: Understanding the data landscape, including data policies and possible loopholes of data loss.
- Protect your data: You can protect your data with MFA, sturdy incident responses, data encryption, and other data protective measures.
- Data loss prevention: This helps prevent your data from getting lost to phishers, social engineers, or hackers.
- Data retention: Aid in easily retaining, deleting, or saving data organizationally.
What are the Challenges to Cloud Network Security?
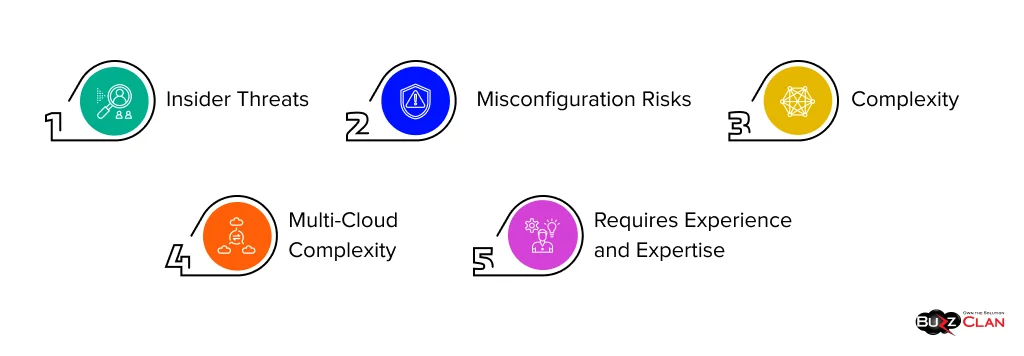
Everything has its peaks and valleys!!
So does Cloud Network Security.
Understand some valleys, a.k.a, ‘cloud security challenges’ that arise when network security is implemented in the cloud, here:
Requires Experience and Expertise
Cloud network security requires skilled personnel and highly trained professionals to secure the data and applications in the cloud network. The recruitment, selection, and training of these highly qualified professionals are costly and time-consuming, sometimes creating a skills gap.
Misconfiguration Risks
When implementing the cloud into network security, the configuration of cloud environments (being complex) often creates several security gaps. Unauthorized access can fill these gaps with malicious software, such as viruses, trojan horses, malware, etc.
Complexity
Network security components such as firewalls, IDS, and application security are complex tasks requiring the utmost precision and attention to detail. Leaving any room will be discovered by social engineers or cyber criminals and then used as a loophole to disrupt the data.
Insider Threats
Whether hardware or software, mistakes or concerns can arise due to the misuse of authority or access, whether accidental or intentional. These insider threats harm cloud network security, leading to extensive and massive data leaks and data theft possibilities. To eradicate this challenge, extra caution and proper authorization should be given.
Multi-Cloud Complexity
Again, implementing cloud computing and its technologies into network security is complex and requires a workforce. However, this complexity becomes exponentially larger when multiple clouds are submerged. It becomes much more complicated than infusing only a single cloud. With higher complexity, multi-cloud security also becomes convoluted.
Common Threats to Network Security in Cloud Computing
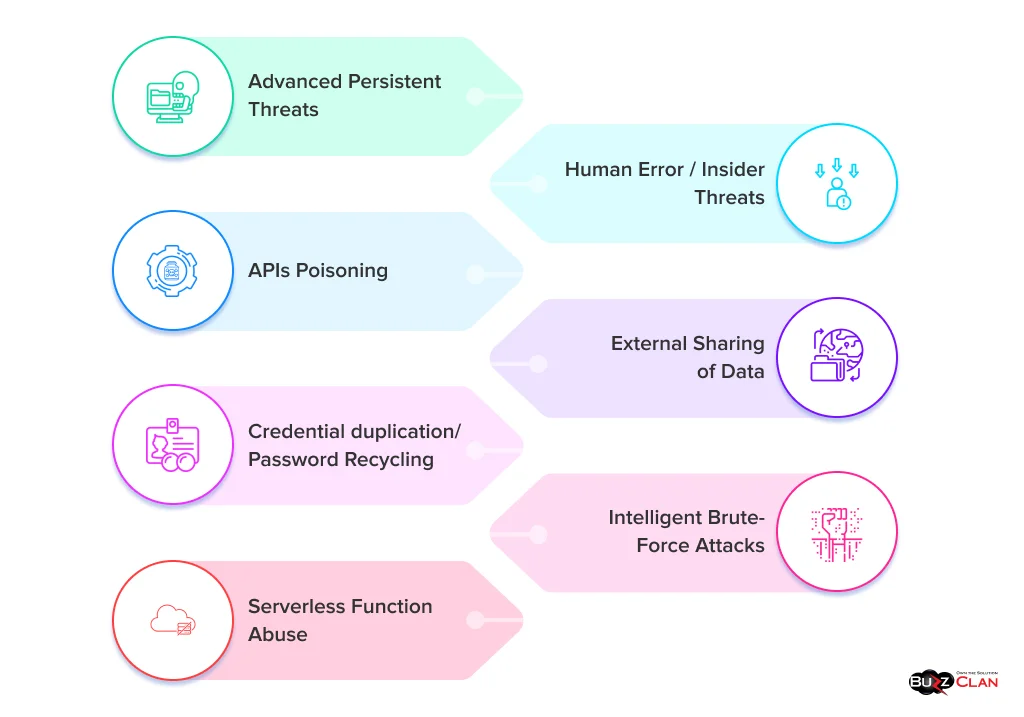
Cloud network security is a broad term encompassing many possible threats. Some of the most common threats are ransomware, DDoS attacks, and account hijacking via phishing in network security. Let’s discover some more common threats to network security in cloud computing:
- Advanced Persistent Threats: These discrete threats consist of attackers who enter a network through a loophole and stay there for a long time until they access confidential or sensitive information. The covert and stealthy perpetrators can transfer the data to the highest bidder for profit.
- Human Error / Insider Threats: Authoritative professionals or employees with access to confidential data or vital company systems can unintentionally or accidentally leak data. Black spots or poor inspection in security supervision can lead to vulnerabilities and potential areas where malicious activities can occur. With mistakes like these, human error contributes to the biggest cloud security concern for most business owners, i.e., data loss.
- APIs Poisoning: APIs or application programming interfaces are well-documented interfaces that cloud service providers’ customers use. Their easy usage can open loopholes for cybercriminals in the interface that can be launched for cyber attacks in the cloud-based services. Poor coding, insufficient authorization, and other factors can allow attackers to disrupt your system through injections, etc.
- External Sharing of Data: When links are shared with everyone, untrained or untrustworthy employees can share these emails or links with external parties. External sharing of data has been a major threat to cloud security. As in a cloud-based system, the infrastructure is shared amongst everyone in the network. The chances of breaches increase because any insider threat can forward confidential documents, links, or files with unauthorized access.
- Credential duplication/ Password Recycling: Massive data breaches can occur when users use the same passwords for multiple devices or accounts. If the attacker knows the password of any single account, they can leverage password recycling to access all accounts easily. Knowing the password to every account is easy due to the interconnected nature of the cloud servers.
- Intelligent Brute-Force Attacks: Brute-force attacks use a trial-and-error method. They continuously try to get access by infusing multiple passwords and usernames until the key unlocks the door. IP blocking and rate limiting are security measures that individuals or businesses should adopt to avoid these attacks. Intelligent brute-force attacks use AI and automation to recognize patterns, which can help in more enhanced password prediction and advanced breaching into systems.
- Serverless Function Abuse: Serverless computing services are exploited to launch malicious software or attacks like DDoS, crypto-jacking, spamming, and fishing. Insecure codes, like SQL injection and XSS, and malicious code execution by attackers abuse serverless functions. By ensuring the deployment of only verified codes, applying strong access controls, and maintaining the quality of the app structure, you can mitigate the risk of serverless function abuse.
Case Studies
To illustrate some of the famous and infamous data breaches of industry leaders, let’s look at some of the cloud security case studies:
Somewhere before August 2019, Facebook (an AWS user) suffered a massive data breach due to a vulnerability in its “contact importer” feature. Facebook did not inform 530 million users that their data, including phone numbers, names, locations, and user profiles, had been stolen until April 6, 2021, in one of their blogs (still published on Meta).
In their defense, the company said that they fixed the issues spontaneously. However, the news of this data breach was more prominent than their statement. This news led Mark Zuckerberg to settle a privacy case with the FTC (Federal Trade Commission), making Facebook pay $5 billion as a penalty.
Later, in October 2021, Frances Haugen (whistleblower) tainted them by stating that Facebook chose profits over safety. Following the breach, Facebook fortified its network security by preventing malicious scraping, encouraging privacy-setting updates, and more.
Toyota Motor Company
In June 2023, the data of approximately 260,000 Japanese customers was spilled due to a data breach caused by a misconfiguration in the cloud environment. This cloud security data breach illustrated that a simple misconfiguration can make attackers exploit your systems.
The Toyota Motor Company breach that exposed customers’ data went unnoticed from February 2015 to May 2023. Despite not exposing massive amounts of sensitive data, the breach leaked in-vehicle device IDs, updated data creation dates, map information, and their creation dates.
Understanding the need for robust network security in the cloud, the company implemented various network security measures. Some of them were real-time threat detection, the implementation of zero-trust architecture, and enhanced security protocols.
The Future of Network Security in Cloud Computing
The future of network security is filled with digital advancements and innovations. Let’s travel ahead in time and see what the future of network security in cloud computing looks like:
Zero-Trust Architecture
Zero-trust architecture has already been applied in several big cloud service providers, but it will be more extensive in the future. It builds a security architecture that doesn’t trust anyone in the network and constantly verifies devices on every access attempt.
This helps maintain a guarded environment with protection at every step, restricting viruses or attackers’ movements once they enter the system.
Adoption of PQC
PQC? PQC is post-quantum cryptography. In recent times, the power of quantum computing has broken and disrupted the methods of encryption that have been traditionally used. PQC adoption is a savior for long-term data protection in the cloud. Organizations can secure their data and its confidentiality with quantum-resistant encryption algorithms across cloud service providers.
Unified Cloud Security Management
Nowadays, where blockchain makes everything decentralized for more security, the cloud is going a new way. In the cloud, where safeguarding services across a broad range of cloud environments has become complex and complicated.
Unified cloud security management has been emerging for streamlined cloud security. Systems like XDR (extended detection and response) offer an expansive view of detected threats across all cloud environments. This approach allows for easier and uncomplicated protection of cloud servers and infrastructures.
AI and ML: Transforming Cloud Security
Like every other industry, AI in cloud network security is booming. AI and machine learning algorithms and programs detect threats by spotting unusual behaviors, automating necessary steps, and instantaneously strengthening the security system by adapting to new threats.
DevSecOps Integration
Dev(development), Sec(security), and Ops(operations) together make DevSecOps. An approach that builds security into the development process from the start. This approach applies the security function at the same pace and scale as the development and operations functions are implemented.
This ensures that security is everyone’s (development or operations teams) shared responsibility and accountability. DevSecOps is an excellent, efficient approach for fixing vulnerabilities in the cloud earlier than ever, and that is also true on a large scale.
Why Customers Choose BuzzClan?
Customers choose BuzzClan because it empowers businesses and individuals with innovative, cutting-edge solutions. BuzzClan tailors threat-mitigated comprehensive solutions according to your changing business priorities, bringing a mix of expertise and experience.
Our team of experts is always set to fortify your cloud’s network security, from cloud migration services to robust cloud BI analytics. From cloud cost optimization to multi-cloud managed services, BuzzClan is your ultimate support.
Conclusion
With the ever-evolving size of digital transformation, the cloud computing industry will only expand at an unprecedented pace, followed by hackers and cybercriminals. That’s why the infusion of network security in the cloud is a must to prevent breaches in cloud servers, networks, and systems.
Understanding the importance of cloud network security can safeguard your business, and with futuristic technological advancements such as AI and ML, you can gain an edge over your competitors.
Implement robust cloud security components to tackle the challenges and possible threats and protect your business from malicious activities for long-lasting business growth and continuity.
FAQs

Get In Touch
