DDoS Protection: The Comprehensive Guide to Safeguarding Your Digital Assets
Manoj Mehra
Oct 4, 2024
Introduction
In the modern digital landscape, where businesses and individuals rely heavily on online services, Distributed Denial of Service (DDoS) attacks loom. DDoS protection is a crucial aspect of cybersecurity that aims to mitigate the risks associated with these malicious attacks. This comprehensive guide will delve into the fundamentals of DDoS protection, explore various solutions, and provide insights on safeguarding your digital assets effectively.
Understanding DDoS Attacks
Unveiling the world of DDoS attacks, this section explains their nature and impact, providing essential knowledge about this critical cybersecurity threat.
What is a DDoS Attack?
A DDoS attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic. These attacks are typically carried out by utilizing multiple compromised computer systems as sources of attack traffic. DDoS attacks can be categorized into three main types:
- Volume-based attacks aim to saturate the bandwidth of the targeted resource, making it inaccessible to legitimate traffic.
- Protocol attacks target network layer protocols, consuming server resources and rendering the target unresponsive.
- Application layer attacks focus on exploiting vulnerabilities in application layer protocols, exhausting server resources, and causing denial of service.
DDoS Attack Impact
The consequences of DDoS attacks can be severe, affecting businesses, organizations, and individuals. Some real-world examples include:
- GitHub DDoS attack (2018): GitHub, the popular code hosting platform, suffered a massive DDoS attack that peaked at 1.35 Tbps, causing intermittent outages and service disruptions.
- Dyn DDoS attack (2016): A major DDoS attack targeting Dyn, a DNS provider, resulted in widespread internet outages, affecting prominent websites such as Twitter, Netflix, and Amazon.
- PlayStation Network and Xbox Live DDoS attacks (2014): Gaming networks PlayStation Network and Xbox Live experienced extended downtime due to DDoS attacks, frustrating millions of gamers during the holiday season.
Fundamentals of DDoS Protection
Fundamentals of DDoS Protection outlines key defense strategies against DDoS attacks, focusing on safeguarding critical network elements such as DNS and proxy servers.
Components of DDoS Protection
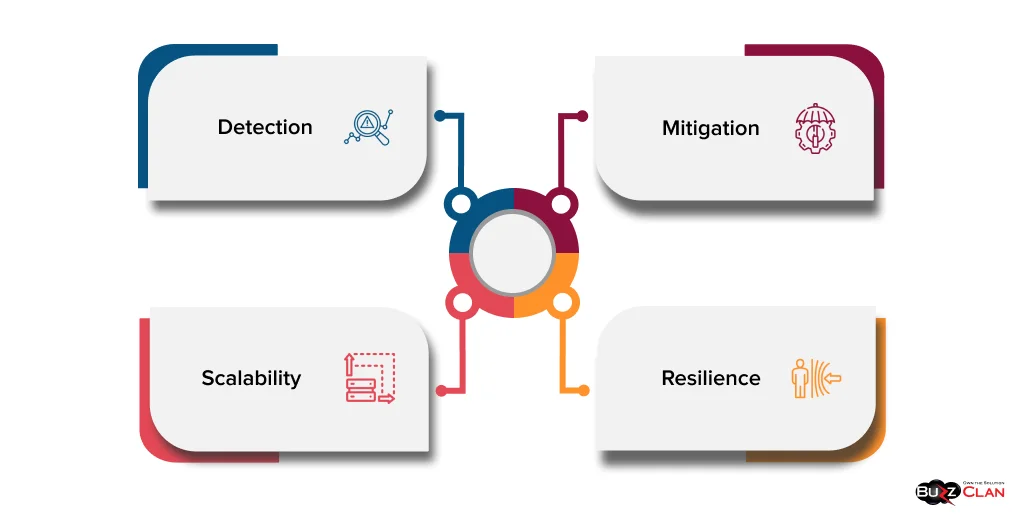
An effective DDoS protection strategy encompasses several key elements:
- Detection: Identifying and distinguishing legitimate traffic from malicious DDoS traffic.
- Mitigation: Filtering and blocking malicious traffic while allowing legitimate traffic.
- Scalability: Ensuring the protection mechanism can handle large-scale attacks without performance degradation.
- Resilience: Implementing redundancy and failover mechanisms to maintain service availability during an attack.
DNS and Proxy Protection
DNSProxy plays a pivotal role in DDoS protection by acting as a robust intermediary between clients and the origin server. It serves as a guardian, filtering and absorbing malicious traffic before it can reach the targeted resource. It provides several essential benefits:
- Traffic Filtering: DNSProxy has advanced algorithms and predefined rules to identify and block malicious traffic effectively. Analyzing incoming requests can detect anomalies and suspicious patterns, such as sudden traffic spikes or unusual geographical origins. This filtering mechanism safeguards the origin server from being overwhelmed by malicious traffic, minimizing the impact of DDoS attacks.
- Load Balancing: DNSProxy employs load-balancing techniques to distribute incoming traffic across multiple servers or data centers. This intelligent approach enhances performance and ensures the origin server is manageable. By spreading the load, DNSProxy prevents bottlenecks and maintains optimal performance even during DDoS attacks, ensuring uninterrupted service for legitimate users.
- Caching: DNSProxy incorporates a caching mechanism to store frequently requested content locally. This caching capability reduces the load on the origin server and significantly improves response times for subsequent requests. By serving cached content locally, DNSProxy minimizes the need for the origin server to process repetitive requests, resulting in enhanced efficiency and faster content delivery.
- Real-Time Monitoring and Analytics: DNSProxy provides real-time monitoring capabilities, enabling administrators to see traffic patterns and promptly identify potential threats. It offers comprehensive analytics that helps analyze attack vectors, traffic volumes, and geographic origins of malicious requests. This real-time monitoring allows for quick response and mitigation of DDoS attacks, minimizing downtime and maximizing uptime for critical services.
- Scalability and Flexibility: DNSProxy is designed to scale effortlessly to accommodate varying traffic volumes and attack intensities. It can be easily configured to handle large-scale DDoS attacks without compromising performance or protection. The flexible architecture of DNSProxy allows for customization and integration with existing infrastructure, ensuring seamless deployment and efficient DDoS mitigation.
- High Availability and Redundancy: DNSProxy ensures high availability and redundancy to maintain continuous protection against DDoS attacks. It employs multiple redundant servers and load balancers to prevent single points of failure. In a server outage or failure, DNSProxy automatically reroutes traffic to alternate servers, ensuring uninterrupted service and minimizing downtime.
DDoS Protection Solutions
DDoS Protection Solutions covers an overview of service providers and essential factors to consider when selecting a DDoS protection solution, offering guidance on making informed choices for a robust defense.
Service Providers Overview
Several cloud service providers offer DDoS protection solutions. Let’s compare a few popular options:
- AWS Shield: Amazon Web Services (AWS) provides AWS Shield, a managed DDoS protection service that safeguards applications running on AWS. AWS Shield Standard (free) and AWS Shield Advanced (paid) offer two tiers.
- Azure DDoS Protection: Microsoft Azure offers Azure DDoS Protection, a service that defends Azure resources against DDoS attacks. It provides two tiers: Basic (free) and Standard (paid).
- Cloudflare DDoS Protection: Cloudflare is a popular content delivery network (CDN) that offers DDoS protection as part of its services. It provides various plans, including a free tier and paid options with advanced features.
Free vs. Paid Protection
Organizations can choose between free and paid protection solutions When defending against distributed denial-of-service (DDoS) attacks. The choice depends on several factors, including the size and criticality of the organization’s IT infrastructure, the budget available for cybersecurity, and the level of protection required.
Free DDoS Protection Services
Free DDoS protection services offer basic protection against common attack vectors, such as SYN floods, UDP floods, and ICMP floods. These services typically involve open-source software or cloud-based platforms that can be deployed quickly and easily. While free DDoS protection services can provide some protection, they often need more advanced features and customization options. They may also have limited capacity and need help to handle large-scale attacks.
Paid DDoS Protection Services
Paid DDoS protection services provide more comprehensive protection against a wider range of attack vectors, including more sophisticated attacks such as application-layer attacks and zero-day exploits. These services typically use dedicated hardware and software appliances to withstand large-scale attacks. Paid DDoS protection services offer higher support and customization, allowing organizations to tailor the protection to their specific needs.
Factors to Consider When Choosing a DDoS Protection Solution
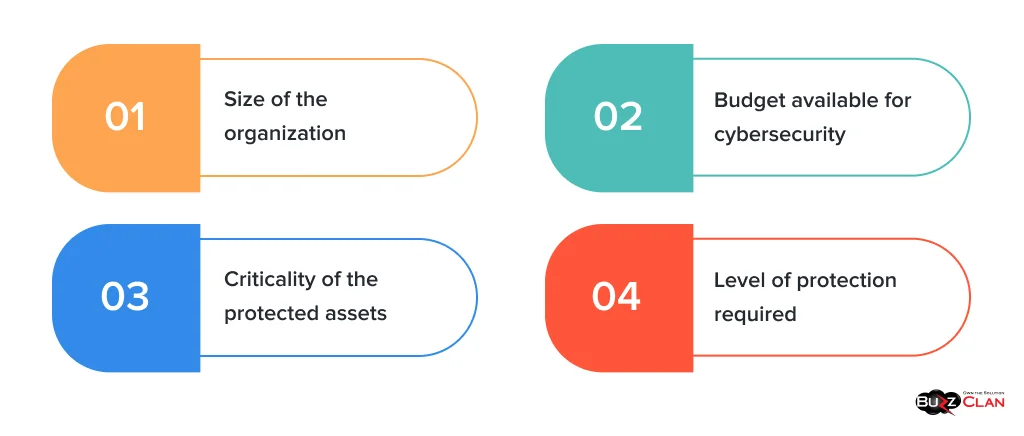
When choosing a DDoS protection solution, organizations should consider the following factors:
- Size of the organization: Larger organizations with a larger IT infrastructure need more comprehensive protection than smaller ones.
- Criticality of the protected assets: Organizations that rely on their IT infrastructure for critical business operations will need more robust protection than organizations that do not.
- Budget available for cybersecurity: The cost of DDoS protection services can vary significantly, so organizations must consider their budget when deciding.
- Level of protection required: Organizations need to assess the level of protection they need based on the types of attacks they are likely to face.
Implementing DDoS Protection
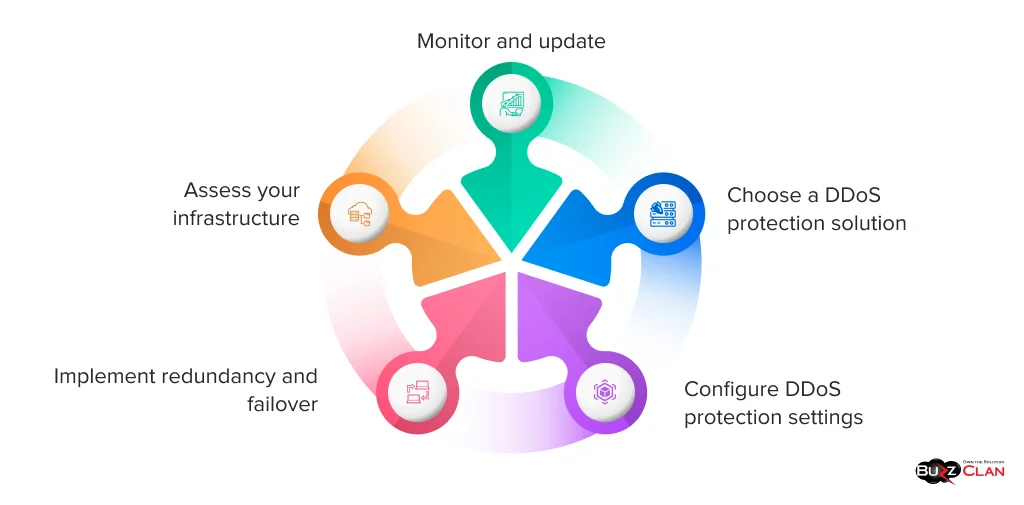
Building DDoS Resilience
To set up effective DDoS protection, follow these steps:
- Assess your infrastructure: Identify critical assets and potential vulnerabilities that could be exploited in a DDoS attack.
- Choose a DDoS protection solution: Based on your requirements and budget, select a service provider or implement an in-house solution.
- Configure DDoS protection settings: Set up filters, thresholds, and mitigation rules to detect and block malicious traffic.
- Implement redundancy and failover: Ensure your infrastructure can handle traffic spikes and maintain availability during attacks.
- Monitor and update: Continuously monitor and update your DDoS protection system to stay ahead of emerging threats.
DDoS Protection for Websites and Services
To safeguard web assets specifically, consider the following strategies:
- Use a content delivery network (CDN): CDNs can absorb and filter DDoS traffic before it reaches your origin server.
- Implement rate limiting: To prevent resource exhaustion, limit the requests allowed from a single IP address within a specific timeframe.
- Enable web application firewall (WAF): WAFs can detect and block application-layer DDoS attacks by inspecting incoming traffic and applying predefined rules.
- Optimize server resources: Ensure that your servers are properly configured and optimized to handle high traffic loads and mitigate the impact of DDoS attacks.
Advanced DDoS Protection Techniques
Preventing DDoS protection involves a set of robust techniques and tools. Understanding advanced DDoS protection techniques, including cloud-based, hardware, and software protection, and how they can help organizations secure their servers, traffic, and network is imperative.
Cloud-Based DDoS Protection
Cloud-based DDoS protection services like AWS Shield and Azure DDoS Protection offer advanced capabilities to mitigate DDoS risks:
- Always-on detection: Cloud-based solutions continuously monitor traffic patterns and automatically detect and mitigate DDoS attacks.
- Scalability: Cloud infrastructure can dynamically scale to absorb and filter large volumes of DDoS traffic.
- Multi-layer protection: Cloud-based services protect the network, transport, and application layers, covering various DDoS attack vectors.
- Threat intelligence: Cloud providers leverage global threat intelligence to identify and block emerging DDoS threats proactively.
Hardware and Software Solutions
In addition to cloud-based services, organizations can also employ hardware appliances and software tools for DDoS mitigation:
- Hardware appliances: Dedicated DDoS mitigation appliances can be deployed on-premises to filter and block malicious traffic before it reaches the protected resources.
- Software-based solutions: Software tools can be installed on servers or network devices to detect and mitigate real-time DDoS attacks.
- Hybrid solutions: Combining cloud-based and on-premises DDoS protection can provide comprehensive coverage and flexibility in handling various attack scenarios.
Choosing the Right DDoS Protection
Conducting regular security audits and having contingency plans are great practices. However, to ensure long-term success, you need to have a dedicated provider in place.
Understanding Your Needs
When selecting a DDoS protection provider, consider the following factors:
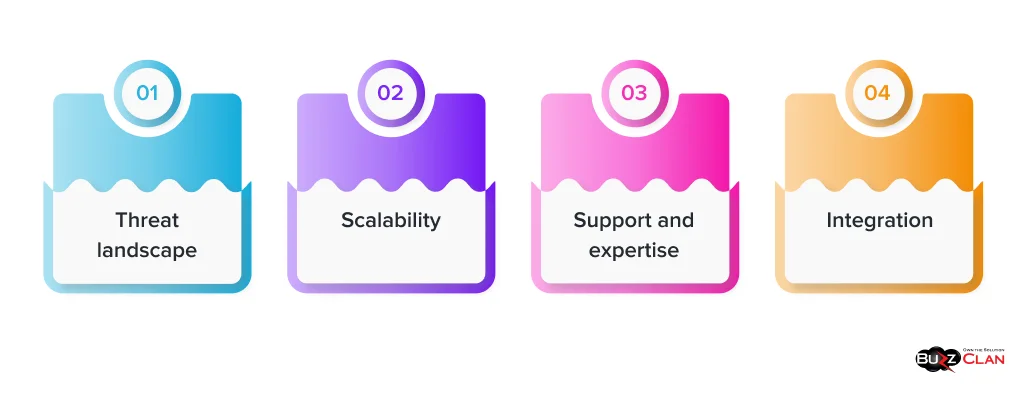
- Threat landscape: Evaluate the types of DDoS attacks your organization will likely face based on your industry, services, and online presence.
- Scalability: Ensure that the DDoS protection solution can scale to handle the volume and complexity of potential attacks.
- Integration: Consider how well the DDoS protection service integrates with your existing infrastructure and security tools.
- Support and expertise: Look for a provider with reliable customer support and a proven track record in mitigating DDoS attacks.
Evaluating DDoS Protection Services
When comparing DDoS protection services, consider the following:
- Attack mitigation capabilities: Assess the service’s ability to handle different types of DDoS attacks and the effectiveness of its mitigation techniques.
- Pricing and cost: Evaluate the pricing models and cost implications of different DDoS protection solutions, considering data transfer, number of protected resources, and additional features.
- Service level agreements (SLAs): Review the provider’s SLAs to understand their commitments regarding uptime, mitigation response times, and support availability.
- Ease of use and management: Consider the user-friendliness of the DDoS protection service’s interface and its level of control and customization.
The Future of DDoS Protection
Emerging technologies are poised to revolutionize DDoS protection, enhancing network security systems. Key trends shaping the future of DDoS protection include:
Emerging Threats and Protection Methods
As DDoS attacks evolve, so do the protection technologies and strategies. Some emerging trends in DDoS protection include:
- AI and machine learning: Leveraging artificial intelligence and machine learning algorithms to detect and mitigate DDoS attacks more effectively.
- Blockchain-based protection: Exploring the use of blockchain technology to create decentralized and resilient DDoS protection systems.
- Software-defined networking (SDN): Utilizing SDN to enable dynamic and programmable DDoS mitigation strategies.
- Collaborative defense: Fostering collaboration among organizations and service providers to share threat intelligence and coordinate DDoS defense efforts.
DDoS Protection and the Internet of Things (IoT)
The unprecedented proliferation of Internet of Things (IoT) devices has revolutionized various aspects of our lives, bringing about undeniable convenience and interconnectedness. However, this rapid growth has a significant downside – increased vulnerability to Distributed Denial of Service (DDoS) attacks. IoT devices, often plagued by weak security measures, pose a prime target for exploitation. They can be easily compromised and incorporated into large-scale botnets, which, in turn, are used to launch crippling DDoS attacks.
The number of IoT devices connected to the Internet is staggering and continues to rise exponentially. This immense network of devices presents an attractive target for malicious actors seeking to disrupt online services or extort organizations. As the number of connected devices grows, prioritizing IoT security becomes imperative. Implementing robust DDoS protection measures at device and network levels is essential.
At the device level, manufacturers must take responsibility for incorporating security features into their products. This includes employing strong default passwords, regularly issuing security updates, and implementing secure protocols for communication. Users, for their part, should refrain from using default passwords and ensure that their devices are updated with the latest security patches.
Service providers and enterprises must adopt comprehensive DDoS protection solutions at the network level. These solutions should be capable of detecting and mitigating DDoS attacks in real time, effectively safeguarding critical infrastructure and online services. Additionally, it is crucial to educate network administrators and security professionals about the unique challenges posed by IoT-based DDoS attacks and provide them with the necessary tools and expertise to combat these threats effectively.
The convergence of IoT and DDoS protection is a critical area that demands immediate attention. By addressing the inherent security weaknesses of IoT devices and implementing robust DDoS protection measures, organizations can safeguard their networks and ensure online services’ continued availability and integrity. Failure to prioritize IoT security could have severe consequences, leading to disruptions, financial losses, and reputational damage.
Conclusion
DDoS attacks pose a significant threat to the availability and integrity of online services, making DDoS protection a critical component of any comprehensive cybersecurity strategy. By understanding the fundamentals of DDoS attacks, exploring various protection solutions, and implementing proactive measures, organizations can effectively safeguard their digital assets and maintain business continuity in the face of evolving threats.
As the digital landscape continues to expand and evolve, businesses and individuals must stay informed about the latest DDoS protection techniques and best practices. By taking a proactive approach to cybersecurity and investing in robust DDoS protection solutions, organizations can minimize the risk of falling victim to devastating DDoS attacks and ensure the uninterrupted delivery of their online services.
FAQs

Get In Touch