The Definitive Guide to Zero Trust Architecture: Principles, Implementation, and Benefits
Sachin Jain
Nov 8, 2024
Introduction
Zero Trust Architecture (ZTA) is a comprehensive security model that operates on “never trust, always verify.”
Unlike traditional perimeter-based security approaches, which assume that everything inside an organization’s network can be trusted, Zero Trust assumes that no user, device, or network should be trusted by default, regardless of whether inside or outside the organization’s perimeter.
The concept of Zero Trust was first introduced by John Kindervag, then a principal analyst at Forrester Research, in 2010. Since then, it has evolved from a theoretical model to a practical and widely adopted security framework. The rapid digital transformation and the rise of cloud computing, mobile devices, and remote work have accelerated the need for a more robust and adaptable security approach – making Zero Trust more relevant than ever.
This comprehensive guide will explore Zero Trust Architecture’s core principles, implementation strategies, benefits, and real-world applications. Whether you’re a cybersecurity professional, IT manager, or business leader, this article will provide the knowledge and insights to understand and leverage Zero Trust Architecture in your organization’s security strategy.
Understanding Zero Trust Architecture
To truly grasp the concept of Zero Trust Architecture, it’s essential to understand its core principles, how it compares to traditional security models, and the key components that make up this innovative approach to cybersecurity.
Core Principles of Zero Trust Architecture
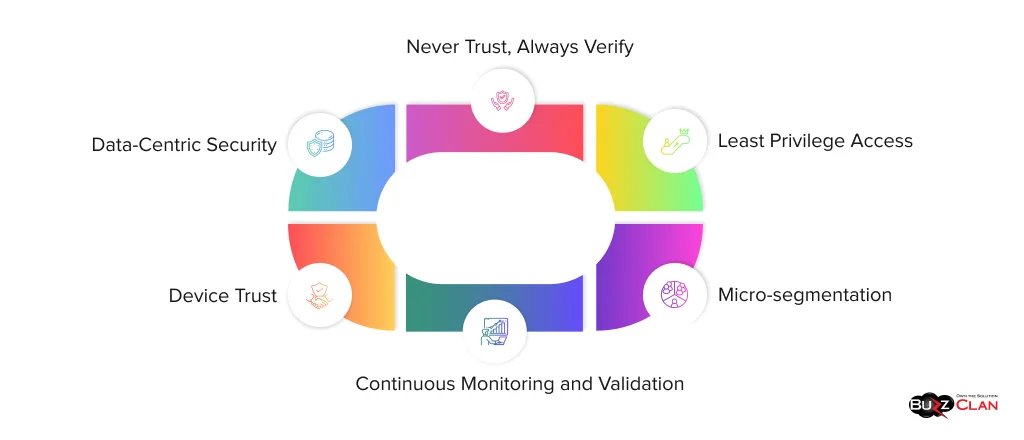
- Never Trust, Always Verify: The foundational principle of Zero Trust is that no entity, whether user, device, or network, should be automatically trusted. Every access request must be authenticated and authorized, regardless of the source.
- Least Privilege Access: Users and systems should be granted only the minimum level of access necessary to perform their tasks. This principle helps to minimize the potential damage if a breach occurs.
- Micro-segmentation: Networks should be divided into smaller, isolated segments to contain potential breaches and limit lateral movement within the network.
- Continuous Monitoring and Validation: Zero Trust systems continuously monitor and validate user activities, device health, and network traffic to detect and respond to real-time threats.
- Device Trust: The security posture of devices should be assessed before granting access to resources, ensuring that only trusted devices can connect to the network.
- Data-Centric Security: Protection should focus on securing data rather than just securing network perimeters or specific endpoints.
Comparison with Traditional Security Models
To appreciate the value of Zero Trust Architecture, it’s helpful to compare it with traditional security models:
| Security Models | Traditional Approach | Zero Trust Approach |
|---|---|---|
| Perimeter-Based Security | Focuses on securing the network perimeter with firewalls and VPNs. | Assumes the network is always hostile and focuses on securing individual resources. |
| Trust Model | Trusts entities within the network perimeter by default. | Trusts no one by default, inside or outside the network. |
| Access Control | Often relies on a single factor (like a password) for authentication. | Implements multi-factor authentication and continuous validation. |
| Network Segmentation | Limited segmentation, often based on broad categories. | Micro-segmentation based on individual workloads and data. |
| Monitoring | Often focuses on perimeter monitoring and may have blind spots within the network. | Continuous monitoring of all network traffic and user activities. |
Key Components of Zero Trust Architecture
- Identity and Access Management (IAM): Robust IAM systems are crucial for authenticating and authorizing users and devices.
- Multi-Factor Authentication (MFA): MFA adds additional layers of security beyond just passwords.
- Network Segmentation Tools: These allow for creating and managing micro-segments within the network.
- Security Information and Event Management (SIEM): SIEM systems collect and analyze log data from across the network to detect and respond to security incidents.
- Endpoint Detection and Response (EDR): EDR tools monitor endpoints for suspicious activities and provide response capabilities.
- Data Encryption: Encryption protects data at rest and in transit.
- Policy Engine: A central system that makes and enforces access decisions based on various contextual factors.
- Policy Administrator: Executes the policy decisions the policy engine makes.
- Policy Enforcement Points: These are the places where policy decisions are enforced, such as firewalls, gateways, and software-defined perimeters.
Understanding these core principles, comparisons, and key components provides a solid foundation for further exploring Zero Trust Architecture. As we proceed, we’ll examine how these elements come together to form a comprehensive security model well-suited to the challenges of modern IT environments.
Further Reading
The Zero Trust Architecture Model
Understanding its model in detail is crucial to fully appreciating the power and flexibility of Zero Trust Architecture. This section will comprehensively explain the architecture, including a visual representation through a Zero Trust Architecture diagram, and highlight how it fundamentally differs from traditional perimeter-based security approaches.
Detailed Explanation of the Architecture
The Zero Trust Architecture model can be broken down into several key layers and components:
User/Entity Layer
- This layer includes all users, devices, and services that request access to resources.
- Each entity is treated as potentially hostile until proven otherwise.
Identity and Access Management (IAM) Layer
- Responsible for authenticating and authorizing all access requests.
- Incorporates multi-factor authentication, Single Sign-On (SSO), and adaptive authentication techniques.
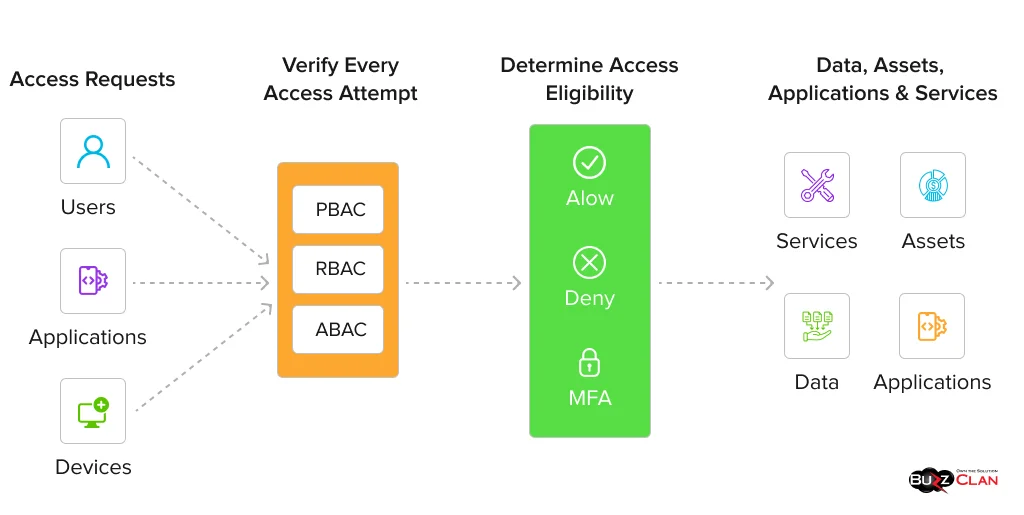
Policy Decision Point (PDP)
- The central brain of the Zero Trust model.
- Evaluates access requests against security policies, considering factors like user identity, device health, resource sensitivity, and environmental context.
Policy Enforcement Point (PEP)
- Executes the decisions made by the PDP.
- Located at various points throughout the network, including gateways, firewalls, and application proxies.
Data and Resource Layer
- Represents the protected assets, including applications, data, services, and infrastructure.
- Each resource is individually secured and requires explicit permission for access.
Visibility and Analytics Layer
- Continuously monitors and logs all activities across the network.
- Provides real-time threat detection and response capabilities.
Automation and Orchestration Layer
- Coordinates the various components of the Zero Trust ecosystem.
- Enables rapid response to security events and policy updates.
Zero Trust Architecture Diagram
How Zero Trust Architecture Differs from Perimeter-Based Security
Zero Trust Architecture represents a paradigm shift from traditional perimeter-based security models. Here are the key differences:
Trust Model
- Perimeter-Based: Assumes everything inside the network perimeter is trustworthy.
- Zero Trust: Treats all network traffic as potentially hostile, regardless of origin.
Access Control
- Perimeter-Based: Often relies on a “castle-and-moat” approach, with strong perimeter defenses but limited internal controls.
- Zero Trust: Implements fine-grained access controls for every resource, requiring continuous authentication and authorization.
Network Segmentation
- Perimeter-Based: May use broad network segments based on departments or functions.
- Zero Trust: Employs micro-segmentation, isolating individual workloads and data.
Visibility
- Perimeter-Based: Often has limited visibility into internal network traffic.
- Zero Trust: Provides comprehensive visibility across all network traffic and user activities.
Adaptability
- Perimeter-Based: Can struggle to accommodate modern work patterns like remote work and BYOD.
- Zero Trust: Designed to support diverse and dynamic IT environments, including cloud and hybrid infrastructures.
Data Protection
- Perimeter-Based: Focuses on protecting the network perimeter.
- Zero Trust: Emphasizes data-centric security, protecting information wherever it resides.
Threat Model
- Perimeter-Based: Primarily defends against external threats.
- Zero Trust: Assumes threats can come from inside and outside the organization.
Continuous Monitoring
- Perimeter-Based: May rely on periodic security assessments.
- Zero Trust: Implements continuous monitoring and real-time security posture assessment.
Zero Trust Architecture provides a more robust, flexible, and comprehensive approach to protecting modern digital environments by reimagining security from the ground up. As we explore this model, we’ll delve into its core pillars, implementation strategies, and real-world applications.
Pillars of Zero Trust Architecture
Zero Trust Architecture is built upon several fundamental pillars that work together to create a comprehensive and robust security framework. Understanding these pillars is crucial for organizations implementing or improving their Zero Trust strategy. Let’s explore each of these pillars in detail:
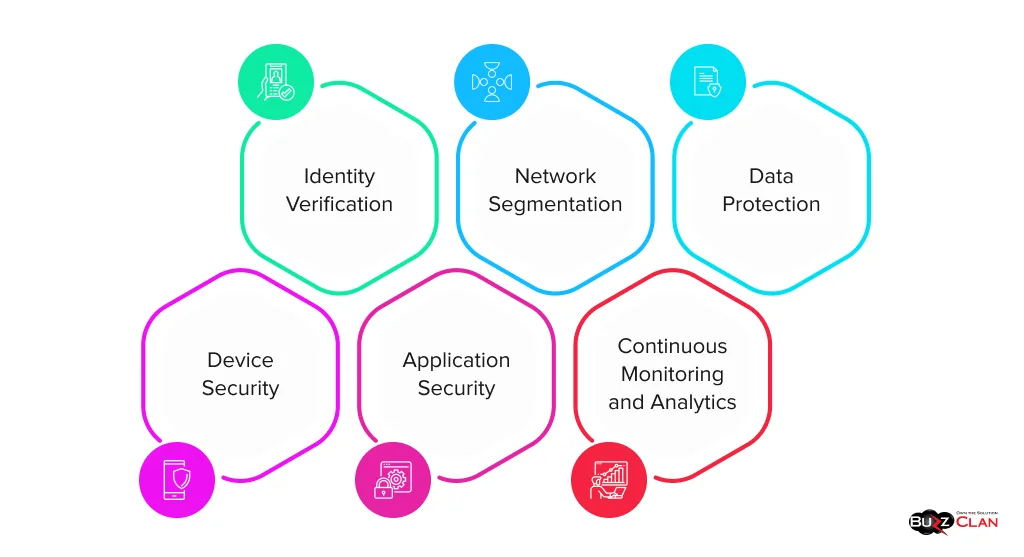
Identity Verification
Identity is at the core of Zero Trust Architecture. This pillar ensures that every user, device, and application is authenticated adequately before granting access to resources.
Key aspects of identity verification include:
- Multi-Factor Authentication (MFA): Requiring multiple forms of identification, such as passwords, biometrics, or security tokens.
- Adaptive Authentication: Adjusting authentication requirements based on risk factors like location, device, and access patterns.
- Single Sign-On (SSO): Providing a seamless user experience while maintaining strong security.
- Identity Federation: Enabling secure authentication across different domains or organizations.
Device Security
In a zero-trust model, devices are potential threat vectors and must be verified before accessing network resources.
Essential elements of device security include:
- Device Health Checks: Assessing the security posture of devices before granting access.
- Mobile Device Management (MDM): Enforcing security policies on mobile devices.
- Endpoint Detection and Response (EDR): Monitoring devices for suspicious activities and providing response capabilities.
- Patch Management: Ensuring all devices have the latest security patches.
Network Segmentation
Network segmentation is crucial for containing potential breaches and limiting lateral movement within the network.
Key aspects of network segmentation in Zero Trust include:
- Micro-segmentation: Dividing the network into small, isolated segments based on individual workloads.
- Software-Defined Perimeter (SDP): Creating dynamic, identity-centric perimeters around specific resources.
- East-West Traffic Control: Monitoring and controlling traffic between network segments.
- Network Access Control (NAC): Enforcing access policies at the network level.
Application Security
Securing applications is critical in a zero-trust model, as they often interface with users and sensitive data.
Important elements of application security include:
- Application-Level Authentication: Requiring authentication for each application, regardless of network location.
- API Security: Protecting APIs facilitating communication between applications and services.
- Runtime Application Self-Protection (RASP): Enabling applications to detect and prevent real-time attacks.
- Web Application Firewalls (WAF): Filtering and monitoring HTTP traffic between web applications and the Internet.
Data Protection
Data is often the primary target of cyber attacks, making its protection a critical pillar of Zero Trust Architecture.
Key aspects of data protection include:
- Data Encryption: Protecting data both at rest and in transit.
- Data Loss Prevention (DLP): Implementing controls to prevent unauthorized data exfiltration.
- Information Rights Management (IRM): Controlling how data can be used, even after it has been accessed.
- Data Classification: Categorizing data based on sensitivity to apply appropriate protection measures.
Continuous Monitoring and Analytics
Zero Trust Architecture relies on ongoing visibility and analysis to detect and respond to potential threats.
Essential elements of continuous monitoring and analytics include:
- Security Information and Event Management (SIEM): Collecting and analyzing log data from the network.
- User and Entity Behavior Analytics (UEBA): Detecting anomalies in user and system behaviors.
- Threat Intelligence Integration: Incorporating external threat data to enhance detection capabilities.
- Automated Incident Response: Enabling rapid reaction to detected threats.
These pillars of Zero Trust Architecture work together to create a comprehensive security framework that addresses the complex challenges of modern IT environments. By focusing on these key areas, organizations can significantly enhance their security posture and better protect their critical assets from evolving cyber threats.
Implementing Zero Trust Architecture
Implementing Zero Trust Architecture is a significant undertaking that requires careful planning, execution, and ongoing management. This section will provide a step-by-step guide to implementation, discuss common challenges and considerations, outline best practices, and present a case study of successful Zero Trust Architecture implementation.
Step-by-Step Guide to Implementing Zero Trust Architecture

Assessment and Planning:
- Conduct a thorough inventory of all assets, users, and data flows.
- Identify critical assets and prioritize protection.
- Define your organization’s security policies and access requirements.
Identity and Access Management:
- Implement a robust IAM system with multi-factor authentication.
- Establish strong password policies and consider passwordless authentication methods.
- Set up Single Sign-On (SSO) for seamless application user experience.
Network Segmentation:
- Map out your network and identify logical segmentation points.
- Implement micro-segmentation using software-defined networking or next-generation firewalls.
- Set up monitoring for east-west traffic within the network.
Device Security:
- Deploy endpoint protection and EDR solutions on all devices.
- Implement a Mobile Device Management (MDM) system for BYOD and corporate devices.
- Establish device health checks and remediation processes.
Data Protection:
- Classify data based on sensitivity and criticality.
- Implement encryption for data at rest and in transit.
- Deploy Data Loss Prevention (DLP) solutions to prevent unauthorized data exfiltration.
Application Security:
- Implement application-level authentication and authorization.
- Secure APIs using API gateways and proper authentication mechanisms.
- Deploy Web Application Firewalls (WAF) for internet-facing applications.
Continuous Monitoring and Analytics:
- Set up a SIEM system to collect and analyze logs from all systems.
- Implement User and Entity Behavior Analytics (UEBA) to detect anomalies.
- Establish a Security Operations Center (SOC) for ongoing monitoring and incident response.
Policy Enforcement:
- Deploy Policy Enforcement Points (PEPs) throughout the network.
- Implement a central policy engine to make and enforce access decisions.
- Regularly review and update policies based on changing requirements and threat landscapes.
Training and Awareness:
- Educate employees about Zero Trust principles and their role in maintaining security.
- Conduct regular security awareness training sessions.
Continuous Improvement:
- Regularly assess the effectiveness of your Zero Trust implementation.
- Stay informed about emerging threats and evolving Zero Trust best practices.
- Continuously refine and optimize your Zero Trust Architecture.
Challenges and Considerations
Implementing Zero Trust Architecture comes with several challenges:
- Complexity: Zero Trust requires a holistic approach that touches every aspect of IT infrastructure.
- Legacy Systems: Older systems may not support modern authentication and segmentation techniques.
- User Experience: Balancing security with user convenience can be challenging.
- Cost: Implementing Zero Trust often requires significant investment in new tools and technologies.
- Cultural Resistance: Employees may resist the additional security measures and perceived inconvenience.
- Skill Gap: Zero Trust requires expertise that may not be readily available in-house.
Best Practices for Implementation
To overcome these challenges and ensure successful implementation, consider these best practices:
- Start Small: Begin with a pilot project or critical asset before rolling out Zero Trust across the organization.
- Prioritize: Focus on protecting your most critical assets first.
- Leverage Existing Investments: Adapt and integrate existing security tools into your Zero Trust framework where possible.
- Adopt a Phased Approach: Implement Zero Trust in stages, allowing for learning and adjustment.
- Focus on User Experience: Design your Zero Trust implementation with user convenience in mind to minimize resistance.
- Automate Where Possible: Use automation to reduce the operational burden and improve consistency in policy enforcement.
- Continuous Education: Keep your team updated on Zero Trust principles and emerging best practices.
- Regular Testing: Conduct frequent penetration testing and security assessments to identify weaknesses in your Zero Trust implementation.
- Vendor Collaboration: Work closely with your technology vendors to ensure their solutions align with your Zero Trust strategy.
- Measure and Refine: Establish metrics to measure the effectiveness of your Zero Trust implementation and continuously refine your approach based on these metrics.
Case Study: Successful Zero Trust Architecture Implementation
Company: [redacted] (GFS)
Challenge: GFS was facing increasing cyber threats and struggling to secure its expanding digital infrastructure, which included on-premises systems, cloud services, and a large remote workforce.
Zero Trust Implementation:
| Phase | Description |
|---|---|
| Assessment and Planning |
|
| Identity and Access Management |
|
| Network Segmentation |
|
| Device Security |
|
| Data Protection |
|
| Application Security |
|
| Continuous Monitoring |
|
Results:
- 75% reduction in successful phishing attempts within the first year.
- 60% decrease in time to detect and respond to security incidents.
- Improved compliance with financial regulations due to enhanced data protection and access controls.
- Successful accommodation of remote work during the COVID-19 pandemic without compromising security.
Challenges Overcome:
- Initial user resistance was addressed through a comprehensive training program and gradual rollout.
- Legacy systems were either updated or isolated in secure enclaves with strict access controls.
- The high initial cost was justified by demonstrating improved security posture and operational efficiency.
Key Takeaways:
- A phased approach allowed for learning and adjustment throughout the implementation.
- Strong executive support was crucial for overcoming organizational resistance.
- Continuous improvement and adaptation of the Zero Trust model were necessary to address evolving threats.
Benefits of Zero Trust Architecture
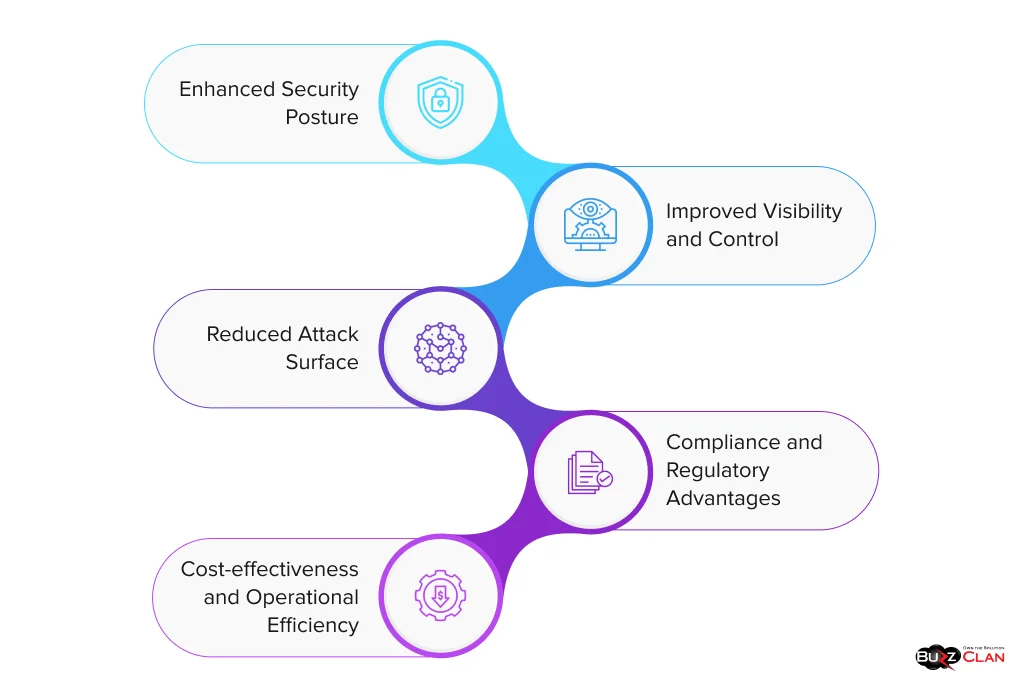
Zero Trust Architecture offers numerous benefits that extend beyond improved security. Understanding these advantages can help organizations justify the investment and effort required to implement this model. Let’s explore the key benefits in detail:
Enhanced Security Posture
- Reduced Attack Surface: Zero Trust significantly reduces the attack surface available to potential threats by implementing the principle of least privilege and micro-segmentation.
- Improved Threat Detection: Continuous monitoring and analytics enable faster detection of anomalies and potential security incidents.
- Limited Blast Radius: In a breach, micro-segmentation and strict access controls limit attackers’ potential damage and lateral movement.
- Protection Against Insider Threats: Zero Trust helps mitigate risks from malicious insider threats or compromised accounts by treating all users and devices as potentially hostile.
- Adaptive Security: Zero Trust’s context-aware policies allow for dynamic adjustment of security controls based on changing risk factors.
Improved Visibility and Control
- Comprehensive Network Insight: Zero Trust requires continuous network traffic monitoring, providing unprecedented visibility into user activities and data flows.
- Granular Access Control: With identity-based policies, organizations can implement fine-grained access controls at the individual user and resource levels.
- Centralized Policy Management: Zero-trust architectures typically feature centralized policy engines, allowing consistent policy enforcement across diverse environments.
- Real-time Risk Assessment: Continuous monitoring and analytics provide real-time insights into the organization’s security posture.
- Audit Trail: Comprehensive logging of all access attempts and network activities creates a detailed audit trail for forensics and compliance.
Reduced Attack Surface
- Minimized Exposure: By default, all resources are hidden and require explicit permission for access, significantly reducing exposure to potential attackers.
- Elimination of Trust Zones: Removing the concept of trusted networks eliminates vulnerabilities associated with flat network architectures.
- Proactive Risk Mitigation: Continuous verification and device health checks help identify and mitigate potential vulnerabilities before they can be exploited.
- Secure Remote Access: Zero Trust eliminates the need for traditional VPNs, reducing the attack surface associated with remote access.
Compliance and Regulatory Advantages
- Data Protection Regulations: Zero Trust’s strong data protection controls align well with GDPR, CCPA, and HIPAA regulations.
- Financial Services Compliance: The model’s strict access controls and comprehensive auditing capabilities support PCI DSS and SOX regulations compliance.
- Government and Defense Standards: Zero Trust aligns with government security standards like NIST SP 800-207 and the DoD Zero Trust Reference Architecture.
- Simplified Audits: Comprehensive logging and access controls make it easier to demonstrate compliance during audits.
- Privacy by Design: Zero Trust’s data-centric security approach supports privacy-by-design principles required by many modern regulations.
Cost-effectiveness and Operational Efficiency
- Reduced Incident Costs: Zero Trust can significantly reduce the costs associated with security incidents by preventing or limiting the impact of security breaches.
- Simplified Architecture: While the initial implementation may be complex, Zero Trust can lead to a more streamlined and manageable security architecture.
- Cloud Enablement: Zero Trust’s identity-centric approach facilitates secure cloud adoption, potentially reducing infrastructure costs.
- Improved Productivity: Zero Trust can provide remote workers with a more seamless and secure user experience.
- Resource Optimization: Fine-grained access controls and continuous monitoring allow for more efficient use of IT resources.
- Reduced Reliance on Perimeter Security: Zero Trust reduces the need for expensive perimeter security devices, potentially lowering hardware costs.
These benefits demonstrate that Zero Trust Architecture is not just a security model but a comprehensive approach to IT that can drive significant improvements in an organization’s overall operational efficiency, compliance posture, and risk management capabilities. While the journey to Zero Trust may be challenging, the potential rewards in enhanced security, improved operational efficiency, and reduced risk make it a compelling option for organizations of all sizes and industries.
Zero Trust Architecture Examples
Let’s examine some notable examples from leading technology companies to understand better how Zero Trust Architecture is implemented. These case studies demonstrate different approaches to Zero Trust and highlight its adaptability to various organizational needs.
Google’s BeyondCorp
Google’s BeyondCorp is one of the most well-known and comprehensive implementations of Zero Trust principles. Developed in response to sophisticated state-sponsored attacks, BeyondCorp represents a complete shift from the traditional perimeter-based security model.
Key features of BeyondCorp:
- Device Inventory Database: Maintains a real-time inventory of all devices accessing corporate resources.
- Device Security Policy: Enforces minimum security standards for all devices.
- User and Group Database: Centralized management of user identities and access rights.
- Access Control Engine: This engine makes real-time decisions about resource access based on user identity, device state, and other contextual information.
- Reverse Proxy: Acts as a Policy Enforcement Point for all access requests.
- Single Sign-On: Provides a seamless user experience across all applications.
Impact:
- Eliminated the need for VPNs, even for remote workers.
- Improved security posture by removing implicit trust in the corporate network.
- Enhanced user experience through consistent access policies regardless of location.
Microsoft’s Zero Trust Model
Microsoft has embraced Zero Trust in its internal security practices and as a framework for its customers. Their approach focuses on verifying explicitly, using least privilege access, and assuming breach.
Key components of Microsoft’s Zero Trust model:
- Azure Active Directory: Provides identity and access management capabilities.
- Microsoft Intune: Manages device compliance and conditional access policies.
- Azure Information Protection: Classifies and protects sensitive data.
- Microsoft Defender for Endpoint: Offers advanced endpoint protection and EDR capabilities.
- Azure Sentinel: SIEM and SOAR threat detection and response platform.
Impact:
- Improved security posture across Microsoft’s diverse product ecosystem.
- Enabled customers to implement Zero Trust principles using familiar Microsoft tools.
- Demonstrated the scalability of Zero Trust for large, complex organizations.
Zscaler’s Zero Trust Exchange
Zscaler, a cloud security company, built its business model around Zero-Trust principles. Its Zero Trust Exchange is a cloud-native security platform that connects users, devices, and applications using business policies over any network.
Key features of Zscaler’s Zero Trust Exchange:
- Cloud-Native Architecture: Eliminates the need for traditional network security appliances.
- Direct-to-Cloud Connectivity: Users connect directly to applications, not to the network.
- Proxy-Based Content Inspection: All traffic is inspected for threats and data protection.
- Policy-Based Access Control: Granular policies determine access to specific applications and data.
- Integrated Threat Prevention: Includes cloud firewall, sandboxing, and browser isolation.
Impact:
- Demonstrated the effectiveness of a cloud-native Zero Trust approach.
- Simplified security architecture for many organizations by eliminating on-premises security appliances.
- Provided a scalable solution for securing remote and mobile workforces.
As we can see from these examples, successful implementation of Zero Trust often involves:
- A strong focus on identity and device management
- Granular, policy-based access controls
- Continuous monitoring and risk assessment
- Integration of multiple security technologies into a cohesive framework
- A shift away from network-centric to data and identity-centric security models
Zero Trust Architecture in Different Sectors
Zero Trust Architecture is not limited to technology companies; it’s being adopted across various sectors due to its effectiveness in addressing modern security challenges. Let’s explore how Zero Trust is implemented and how it impacts different industries.
Enterprise Applications
Enterprises across industries adopt Zero Trust to secure increasingly complex and distributed IT environments.
Key focus areas:
- Hybrid and Multi-Cloud Security: Zero Trust helps secure workloads across on-premises, public, and private cloud environments.
- Remote Work Security: With the rise of remote work, Zero Trust provides a secure way to access corporate resources anywhere.
- Shadow IT Mitigation: Zero Trust helps address risks associated with unauthorized software use by focusing on securing data and applications rather than networks.
- Third-Party Access Management: Zero Trust principles enable more secure and granular control over vendor and partner access to corporate resources.
Example: A global manufacturing company implemented Zero Trust to secure its geographically distributed operations, resulting in a 40% reduction in security incidents and improved collaboration across international teams.
Government and Military (DoD Zero Trust Reference Architecture)
Government and military organizations increasingly adopt Zero Trust to protect sensitive information and critical infrastructure.
Key aspects of the DoD Zero Trust Reference Architecture:
- Pillars: User, Device, Network/Environment, Application and Workload, Data.
- Capabilities: Visibility and Analytics, Automation and Orchestration, Governance.
- Zero Trust Principles: Never trust, always verify; Assume breach; Verify explicitly.
Impact:
- Enhanced protection of classified information and critical systems.
- Improved ability to detect and respond to sophisticated state-sponsored attacks.
- Greater flexibility in supporting secure remote work for government employees.
Example: The U.S. Department of Defense is implementing its Zero Trust strategy to enhance cybersecurity across its vast and complex IT infrastructure.
Healthcare
The healthcare sector is adopting Zero Trust to protect sensitive patient data and comply with stringent regulations like HIPAA.
Key focus areas:
- Medical Device Security: Zero Trust helps secure the growing number of connected medical devices.
- Telemedicine Security: Enables secure remote patient consultations and data sharing.
- Research Data Protection: Secures valuable intellectual property and research data.
- Patient Data Privacy: Ensures that patient data is accessed only by authorized personnel for legitimate purposes.
Example: A large hospital network implemented Zero Trust, resulting in a 60% reduction in data breaches and improved compliance with HIPAA regulations.
Financial Services
Financial institutions leverage Zero Trust to protect sensitive financial data and combat sophisticated cyber threats.
Key applications:
- Transaction Security: Ensures that every financial transaction is authorized and authenticated.
- Customer Data Protection: Safeguards customer personal and financial information.
- Regulatory Compliance: Helps meet regulations requirements like PCI DSS, SOX, and GDPR.
- Fraud Prevention: Continuous monitoring and authentication help detect and prevent fraudulent activities.
Example: A global bank implemented Zero Trust principles across its digital banking platform, which reduced fraud attempts by 70% and improved customer trust.
Across these sectors, we see common themes in Zero Trust implementation:
- Identity-Centric Security: Focusing on user and device identity rather than network location.
- Data Protection: Emphasizing the security of data itself, regardless of where it resides.
- Continuous Monitoring: Implementing real-time monitoring and analytics to detect anomalies quickly.
- Micro-Segmentation: Dividing networks into small, isolated segments to limit the impact of potential breaches.
- Least Privilege Access: Granting users only the minimum level of access necessary for their roles.
NIST Zero Trust Architecture
The National Institute of Standards and Technology (NIST) has played a crucial role in formalizing and standardizing Zero Trust Architecture. NIST Special Publication 800-207, released in August 2020, provides a comprehensive framework for understanding and implementing Zero Trust Architecture. Let’s explore the key aspects of NIST’s approach to Zero Trust.
Overview of NIST Special Publication 800-207
NIST SP 800-207 offers a vendor-neutral, technology-agnostic approach to Zero-Trust Architecture. It provides organizations with a conceptual framework and general deployment models to guide their Zero-Trust journey.
Key aspects of the publication:
- Definition: NIST defines Zero Trust as “a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised.”
- Tenets: The document outlines seven tenets of Zero Trust, including the assumption that no network is inherently trusted and that all communication should be secured regardless of network location.
- Logical Components: This section describes the logical components of a Zero-Trust Architecture, providing a common language for discussing and implementing Zero-Trust.
- Deployment Models: The publication outlines several deployment models for Zero Trust Architecture, acknowledging that there’s no one-size-fits-all approach.
NIST Zero Trust Architecture Components
NIST SP 800-207 defines several key components of Zero Trust Architecture:
Policy Engine (PE):
- The brain of the Zero Trust Architecture.
- Makes and logs access decisions based on enterprise policy and information from external sources.
Policy Administrator (PA):
- Responsible for establishing and shutting down the communication path between a subject and a resource.
- Generates session-specific authentication and authorization tokens.
Policy Enforcement Point (PEP):
- Enables, monitors, and terminates connections between a subject and an enterprise resource.
- Relays requests from subjects to the PA and requires a token before allowing access.
Continuous Diagnostics and Mitigation (CDM) System:
- Collects data about enterprise assets, their state, and security posture.
- Provides the Policy Engine with up-to-date information to make access decisions.
Industry Compliance System:
- Ensures that the enterprise remains compliant with any regulatory standards.
- Informs the Policy Engine of any changes that would affect access decisions.
Threat Intelligence Feed(s):
- Provide information about new threats and vulnerabilities.
- Help the Policy Engine make more informed decisions based on the current threat landscape.
Network and System Activity Logs:
- Provide real-time feedback on the current state of enterprise assets.
- Used by the Policy Engine to make access decisions and by security analysts for threat hunting.
Data Access Policies:
- Define the attributes and access privileges required to access enterprise resources.
- Consumed by the Policy Engine to make access decisions.
Public Key Infrastructure (PKI):
- Provides and manages cryptographic keys for the enterprise’s components.
- Ensures secure communication between components.
ID Management System:
- Creates, stores, and manages enterprise user accounts and identity records.
- Provides the Policy Engine with information about subjects requesting access to resources.
How NIST Guidelines Shape Zero Trust Implementation
The NIST guidelines have had a significant impact on how organizations approach Zero Trust implementation:
Common Framework:
- NIST SP 800-207 provides a standardized framework for discussing and implementing Zero Trust.
- This common language helps organizations align their efforts and communicate more effectively with vendors and partners.
Technology-Agnostic Approach:
- NIST’s vendor-neutral stance allows organizations to implement Zero Trust using various technologies and solutions.
- This flexibility enables organizations to leverage existing investments while adopting a Zero Trust model.
Risk-Based Implementation:
- NIST emphasizes the importance of risk assessment in Zero Trust implementation.
- Organizations are encouraged to prioritize their Zero Trust efforts based on their specific risk profiles and critical assets.
Continuous Monitoring and Improvement:
- The NIST model emphasizes continuous monitoring and adjustment of Zero Trust policies.
- This aligns with the dynamic nature of modern IT environments and evolving threat landscapes.
Integration with Existing Standards:
- NIST’s Zero Trust guidelines integrate well with other NIST cybersecurity frameworks, such as the Cybersecurity and Risk Management Framework.
- This integration helps organizations incorporate Zero Trust into their broader cybersecurity strategies.
Government Adoption:
- The U.S. government’s adoption of NIST guidelines has accelerated Zero Trust implementation in the public sector.
- This, in turn, has influenced private sector adoption, particularly among government contractors and regulated industries.
Emphasis on Data Protection:
- NIST’s focus on protecting data, rather than just network perimeters, has shifted organizational thinking toward data-centric security models.
Scalability Considerations:
- NIST guidelines address the challenges of implementing Zero Trust in large, complex environments.
- This has helped enterprises understand how to scale Zero Trust across their organizations.
Maturity Model:
- While not explicitly defined in SP 800-207, NIST’s approach allows organizations to implement Zero Trust in stages, moving from basic to advanced implementations over time.
Compliance Alignment:
- NIST’s Zero Trust model aligns well with various compliance requirements, helping organizations meet regulatory obligations while enhancing their security posture.
The NIST Zero Trust Architecture guidelines have become a cornerstone for many organizations’ Zero Trust initiatives. By providing a comprehensive, flexible framework, NIST has helped demystify Zero Trust and make it more accessible to various organizations. As the Zero Trust landscape continues to evolve, we can expect NIST to update and refine its guidelines, further shaping the future of cybersecurity.
Future of Zero Trust Architecture
As cyber threats evolve and digital transformation accelerates, Zero Trust Architecture is poised to play an increasingly crucial role in cybersecurity. Let’s explore the emerging trends, integration with advanced technologies, and predictions for the evolution of Zero Trust.
Cloud-Native Zero Trust:
- As organizations migrate to the cloud, we’re shifting towards cloud-native Zero Trust implementations.
- This trend focuses on securing cloud workloads, containers, and serverless architectures using Zero Trust principles.
Zero Trust Network Access (ZTNA):
- ZTNA is gaining traction as a replacement for traditional VPNs, offering more granular access control and improved security for remote workers.
Identity-Centric Security:
- There’s an increasing focus on identity as the new perimeter, with advanced identity and access management (IAM) solutions becoming central to Zero Trust strategies.
Continuous Authentication:
- Beyond multi-factor authentication, we’re moving towards continuous authentication methods that verify user identity throughout a session.
DevSecOps Integration:
- Zero Trust principles are being incorporated into the DevSecOps pipeline, ensuring security is built into applications and infrastructure from the ground up.
Zero Trust for IoT:
- As the Internet of Things (IoT) expands, there’s a growing need to apply Zero Trust principles to secure the vast network of connected devices.
Integration with AI and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are set to play a pivotal role in the future of Zero Trust Architecture:
Anomaly Detection:
- AI-powered systems can analyze vast network traffic and user behavior to detect anomalies that might indicate a security threat.
Adaptive Policies:
- Machine learning algorithms can help create and adjust access policies in real time based on changing risk factors and user behavior patterns.
Predictive Security:
- AI can analyze historical data and current trends to predict potential security threats before they materialize.
Automated Response:
- AI-driven systems can automate incident response, quickly containing threats and minimizing damage.
User and Entity Behavior Analytics (UEBA):
- Advanced AI algorithms can build detailed profiles of normal user behavior, making it easier to spot potentially malicious activities.
Natural Language Processing (NLP):
- NLP can analyze logs and security alerts, helping security teams quickly understand and respond to threats.
Predictions for Zero Trust Evolution
Here is all that you can look forward to with Zero Trust Evolution.
Ubiquitous Adoption:
- Zero Trust will become the de facto standard for cybersecurity across industries, driven by increasing cyber threats and regulatory pressures.
Standardization:
- We’ll likely see more standardization in Zero Trust implementations, with industry bodies and governments developing comprehensive Zero Trust frameworks and certifications.
Integration with Emerging Technologies:
- Zero Trust principles will be adapted to secure emerging technologies like 5G networks, edge computing, and quantum computing.
Enhanced User Experience:
- As Zero Trust technologies mature, we’ll see improvements in user experience, with security becoming more seamless and less intrusive.
Zero Trust Supply Chain:
- The principles of Zero Trust will extend beyond an organization’s boundaries to encompass entire supply chains and partner ecosystems.
Automated Zero Trust:
- AI and automation will play a larger role in managing Zero Trust environments, reducing the burden on security teams and improving response times.
Privacy-Enhanced Zero Trust:
- As privacy concerns grow, we’ll see Zero Trust models that better balance security needs with user privacy, possibly leveraging technologies like homomorphic encryption.
Zero Trust as a Service:
- More vendors will offer comprehensive Zero Trust solutions as a service, making it easier for smaller organizations to adopt advanced security measures.
Regulatory Alignment:
- Future regulations will likely align more closely with Zero Trust principles, mandating Zero Trust approaches in specific industries or for certain types of data.
Human-Centric Design:
- Zero Trust implementations will increasingly focus on human behavior and psychology, designing systems that are both secure and aligned with how people naturally work.
The future of Zero-Trust Architecture is dynamic and promising. As it evolves, we expect to see more sophisticated, automated, and user-friendly implementations that provide robust security in increasingly complex digital environments. Organizations that embrace these trends and adapt their Zero-Trust strategies accordingly will be well-positioned to face future cybersecurity challenges.
Conclusion
As explored throughout this comprehensive guide, Zero Trust Architecture represents a paradigm shift in cybersecurity, offering a more robust and adaptable approach to protecting modern digital environments. Let’s recap the key points and consider the critical role of Zero Trust in modern cybersecurity.
Recap of Key Points
Here is a quick review of the information we absorbed and understood in the blog.
Zero Trust Fundamentals:
- The core principle of “never trust, always verify” underpins all aspects of Zero Trust Architecture.
- Zero Trust assumes that no user, device, or network should be automatically trusted, regardless of location.
Components and Implementation:
- Successful Zero Trust implementation involves integrating various components, including strong identity management, micro-segmentation, and continuous monitoring.
- Organizations should approach Zero Trust as a journey, often starting with critical assets and expanding over time.
Benefits:
- Zero Trust offers enhanced security, improved visibility and control, a reduced attack surface, and better alignment with regulatory requirements.
- It also provides operational benefits, including improved user experience for remote workers and more efficient use of IT resources.
Industry Adoption:
- Zero Trust is being adopted across various sectors, from technology companies to government agencies, healthcare providers, and financial institutions.
- Each industry is adapting Zero Trust principles to address its specific security challenges and regulatory requirements.
Standards and Guidance:
- NIST SP 800-207 provides a comprehensive, vendor-neutral framework for understanding and implementing Zero Trust Architecture.
- This and other emerging standards are helping to shape and standardize Zero Trust implementations.
Future Trends:
- The integration of AI and machine learning, the shift towards cloud-native implementations, and the extension of Zero Trust principles to IoT and supply chains are key trends shaping the future of Zero Trust.
The Critical Role of Zero Trust in Modern Cybersecurity
Zero Trust Architecture is not just another security trend; it’s becoming a fundamental approach to cybersecurity in the digital age. Here’s why it’s critical:
Addressing Modern Threats:
- Zero Trust is designed to combat sophisticated cyber threats, including advanced persistent threats (APTs) and insider threats, which traditional perimeter-based security struggles to address.
Supporting Digital Transformation:
- As organizations embrace cloud computing, remote work, and IoT, Zero Trust provides a security model that aligns with these modern, distributed IT environments.
Improving Resilience:
- By assuming breach and implementing least-privilege access, Zero Trust helps organizations limit the impact of security incidents and recover more quickly.
Enhancing Compliance:
- Zero Trust principles align well with many regulatory requirements, helping organizations meet their compliance obligations more effectively.
Enabling Business Agility:
- Organizations can adopt new technologies and business models more confidently with a robust Zero Trust framework without compromising security.
Shifting Security Mindsets:
- Zero Trust encourages a proactive, risk-based approach to security, moving organizations away from reactive, perimeter-focused strategies.
Call to Action for Organizations to Adopt Zero Trust Principles
Given the critical role of Zero Trust in modern cybersecurity, organizations that haven’t yet embraced this approach should consider taking the following steps:
Assess Current Security Posture:
- Evaluate your security infrastructure and identify gaps that Zero Trust could address.
Develop a Zero Trust Strategy:
- Create a roadmap for implementing Zero Trust, prioritizing critical assets and high-risk areas.
Start Small and Iterate:
- Begin with pilot projects to gain experience and demonstrate value before rolling out Zero Trust more broadly.
Invest in Education:
- Ensure your IT and security teams are well-versed in Zero Trust principles and technologies.
Engage Stakeholders:
- Zero Trust impacts the entire organization. Engage business leaders, end-users, and IT staff in the transition.
Choose the Right Partners:
- Select vendors and service providers that align with your Zero Trust strategy and can support your long-term goals.
Embrace Continuous Improvement:
- Recognize that Zero Trust is an ongoing journey. Regularly assess and refine your approach as threats and technologies evolve.
In conclusion, Zero Trust Architecture represents a fundamental shift in how we approach cybersecurity. By embracing its principles, organizations can build more resilient, adaptive, and secure digital environments capable of meeting the challenges of today’s threat landscape and supporting tomorrow’s business needs. As cyber threats evolve and digital transformation accelerates, Zero Trust will play an increasingly critical role in safeguarding our digital future.

Get In Touch