How Vishing Attacks Work And Why Your Business Could Be At Risk?
Priya Patel
Nov 19, 2024
Did you know a whopping $39.5 billion was lost to phone scams in just one year?
While these numbers are enough to give careful consideration to developing robust security measures, staying ahead of scammers is not easy.
With each passing second, vishing (voice + phishing) attacks are getting more sophisticated.
And close to 20% of victims are aged 60 and above.
What is Vishing in Cybersecurity?
Vishing attacks are much more than your regular phone scams.
Hackers leverage Voice over Internet Protocol (VoIP) technology and caller ID spoofing to access sensitive personal and financial information.
In such attacks, hackers pretend to represent legitimate companies or organizations and urge victims to provide personal data such as passwords, credit card numbers, and other confidential information.
While awareness is a must, to keep up with hackers, you must understand their ideologies and have well-defined cybersecurity metrics in place.
Understanding the Purpose behind Vishing
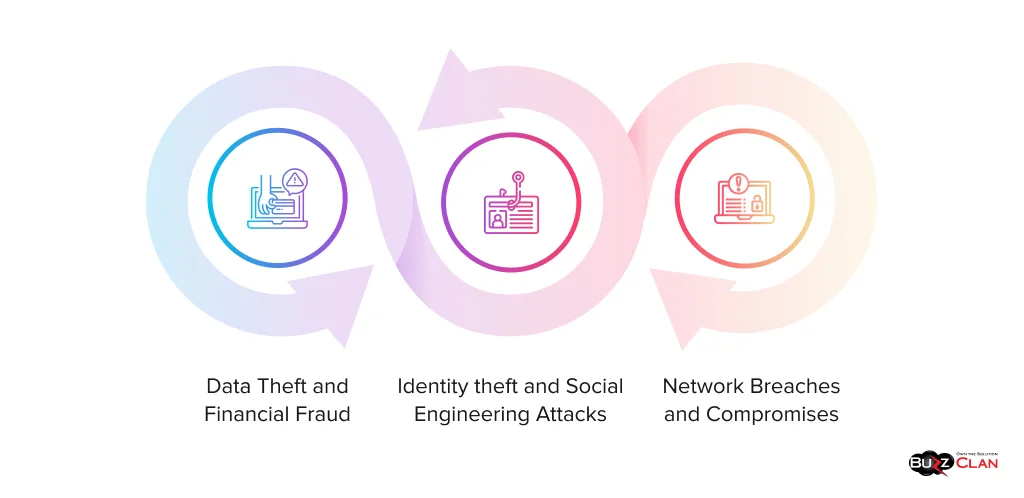
Before we can deal with vishing attacks, it is essential to understand the purpose behind them.
Data Theft and Financial Fraud
How often do we pay attention to warnings by banks and other service providers? While we can repeat the words verbatim, how frequently do we follow them? We usually end up disclosing financial information on calls or clicking on spammy links. And this invariably leads to financial fraud and even loans being taken in your name.
Identity Theft and Social Engineering Attacks
What if we hold you responsible for a crime you didn’t commit? No, we are not talking about homework. Vishers collect ample data from individuals under false pretexts and can commit multiple frauds. The consequences of this can be dire, and you might spend your precious time explaining things to authorities.
Network Breaches and Compromises
Sometimes, vishing attacks are just the tip of the iceberg. Now, what does this imply? These attacks are entry points for more extensive network breaches or compromises. Rather than targeting businesses in the first attempt, they weaken their foundation.
And how is that done? Well, the targets are employees who are lured into shelling out sensitive information. If they manage to extract data from them, you will need to face financial losses and legal liabilities in the long run.
Smishing vs. Vishing vs. Phishing: Key Differences
Smishing and vishing are commonly used tactics to dupe customers; the same is true of phishing. Unfortunately, hackers are getting more potent with each attempt.
| Parameters | Vishing | Phishing | Smishing |
|---|---|---|---|
| Method | Use phone calls or VoIP to trick victims into divulging personal information. | Send e-mails or create fake websites to dupe victims and download malware. | Use text messages to gain access to confidential and financial information. |
| Purpose | Banks, government agencies, unsuspecting individuals | Businesses, individuals, banks, and service providers | Individuals, employees, and service providers |
| How it works | Hackers pose as bank officials, claim suspicious activity on your account, and request verification of account details. | Mails that look legitimate and urge you to click on links and enter confidential data. | Inform users of a delivery requiring payment confirmation by clicking a spammy link. |
How are Vishing Attacks Planned?
Now that you know the purpose behind vishing attacks, let’s understand how they are carried out.
Extracting Phone Numbers via Emails
Hackers extract your email IDs and lure you into giving your phone numbers.
Calling Attempts
If you get tricked by a phishing email, the probability of receiving a phone call is high. Seasoned hackers may leverage phishing and vishing to fake area codes to gain trust, as you are more likely to pick up calls that come from local areas. In this case, avoidance is the best virtue.
Yes, you may be skeptical of missing out on crucial information. However, legitimate sources have well-defined and structured ways of intimating you. Under no circumstances will they ask you to share confidential data via any form.
Did you know that 35% of victims do not report the incident because a feeling of guilt overrides them? Unfortunately, not reporting for any reason encourages scammers to hone their skills and continue their pursuits.
Final Showdown
Help us with a question. What would you do if we did all the research for your designated job? You will get to work and give your best attempt at the given task. Unfortunately, the same is the case with scammers. They go the extra mile to make purchases; some even empty your entire bank account.
9 Common Vishing Examples
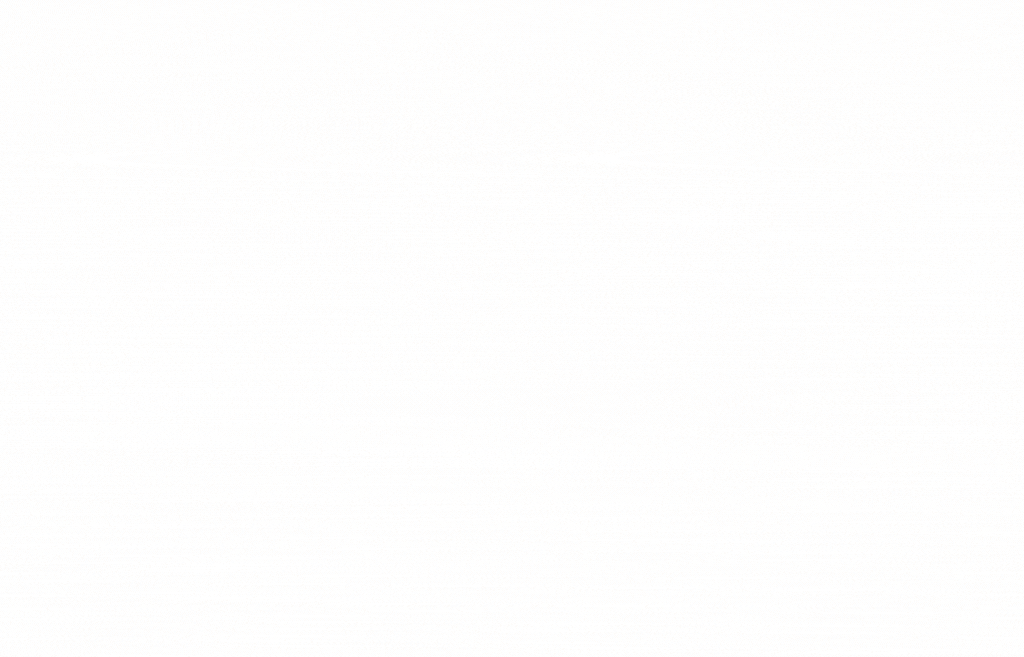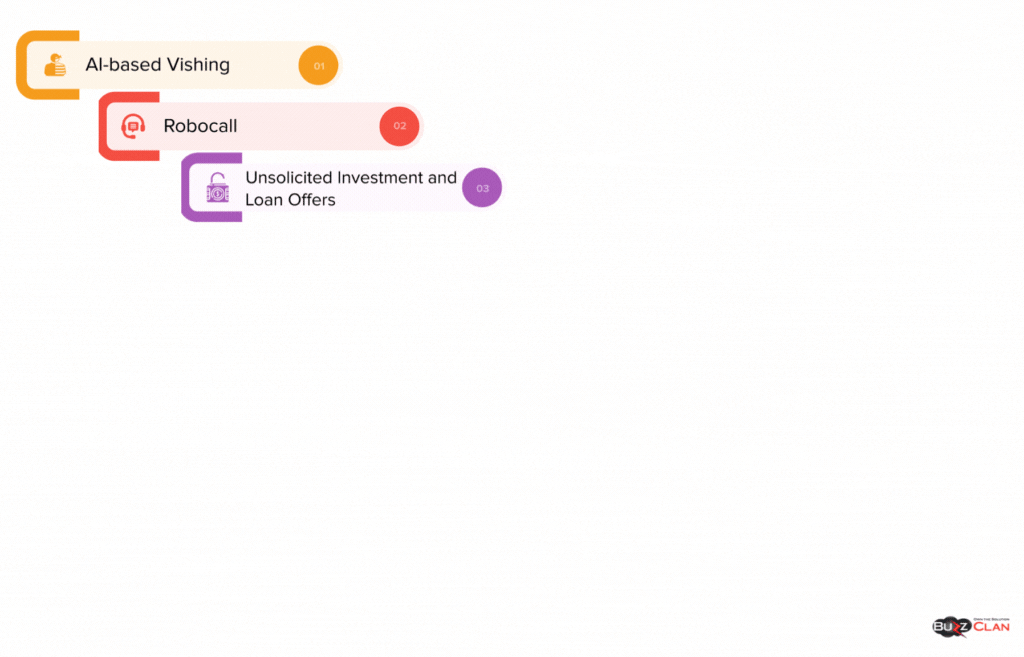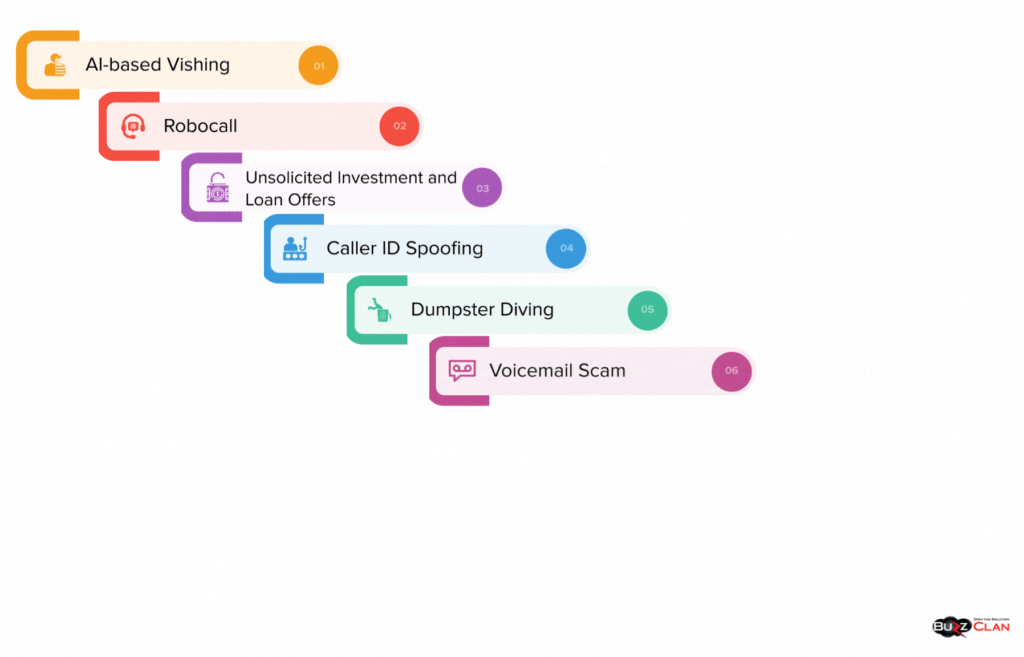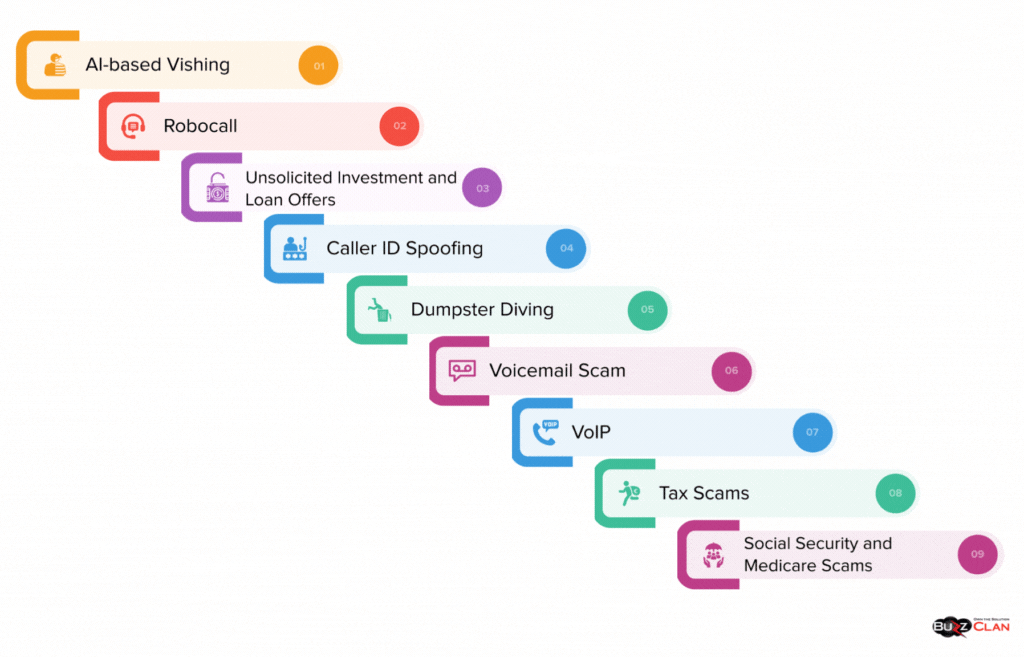
If versatility had a name, it had to be vishing! Jokes apart, vishing is carried out in both manual and automated ways. However, the consequences in both cases are devastating. Some of the common vishing examples include:
AI-based Vishing
Scammers use free AI voice tools to develop sound boards, conduct live conversations, and answer customers with advanced credibility.
Robocall
These involve using computer-generated audio or prerecorded messages to trick victims.
VoIP
Scammers use VoIP to create multiple numbers and expedite their attacking attempts. While VoIP was designed to support call center operations, it has become a preferred tool for scammers.
Caller ID Spoofing
Scammers use dark web solutions to modify caller IDs and trick victims into believing the calls are from legitimate entities. Often, these caller IDs are so convincing that users get tricked quickly.
Dumpster Diving
This method is mainly used against businesses. It involves extensive digging through the company’s trash to find personal data. For example, obtaining information on employee names or how a company organizes invoices.
Voicemail Scam
The boring old voicemail is hackers’ favorite weapon. They usually hunt for companies that use voice-to-text software for voicemails. Once they have a list, they share emails with malicious links suggesting you have voicemails.
Unsolicited Investment and Loan Offers
What if we told you we could cancel your debt in an instant? It sounds too good to be true. Well, scammers are just better at marketing this! Quick-get-rich schemes that need you to act in milliseconds and even pay an amount are classic vishing scams. Legitimate vendors will avoid making optimistic offers and thoroughly check your credit history.
Social Security and Medicare Scams
Old is gold. Yes, this is the raw truth about Social Security and Medicare scams. Scammers often pose as representatives and target the elderly. A common tactic is to steal Medicare or Social Security numbers or threaten to stop benefits. They use the stolen information to steal money or redirect gains if they succeed.
Tax Scams
Issues in tax returns are expected. Even the best of us are prone to mistakes. Imagine getting a message that there are issues with your tax returns from seemingly legitimate sources. Chances are you will believe it. This is where the scammers play with your sentiments and take out sensitive information.
Experienced a Vishing Attack? Here is What Needs to be Done
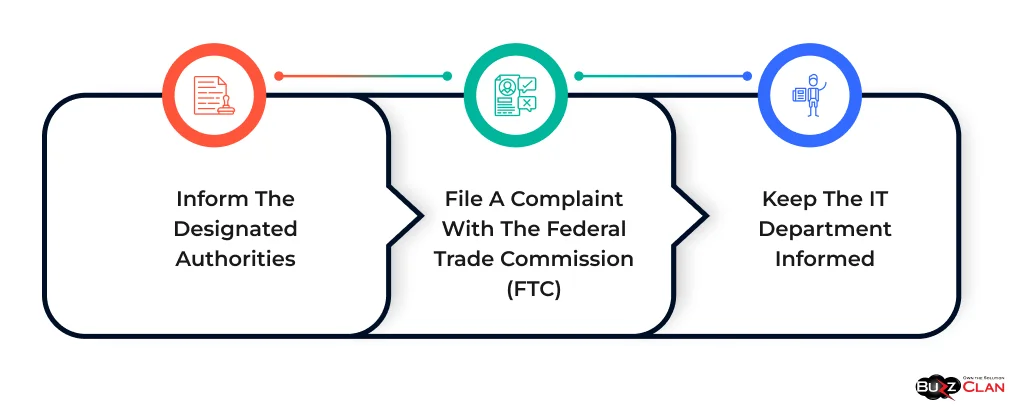
Follow these steps to reduce the blow:
Inform the Designated Authorities
While it is normal to panic, the first step is to alert your financial institution and request that they freeze your account. The next step is to change your passwords with zero delays.
File a Complaint With the Federal Trade Commission (FTC)
Informing the FTC is a must to protect other individuals from getting scammed.
Keep the IT Department Informed
If you have disclosed sensitive information, contact your IT department so that they can take the necessary action. Vishing and other cybercrimes will continue to exploit the public as long as scammers are creative. However, we can’t leave everything to fate. Investing time in understanding vishing attacks can significantly lessen the collateral effect.
How to Protect Your Business from Vishing Attacks?
75% of businesses have lost money to voice scams, with costs exceeding $14 million per business year. Here is how you can protect your business from vishing attacks.
Train Employees on Keeping Sensitive Information Secure
Sticking to the basics always helps. There are no complex interpretations. All you need to do is ensure your employees are trained enough to prevent vishing attacks. Let’s suggest some weapons, aka tools, to ensure seamless awareness, such as monthly training and sharing power-packed solution-oriented emails.
Stronger Passwords and 2-Factor Authentication
How often did your close ones guess your passwords? We are sure you have lost count. However, be practical: scammers are skilled and wise enough to guess passwords. Is there a solution? Yes, simplicity is the key. No, we are not contradicting our statements. Just ensure your passwords combine special characters that are harder to guess. Wish to go ahead? Make 2-factor authentication a must for all employees.
Call Blocking and ID Tracking to Rescue
You might think that your block list is never-ending. We suggest you act on your thoughts, start making a list longer, and track caller IDs as you would care for your loved ones. Yes, it seems too much for the time being. However, this will save you from identity theft in the short and long run.
Safeguard Data with Multi-Level Security
Just like our homes, we need to guard our data creatively. Luckily, nothing overly creative and precise has to be done. All you need to do is make access difficult for hackers. Remember, damage can only be done when they obtain sensitive data. Without any information, they are helpless.
Track Telephone Networks
When monitoring your networks for suspicious attempts, you can proactively identify and combat vishing attacks. But how do you prevent them? You can do it by automating the process of tracking spam calls and warning users via notifications of suspicious attempts to gain confidential data.
Train and Educate Users on Attacking and Prevention Methods
Your job doesn’t involve employee training. You are also responsible for customer awareness. Customers who understand the dynamics behind vishing attacks are less prone to fraud
Use Voice Biometrics for Access Management
Authenticating users with their voice is a great way to prevent attackers from accessing confidential data.
Verification Codes as a Savior
We are often requested to add OTPs when we need to log in to portals. The same is true for verification codes. You can ask callers to enter their registered numbers and verification codes whenever you receive calls. Are you worried about making things difficult for your customers/callers? Trust us; they will thank you later for adhering to the best security practices.
Add your Numbers to the Do Not Call Registry
Adding numbers to the list means permanently saying goodbye to telemarketing calls. But does this mean you are safe from all scams? The answer is a big “No.” Scammers can still target you. Staying alert is the ultimate solution.
Summing Up
Despite preventive measures, we can be victims of hybrid vishing attacks, which have surged by 554% in volume. Multi-factor authentication and robust VoIP systems are potent solutions, but nothing beats awareness and intuition. Cybersecurity training is no longer a luxury but a necessity to safeguard personal information.
FAQs

Get In Touch
Follow Us
Table of Contents
- What is Vishing in Cybersecurity?
- Understanding the Purpose behind Vishing
- Smishing vs. Vishing vs. Phishing: Key Differences
- How are Vishing Attacks Planned?
- 9 Common Vishing Examples
- Experienced a Vishing Attack? Here is What Needs to be Done
- How to Protect Your Business from Vishing Attacks?
- Summing Up
- FAQs





