Top Cybersecurity Threats for Businesses: Complete Protection Guide 2026
Deepak Dube
Sep 30, 2025
Did you know that the cost of cybercrime is slated to reach $24 trillion by 2027? With the cybersecurity workforce shortage reaching a record-high gap of 4 million unfilled positions globally, businesses need to be strategic about their data. Cybersecurity threats for businesses are growing exponentially. Unfortunately, two-thirds of cybersecurity professionals report that their organizations need more resources to prevent and troubleshoot security issues.
So, how can you prevent cybersecurity threats while addressing organizational challenges and making a mark in the ever-competitive world? While achieving all this is not easy, the first step is to develop a solid understanding of cybersecurity threats to businesses and organizations, analyze the impact of these threats, and utilize the right tools to automate processes. Before we begin the journey, let’s first understand what a cyber attack entails.
What Are Cybersecurity Threats?
Cybersecurity threats for businesses include all risks or dangers that target their data, systems, and networks with the intention of financial gain, disrupting operations, or causing reputational damage. The primary reasons for these threats are hackers, accidental employee mistakes, or malware. Many businesses have faced lawsuits or penalties for failing to protect sensitive customer information, resulting in lost customers.
Top Common Cybersecurity Threats for Businesses
Here is a list of common cybersecurity threats for businesses, along with tips on how to avoid them.
Phishing
A classic case of trust exploitation, phishing involves hackers sending fake emails pretending to be a legitimate authority. However, the scenario is entirely different. They only do it to gain access to passwords or get card details. For the same reason, they often create panic by sending emails about immediate account deactivation, and they usually succeed in their pursuits. To prevent such attacks, you must double-check incoming requests and use email filters to block such messages. Also, train your employees to recognize such emails immediately and direct them to spam.
Ransomware
One of the most common and detrimental attacks, ransomware encrypts your files, rendering them useless, and demands money to unlock them. Despite multiple warnings and training, numerous businesses have lost millions of dollars because they didn’t have the proper security measures. To ensure you are not a part of such hacks, back up your data regularly to keep it offline and use strong firewalls and endpoint protection. Nothing tops vigilance, so train your employees to avoid clicking suspicious links or attachments.
Denial of Service (DoS) Attacks
Such attacks are common during sales or significant events. Hackers purposely overload a website with traffic, causing it to crash. While you may think the crash was due to heavy traffic, it is not. Not only will you go offline, but you will also be unable to rectify these issues in real-time. To ensure such problems don’t hamper your reputation by creating chaos at peak hours, install top-notch DoS protection tools. Not only will they ward off such attacks, but they will keep you updated on any suspicious attempts. The second thing you need to do is use a Content Delivery Network (CDN) to handle high traffic. Lastly, ensure you work with your hosting provider to put the proper measures in place.
SQL Injection
In such attacks, hackers try to exploit vulnerabilities in a website’s database. If they are successful in their attempts, they inject malicious code into login forms and can easily steal your data. Such attacks are common, and businesses worldwide have lost millions of dollars. This makes it a must to curb this menace. To prevent such attacks, you must restrict user permissions for sensitive databases and regularly test and patch web applications. Another essential measure is to use parameterized queries in your database, which will help you prevent these attacks before they can cause any damage.
Password Attacks
While businesses often advise their employees to use strong passwords, only a few actually do. Unfortunately, this leads to hackers guessing or stealing passwords by brute force. This, in turn, can lead to huge losses as hackers can further invade systems and gain access to sensitive financial data. What can be done to better deal with such attacks? Simple things like multi-factor authentication can significantly eliminate issues. If your employees complain of not remembering complex passwords, ask them to use password managers.
Insider Threats
While some of your employees may not know the best cybersecurity practices, some may deliberately misuse their access to harm your data. In both cases, sensitive company information will be leaked, resulting in financial losses and a damaged reputation. Therefore, it is crucial to utilize role-based access controls or restrict access to sensitive data. You must monitor user activities for unusual behavior and regularly conduct cybersecurity training.
Zero-Day Exploits
Application versions can have vulnerabilities as you update them or modify some features. However, these issues have become breeding grounds for criminals. They discover these loopholes and install malware. Once they have done that, they plan complex attacks, resulting in heavier losses. To protect your systems, make sure you always keep your software and systems up to date. Additionally, if your IT team is overwhelmed with work, consider partnering with vendors to provide quick patches for vulnerabilities. Lastly, investing in solid intrusion detection systems will help you stay ahead of the game by monitoring unusual activities.
Inadequate Post-Attack Procedures
Tell us something. What would you do once you have faced a data breach? You would take extra precautions and patch any loopholes in your software to prevent another attack. However, this is not the case for all organizations. They ended up facing attacks within the same year. The solution is to patch your systems and upgrade them regularly. Many businesses are thus adopting Patching-as-a-Service products to stay consistent with updates and patches. Additionally, automated patching will significantly reduce the likelihood of patching issues caused by human errors.
Social Engineering
Fear is a commonly exploited emotion, and hackers know how to use it. In social engineering attacks, hackers often trick your employees into giving sensitive information. They may pretend to be your IT support and ask for login credentials. Also, they may fake urgency from higher management, and your employees will have no choice but to give in. Thus, to prevent such attacks, ensure that you provide your employees with ample and regular training. This will help them verify requests and only comply with the legitimate ones. Additionally, make it a must to use multi-factor authentication, as it will add an extra layer of security and prevent the sharing of sensitive information over the phone or email.
Internet of Things
While IoT is claimed to be one of the most groundbreaking technologies of the 21st century, it also acts as a gateway to unforeseen cyber threats. The COVID-19 pandemic saw many businesses and people investing in IoT devices. However, there have been millions of cyberattacks on IoT devices recently. These devices are vulnerable to attacks, so they don’t have the same security measures as other devices. Use separate networks and strong encryption to protect your systems and prevent such attacks. Also, firewalls can monitor and control traffic to and from IoT devices.
Poor Data Management
While organizations worldwide invest a fortune in data protection and management, they must realize that it is much more than keeping the data organized. As time passes, the amount of data consumed by consumers doubles, which can lead to confusion and missed opportunities. Moreover, it can also make sensitive information vulnerable to cyberattacks. To ensure you are not a victim of such an attack, ensure you have a strategic data management plan. This plan can protect your systems, prevent business interruption, and avoid fines.
Deepfake Attacks
Accenture’s Cyber Intelligence (ACI) report suggests that criminals are willing to spend a fortune for higher-quality deepfakes, with prices hitting $20,000 per minute for high-quality videos. The opposite is valid in a world where AI makes lives more manageable. Deepfakes are being used to create videos, audio, and texts that can pass even the most scrupulous eyes, leading to losses of millions. One of the most shocking incidents was when the Hong Kong Bank reported losses worth $25 million, all due to a deepfake scam. The scammers smartly recreated the company’s CTO on a conference call and instructed the employees to transfer money.
As technology advances, such instances will rise. The only way out is to invest in advanced AI detection tools that identify deepfakes. Some of the popular names include Microsoft Video Authenticator and Deepware Scanner. You can also partner with a blockchain expert to develop a use case to embed digital signatures in authentic video and audio files. This way, scammers will not be able to carry out their objectives. Lastly, you must develop a robust strategy to counter deepfake attacks.
AI/ML-Based Threats
While AI and ML have been trailblazers in improving cybersecurity defences, they have also introduced new threats. Attackers use AI to automate cyber attacks and ML to enable real-time malware adaptation. Another cause of concern is model inversion attacks, where ML models are reverse-engineered to extract sensitive data. To combat such attacks, you need to shake hands with AI-driven threat intelligence and adversarial ML defenses, and make continuous model monitoring a part of your security posture to detect anomalies and mitigate AI-enhanced cyber risks.
Edge Computing Security Challenges
Since edge devices operate outside traditional network perimeters, they are more prone to cyber threats. The worst part is that since these nodes have limited computational power, it becomes difficult to implement strong encryption or advanced security protocols. Attacks have launched multiple DDoS attacks or data manipulation exploits on such devices in the past decade. To mitigate these risks, you should implement endpoint detection and response (EDR), lightweight encryption protocols, and automated patch management to safeguard edge computing environments from evolving cyber threats.
Supply Chain Security Risks
Cyber threats targeting the supply chain have risen in the past few years. These attacks can lead to large-scale disruptions, data breaches, and even nation-state cyber espionage. The primary cause of concern is supply chain poisoning, where adversaries inject malicious code into trusted software components that reach end-users. To ensure such issues don’t hamper your operations, enforce vendor risk assessments, strict code signing practices, and continuous security monitoring to detect and mitigate potential compromises before they escalate into full-scale attacks.
Impact of Cybersecurity Threats on Businesses
Cybersecurity threats can drain businesses in multiple ways and even permanently put them out of operation. Let’s understand how your business is impacted after a data breach.
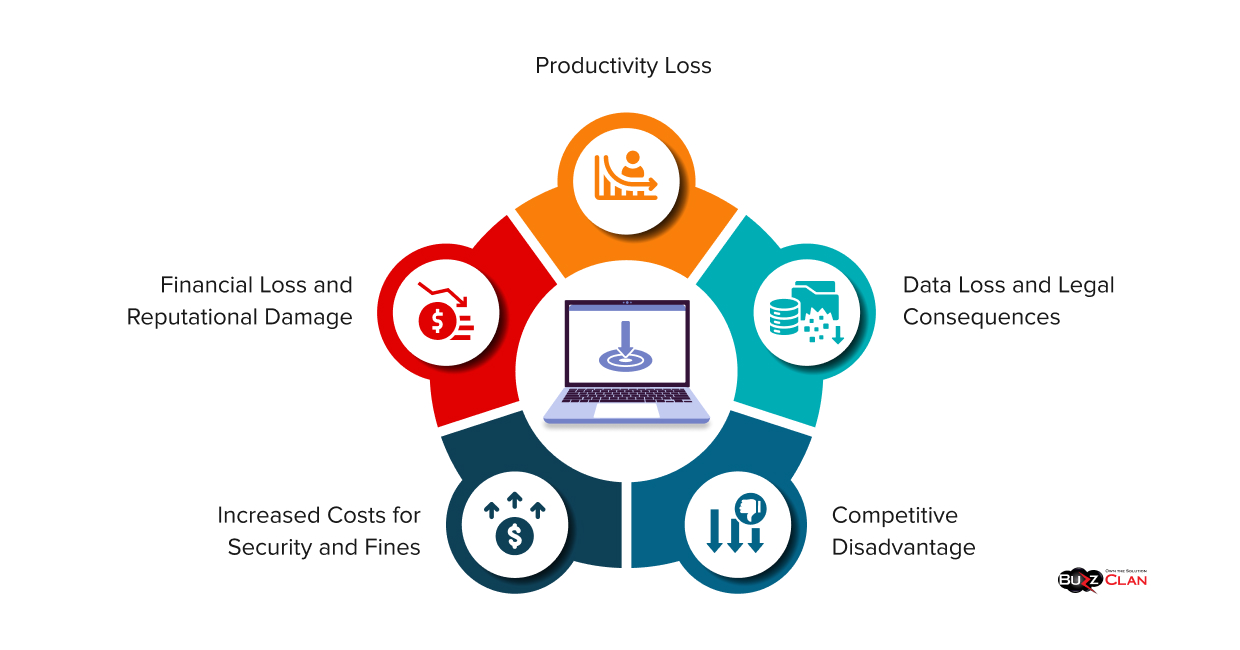
Financial Loss and Reputational Damage
Every year, businesses lose millions of dollars due to cyberattacks. Hackers demand thousands of dollars to return data rights; even if you choose not to pay them, recovering data is costly. Not only does it lead to a loss of trust, but it can also result in the loss of your well-earned clientele. This makes it all the more crucial to be well-versed in cybersecurity practices and implement them effectively.
Data Loss and Legal Consequences
You will face many fines and lawsuits if you fail to protect customer data. Legal expenses will only add to the burden and may burn a hole in your pocket. Also, recovering the money and resources will take a reasonable amount of time. In some cases, you may need to delete your data and accept the associated losses permanently. This may also mean a permanent shutdown of your business. Therefore, make it a point to employ cybersecurity best practices and safeguard your company against threats.
Competitive Disadvantage
All your efforts go in vain once you face a data breach. Now, you may say that you had backups and didn’t pay a single penny as ransom. Well, there is much more than money when running a business. A data breach can expose your plans and trade secrets to your competitors. Once they know that, they can use it to their advantage. Also, losing your position in the market can take years and even decades to recover.
Increased Costs for Security and Fines
Once you have dealt with the aftermath of a data breach, you must ensure that such incidents do not happen again. For the same, you need to invest in cybersecurity tools and expert guidance to detect threats beforehand. Also, you are repeating a big mistake if you think you can save money by not investing in them. Businesses that fail to follow cybersecurity regulations may face fines or have their licenses revoked.
Productivity Loss
Employees will be left with no work if your systems are not in perfect condition and have been locked down due to breaches. As a result, they will miss deadlines, and you will not be able to operate your business at the previous efficiency level. Moreover, all upskilling initiatives will go down the drain as your time will be spent dealing with the consequences of the breach.
Further Reading
Cybersecurity Strategies for Businesses
You need a solid plan to protect your data and systems from cyberattacks. To achieve this, you will need to develop a strategy. Here is how to make one.
Using Strong Passwords and Multi-Factor Authentication (MFA)
Did you know many companies require employees to sign in to their email IDs weekly? This is because they understand the importance of multi-factor authentication. The lesson here is to learn from these companies, ensure that all your employees’ passwords are complex, and enable multi-factor authentication. Using password managers will help your employees create unique passwords and keep their data safe.
Ensure Regular Data Backups
You must have heard this many times before that prevention is always better than a cure. Similar is the case with data back-ups. Even if you have the best systems at your fingertips, they can be attacked, and you can lose your precious data quickly. In the worst-case scenario, if you become a victim of a ransomware attack, you can quickly restore your data and pay no ransom. Yes, you heard that right! All you need to do is use secure cloud storage or external drives to back up your files and frequently check your recovery processes.
Use Firewalls and Antivirus Software
What would happen if you could permanently block unauthorized access and deal better with malicious software? Well, it is a human miracle that you have firewalls and antivirus software at your disposal. Jokes apart, they help you achieve the same, minus the hassles. You only need to ask your IT department to install top-notch antivirus software and reputable firewalls, and keep them up to date.
Regular Software Updates
If you think that functioning with outdated systems can save you money and the hassle of learning new tools, then it is time to remember the 2017 WannaCry ransomware attack. The only fault of businesses was that they didn’t update their Windows operating systems, which infected 200,000+ computers. Enable automatic updates for all operating systems, applications, and antivirus software to eliminate such hassles.
Encrypt Sensitive Data
What if hackers fail to use the data they hacked? Encryption can achieve this. Even if a system with customer data is stolen or hacked, hackers cannot understand it. Thus, make it a practice to encrypt files, emails, and devices containing sensitive data.
Invest in Cyber Liability Insurance
A safety net for your business is necessary in a world where hackers improve their tactics with each passing second. We understand that it is not possible to keep up with each attempt. So, what can be done? You can always rely on insurance to help recuperate lost revenue. All you need to do is work with a trusted insurance provider and choose a policy that best suits your business needs.
Test Your Security Regularly
It has been said repeatedly; we will repeat it: Ensure you conduct regular penetration tests to find weaknesses in your system. Stimulating complex attacks and finding weak spots in your system is a solid way to do this. Also, monitor your systems in real time with security information and event management (SIEM) tools. This will help you better detect threats and avoid damage from a breach. Therefore, it is crucial to schedule regular audits with professionals and address any concerns that arise promptly.
Limited Data Access
There is no point in giving confidential data access to all your employees. You should only provide employees with the data they need to perform their tasks. But how does this benefit you in the long run? Well, even if your account is hacked, you can minimize the damage to a great extent.
Create an Incident Response Plan
Even with all the security measures in place, a breach can happen. You need a well-defined plan to handle cyber attacks, cut the panic, and communicate effectively with your customers. So, how can you execute it seamlessly? You must isolate the infected systems, notify employees and key stakeholders, and restore backups for seamless functioning.
How BuzzClan Protects Your Organization Against Cybersecurity Threats?
Cybersecurity is much more than using the right tools and techniques. You need to be aware 24/7. And that’s not humanly possible. We understand that and thus provide you with the best audits and logging functionalities to protect your systems from all kinds of threats. We analyze your requirements and lay out a detailed roadmap following security best practices to ensure your systems are always protected. BuzzClan provides enterprise-grade security that helps you detect the most complex attacks and safeguard your systems. We specialize in:
- Multi-layered security architecture to protect your systems
- Automated compliance monitoring to ensure zero legal hassles
- 24/7 threat detection and response for proactive threat detection
- Incident response planning and comprehensive cybersecurity training
- 99.99% guaranteed uptime
The Final Thoughts
Technological advancements are directly proportional to the sophistication of hacking methods. Using security best practices and tools is just one aspect of protecting your systems and guarding confidential information. However, nothing stops vigilance and training. When employees across your organization are trained with the best tools and techniques, they can guide your customers better and massively reduce instances of cyberattacks and data breaches. Thus, make it a point to invest in training and workshops and conduct regular security audits for your system. While it may seem overwhelming initially, you will save yourself from many hassles in the long run.
FAQs

Get In Touch






