The Complete Guide to Enterprise Cloud Security: Strategy, Implementation, and Best Practices
Abhi Garg
Dec 17, 2024
The cloud has revolutionized enterprise operations, offering unparalleled scalability, flexibility, and cost-efficiency. However, this digital transformation brings new security challenges. In today’s interconnected world, cloud security is paramount, ensuring an organization’s data and applications remain safe and resilient in this dynamic environment.
This comprehensive guide delves deep into the intricacies of cloud security, exploring its core concepts, best practices, and emerging trends. Whether you’re a seasoned IT professional or an enterprise navigating the cloud landscape, this resource will equip you with the knowledge to fortify your cloud infrastructure and safeguard your valuable assets.
What is Cloud Security?
Cloud security, or cloud computing security, encompasses the technologies, policies, and best practices that protect cloud-based data, applications, and infrastructure from unauthorized access, threats, and vulnerabilities. It addresses the unique challenges of securing data stored outside traditional on-premises environments.
Security in cloud computing involves a shared responsibility model. The cloud provider secures the underlying infrastructure, while the customer is responsible for securing their data and applications residing within that environment. This shared responsibility necessitates a collaborative approach to ensure comprehensive protection.
Key Components of Cloud Security
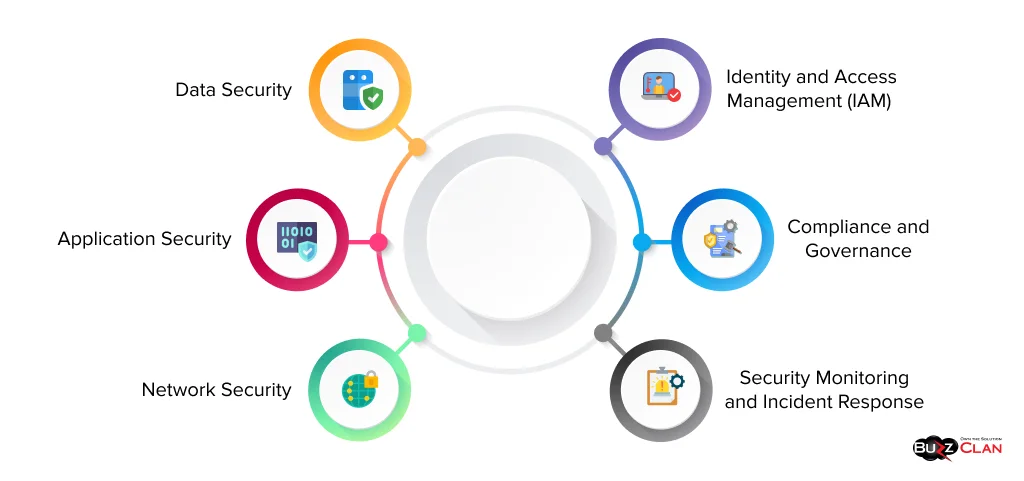
Effective cloud security requires a multi-layered approach that encompasses various essential components:
Data Security
- Encryption at rest and in transit: Encrypted data is unreadable without the appropriate decryption key, protecting it from unauthorized access.
- Access controls: Implementing access controls such as role-based access control (RBAC) and least privilege principles ensures that only authorized users can access specific data and resources.
- Data loss prevention (DLP) measures: DLP solutions identify, monitor, and protect sensitive data from unauthorized disclosure or exfiltration.
Application Security
- Secure coding practices: Developers should follow secure coding guidelines to prevent common vulnerabilities and coding errors that could lead to security breaches.
- Vulnerability scanning: Regularly scanning cloud applications for known vulnerabilities helps identify security weaknesses that attackers can exploit.
- Penetration testing: Conducting penetration tests simulates real-world attacks to uncover potential security vulnerabilities in cloud applications.
Network Security
- Firewalls: Firewalls act as a barrier between the cloud network and the internet, filtering and blocking unauthorized traffic.
- Intrusion detection systems (IDS): IDS monitor network traffic for suspicious activities and anomalies, alerting security teams to potential threats.
- Virtual private networks (VPNs): VPNs create secure tunnels for encrypted data transmission over public networks, preventing eavesdropping and unauthorized access.
Identity and Access Management (IAM)
- Authentication: Verifying user identities through multi-factor authentication (MFA) or other strong authentication methods ensures that only legitimate users can access cloud resources.
- Authorization: Authorization mechanisms control which users can access specific resources and what actions they can perform.
- Role-based access control (RBAC): RBAC assigns roles and permissions to users based on their job functions, ensuring they only have access to the resources they need to perform their duties.
Compliance and Governance
- Adherence to industry regulations: Compliance with GDPR, HIPAA, and PCI DSS ensures data privacy and security standards are met.
- Governance frameworks: Establishing governance frameworks provides a structured approach to cloud security, ensuring that security policies and procedures are aligned with enterprise objectives.
Security Monitoring and Incident Response
- Continuous monitoring: Monitoring cloud infrastructure, applications, and network traffic in real-time helps identify potential threats and security incidents.
- Log analysis: Analyzing security logs provides valuable insights into security events, helping security teams detect and investigate suspicious activities.
- Incident response planning: A well-defined incident response plan ensures that security teams can respond quickly and effectively to security incidents, minimizing their impact.
Types of Cloud Security Solutions
The market presents diverse cloud security solutions meticulously engineered to cater to specific security requirements within cloud environments. These solutions seamlessly integrate with existing cloud infrastructures, offering a comprehensive suite of functionalities to enhance security postures.
- Among the notable solutions are Cloud Access Security Brokers (CASB), which act as gatekeepers between users and cloud services. CASB solutions enforce robust security policies, ensuring compliance and providing granular visibility into cloud usage patterns.
- Security Information and Event Management (SIEM) tools play a vital role in collecting and analyzing security logs from various sources, enabling organizations to detect threats promptly and efficiently respond to security incidents.
- Intrusion Detection and Prevention Systems (IDPS) are vigilant guardians, monitoring network traffic for suspicious activities. IDPS solutions leverage advanced algorithms to identify potential attacks and take immediate action to prevent or mitigate their impact.
- Data Loss Prevention (DLP) tools are indispensable for safeguarding sensitive information by preventing unauthorized disclosure. DLP solutions implement stringent controls to ensure that confidential data remains within the organization’s purview, intentionally and unintentionally.
- Vulnerability Scanners are invaluable in identifying security weaknesses within cloud infrastructure and applications. These tools conduct comprehensive scans to detect potential vulnerabilities, allowing organizations to promptly prioritize and address security gaps.
- The aforementioned cloud security solutions provide a multi-layered defense against various threats and contribute to an enhanced security posture. By leveraging these solutions, organizations can confidently embrace cloud computing while maintaining the highest levels of security and compliance.
Cloud Security Automation
As cloud environments become increasingly intricate and interconnected, maintaining consistent security controls and responding swiftly to threats becomes paramount. Security automation is pivotal in navigating this complex landscape, enabling organizations to effectively manage and safeguard their cloud infrastructure.
One crucial aspect of cloud security is integrating security measures into Infrastructure as Code (IaC) practices from the outset. This involves:
- Automated Security Testing of IaC Templates: Implementing automated security testing tools to meticulously scan IaC templates for potential vulnerabilities and security misconfigurations even before deployment. This proactive approach helps identify and address security issues early, preventing them from propagating into production environments.
- Policy Enforcement during Infrastructure Deployment: Enforcing security policies ensures that all newly provisioned resources adhere to predefined security standards. This can be achieved through policy-as-code frameworks that automatically validate and enforce security policies during deployment, ensuring compliance with organizational security requirements.
- Continuous Compliance Validation: Establishing automated mechanisms for continuous compliance validation helps organizations comply with regulatory mandates and industry best practices. These mechanisms regularly assess cloud resources against compliance benchmarks, identifying deviations or potential risks and triggering remediation actions as necessary.
- Security Guardrails in CI/CD Pipelines: Incorporating security guardrails into CI/CD pipelines adds a layer of protection by enforcing security checks and gates throughout the development and deployment lifecycle. These guardrails help identify and block insecure code changes, preventing them from reaching production environments.
Adopting security as code principles ensures that security controls are consistently applied across all environments, fostering a standardized and auditable approach to cloud security. Additionally, version-controlling security controls alongside infrastructure code facilitate traceability, enabling teams to track changes and maintain a historical record of security configurations.
Furthermore, automating security testing is crucial for proactively identifying and mitigating potential risks in cloud environments. This involves implementing tools and processes for regular vulnerability scanning, configuration compliance checks, security benchmark testing, and penetration testing where applicable. Automating these tests helps or
Cloud Security Best Practices
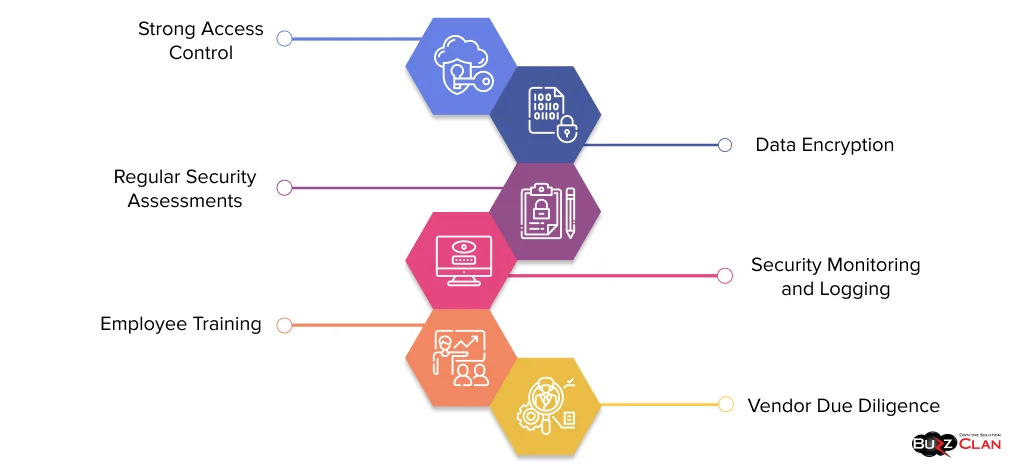
Implementing robust cloud security requires a comprehensive approach that encompasses various best practices and considerations:
Strong Access Control
- Enforce multi-factor authentication (MFA) for all users, including administrators, to prevent unauthorized access.
- Implement the principle of least privilege, granting users only the minimum level of access necessary to perform their job duties.
- Conduct regular user access reviews to identify and remove unnecessary privileges, reducing the risk of insider threats.
Data Encryption
- Encrypt data at rest using strong encryption algorithms such as AES-256.
- Encrypt data in transit using secure protocols like Transport Layer Security (TLS) or Virtual Private Networks (VPNs) to protect against eavesdropping and interception.
- Regularly rotate encryption keys to maintain data confidentiality.
Regular Security Assessments
- Conduct regular vulnerability scans and penetration testing to identify and exploit cloud infrastructure and application vulnerabilities.
- Schedule security audits to evaluate the cloud environment’s overall security posture and ensure compliance with industry standards and regulations.
- Address identified vulnerabilities promptly to minimize the risk of exploitation.
Security Monitoring and Logging
- Implement continuous security monitoring tools to detect suspicious activities and potential threats in real-time.
- Collect and analyze security logs to identify patterns, anomalies, and incidents.
- Security information and event management (SIEM) solutions centralize and correlate log data from various sources, enabling compr
Employee Training
- Educate employees about cloud security risks and best practices, including the importance of strong passwords, phishing awareness, and social engineering techniques.
- Provide training on incident reporting procedures, ensuring that employees know how to report any suspicious activities or security brea
Vendor Due Diligence
- Carefully evaluate cloud providers’ security posture before selecting a provider.
- Review the provider’s security certifications, compliance with industry standards, and track record of handling security incidents.
- Ensure that the provider offers transparent access to security documentation and allows for regular security audits.
By adhering to these best practices and considerations, organizations can significantly enhance their cloud security posture, protect sensitive data, and mitigate the risk of cyber threats.
Cloud Security for Remote Work
The shift to remote work has introduced new security challenges for cloud environments that organizations must address. With employees accessing corporate resources and sensitive data from remote locations, securing cloud environments becomes more critical than ever. Here are key considerations and best practices for cloud security in remote work settings:
Secure Access
- Zero Trust Network Access (ZTNA): Implement ZTNA to verify users and devices before granting access to cloud resources, regardless of location.
- Multi-factor Authentication (MFA): Enforce MFA for all remote users to add an extra layer of security beyond passwords.
- Device Health Checking: Continuously monitor remote devices for security vulnerabilities and compliance with organization policies.
- Conditional Access Policies: Configure access policies based on factors like device type, location, and user attributes to limit access to sensitive resources.
Endpoint Security
- Endpoint Detection and Response (EDR): Deploy EDR solutions to detect and respond to real-time threats on remote endpoints.
- Mobile Device Management (MDM): Implement MDM to manage and secure mobile devices used for remote work, ensuring compliance with security policies.
- Data Loss Prevention (DLP): Use DLP tools to detect and prevent unauthorized transfer or exfiltration of sensitive data from cloud environments.
- Regular Security Updates and Patches: Ensure that remote endpoints are regularly updated with the latest security patches and software updates to address vulnerabilities.
Additional Considerations
- Cloud Identity and Access Management (CIAM): Implement a robust CIAM solution to manage user identities, access privileges, and authentication mechanisms for cloud services.
- Encryption: Encrypt data at rest and in transit to protect sensitive information from unauthorized access.
- Cloud Security Posture Management (CSPM): Use CSPM tools to continuously monitor and assess the security posture of cloud environments, identifying potential risks and misconfigurations.
- Incident Response: Develop a comprehensive incident response plan that outlines procedures for responding to security incidents in a remote work environment.
- Employee Education: Regularly educate employees on cloud security best practices and potential risks associated with remote work to promote security-conscious behavior.
By implementing these measures, organizations can significantly enhance the security of their cloud environments and protect sensitive data in a remote work setting.
Cloud Security Threats and Vulnerabilities
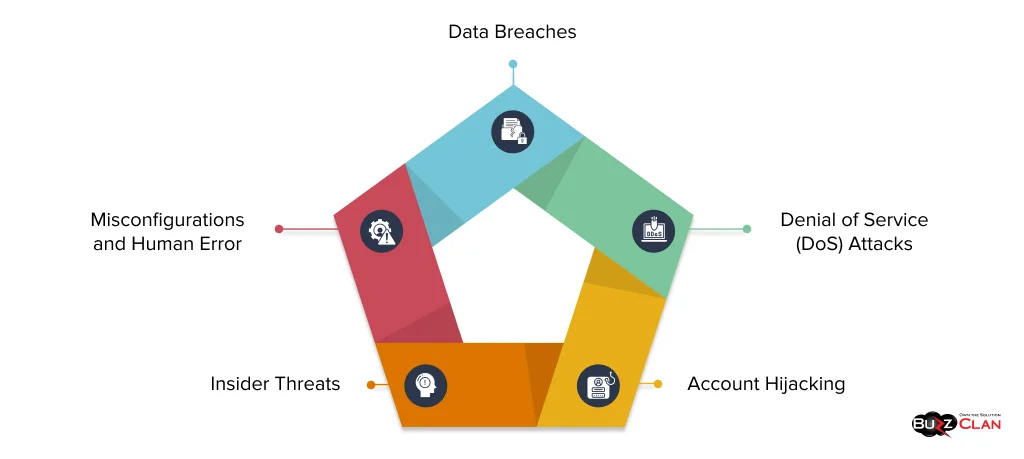
The cloud introduces a unique set of security challenges and vulnerabilities that organizations must address to protect their data and systems. Here are some of the most common cloud security threats:
- Data Breaches: Unauthorized access to sensitive data stored in the cloud can result in significant financial and reputational damage. This can occur due to various factors, including weak security configurations, vulnerabilities in cloud platforms, or malicious insiders.
- Misconfigurations and Human Error: Incorrectly configured cloud services, such as storage buckets or virtual machines, can expose data to unauthorized users. Human error, such as mistakenly sharing sensitive data or failing to apply security updates, can lead to misconfigurations and vulnerabilities.
- Insider Threats: Malicious or negligent insiders with authorized access to cloud resources can pose a significant risk to cloud security. They may intentionally steal or leak sensitive data, disrupt cloud services, or compromise user accounts.
- Denial of Service (DoS) Attacks: These attacks can target cloud services and disrupt their availability by flooding them with traffic or exploiting vulnerabilities. DoS attacks can prevent legitimate users from accessing cloud resources and cause significant business disruptions.
- Account Hijacking: Compromised user accounts can grant attackers access to sensitive data and resources stored in the cloud. This can occur through various methods, such as phishing attacks, password theft, or exploiting vulnerabilities in cloud platforms.
To mitigate these cloud security threats, organizations should implement comprehensive security measures, including:
- Strong Authentication: Use multi-factor authentication (MFA) to protect user accounts from unauthorized access.
- Encryption: Encrypt data at rest and in transit to protect it from unauthorized access, even if it is compromised.
- Access Control: Implement granular access controls to restrict access to cloud resources only to authorized users and services.
- Vulnerability Management: Regularly scan cloud systems for vulnerabilities and apply security updates promptly.
- Security Monitoring: Continuously monitor cloud activity for suspicious behavior and security threats.
- Incident Response: Develop and maintain an incident response plan to promptly address and mitigate security incidents.
By implementing these security measures and staying vigilant against emerging threats, organizations can significantly reduce their cloud security risks and protect their data and systems.
Supply Chain Security Risks in Modern Cloud Applications
Modern cloud applications heavily rely on a multitude of third-party components and services. This interconnectedness introduces significant supply chain security risks that organizations must proactively address. Ensuring the security of these applications requires a comprehensive approach encompassing vendor risk management and software composition analysis.
Vendor Risk Management
Organizations must establish and implement robust vendor risk management programs to mitigate the risks associated with third-party software and services. These programs should include:
- Security Assessment of Third-Party Providers: Before onboarding third-party providers, conduct thorough security assessments. Evaluate their security posture, compliance with industry standards, and track record in managing security incidents.
- Continuous Monitoring of Vendor Security Posture: Establish ongoing monitoring mechanisms to track and assess the security posture of third-party providers. This includes monitoring for vulnerabilities, misconfigurations, and any changes in their security practices.
- Clear Security Requirements in Vendor Contracts: Incorporate clear and specific security requirements into vendor contracts. These requirements should outline expectations for data protection, incident response, and compliance with relevant regulations.
- Regular Review of Vendor Access and Privileges: Review and manage vendor access and privileges regularly. Ensure that vendors have only the minimum access required to perform their services and promptly revoke access when no longer needed.
Software Composition Analysis
Understanding and securing the software supply chain requires organizations to adopt software composition analysis practices. These practices include:
- Automated Scanning of Third-Party Dependencies: Implement automated scanning tools to identify and track third-party dependencies in cloud applications. This helps organizations gain visibility into the software components they rely on.
- Vulnerability Management for Open-Source Components: Given the prevalence of open-source components in modern applications, organizations must prioritize vulnerability management. This includes staying updated on security advisories, patching vulnerabilities promptly, and implementing secure coding practices.
- Software Bill of Materials (SBOM) Maintenance: Maintain a comprehensive software bill of materials (SBOM) that lists all the components, libraries, and dependencies used in cloud applications. The SBOM should be regularly updated to reflect the changes in the application’s software composition.
- Regular Updates and Patch Management: Establish a robust patch management process to apply security updates and patches to third-party components promptly. This helps mitigate vulnerabilities and reduce the risk of exploitation.
By implementing these vendor risk management and software composition analysis practices, organizations can significantly enhance the security of their modern cloud applications and protect against potential supply chain threats.
Cloud Security Trends
The cloud security landscape is constantly changing, with new threats and technologies emerging at an unprecedented rate. Organizations must be aware of the latest trends and developments in cloud security to stay ahead of the curve.
Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML are increasingly used to automate threat detection, analyze security data, and improve incident response. These technologies can help organizations identify and respond to threats more quickly and effectively. For example, AI-powered security solutions can detect suspicious activity patterns, identify malicious software, and investigate security incidents.
Serverless Computing Security
Serverless computing is a cloud computing model that allows organizations to run code without managing servers. This can be a more cost-effective and scalable way to develop and deploy applications. However, it also introduces new security challenges. For example, serverless functions and APIs can be more vulnerable to attack than traditional applications. Organizations need to implement specialized security measures to protect their serverless applications.
DevSecOps
DevSecOps is a practice that integrates security into the software development lifecycle (SDLC). This approach helps ensure that security is considered from the beginning of the development process rather than being an afterthought. DevSecOps can help organizations develop more secure applications and reduce the risk of security breaches.
Zero Trust Security
Zero-trust security is a security model that assumes no user or device is inherently trustworthy. This approach enforces strict access controls and verification for all users and devices, regardless of location or identity. Zero-trust security can help organizations protect their data and applications from unauthorized access.
Edge Computing Security
Edge computing is a distributed computing model that brings computation and data storage closer to the devices and users that need it. This can improve performance and reduce latency. However, it also introduces new security challenges. For example, edge devices can be more vulnerable to attack than traditional centralized servers. Organizations need to implement specialized security measures to protect their edge computing environments.
These are just a few of the latest trends in cloud security. Organizations must be aware of these trends and implement the appropriate security measures to protect their data and applications.
Cloud Security for Different Deployment Models
Cloud security considerations vary depending on the chosen deployment model:
Infrastructure as a Service (IaaS)
In the IaaS deployment model, the customer is responsible for securing their operating systems, applications, and data. This includes tasks such as:
- Patching and updating operating systems and applications
- Configuring security settings on operating systems and applications
- Implementing access controls to restrict who can access resources
- Encrypting data at rest and in transit
- Implementing disaster recovery and backup plans
Customers using IaaS should also be aware of the shared responsibility model, which states that the cloud provider is responsible for securing the infrastructure. In contrast, the customer is responsible for securing their data and applications.
Platform as a Service (PaaS)
In the PaaS deployment model, the cloud provider manages the underlying infrastructure while customers secure their applications and data. This means that customers are responsible for tasks such as:
- Configuring security settings on their applications
- Implementing access controls to restrict who can access their applications
- Encrypting data at rest and in transit
- Implementing disaster recovery and backup plans
Customers using PaaS should also be aware of the shared responsibility model, which states that the cloud provider is responsible for securing the platform. In contrast, the customer is responsible for securing their applications and data.
Software as a Service (SaaS)
In the SaaS deployment model, the cloud provider is responsible for securing the entire stack, including the application, infrastructure, and data. Customers do not need to worry about securing their infrastructure or applications. However, customers are still responsible for tasks such as:
- Configuring security settings on their SaaS accounts
- Implementing access controls to restrict who can access their SaaS accounts
- Encrypting data at rest and in transit
- Implementing disaster recovery and backup plans
SaaS customers should also be aware of the shared responsibility model, which states that the cloud provider is responsible for securing the service. In contrast, the customer is responsible for securing their data and access to the service.
Container Security in Cloud Environments
Given organizations’ growing adoption of containerized applications, container security constitutes a vital cloud security component. This modern approach to application deployment presents distinctive security challenges that demand attention throughout the container lifecycle.
Container Image Security
Container images are the foundation of containerized applications, rendering their security paramount. Organizations must prioritize robust processes for creating, storing, and managing secure container images. This entails:
- Scanning images for vulnerabilities: It is crucial to scan base images and application dependencies for vulnerabilities regularly. Organizations should establish policies for using only approved base images and maintain an up-to-date inventory of all container images.
- Maintaining a secure container registry: Organizations should implement a secure registry to store and manage container images centrally. This registry should be protected from unauthorized access and regularly scanned for vulnerabilities.
- Implementing proper access controls: Establishing granular access controls for image management is essential. This includes restricting who can create, modify, and delete images and implementing role-based access control (RBAC) to limit privileges.
Runtime Security
Securing containers during runtime necessitates multiple layers of protection, including:
- Network segmentation between containers: Isolating containers on separate networks helps prevent lateral movement of threats and limits the impact of security breaches.
- Resource usage monitoring and limitations: Monitoring and enforcing resource limits for containers helps prevent resource starvation and denial-of-service attacks.
- Runtime vulnerability scanning: Regularly scanning running containers for vulnerabilities is crucial for promptly detecting and patching potential security issues.
- Behavioral monitoring for anomaly detection: Implementing behavioral monitoring tools can detect anomalous activities within containers, indicating potential attacks or misconfigurations.
Kubernetes Security
Kubernetes, a widely adopted container orchestration platform, offers additional security features that organizations should leverage. These include:
- Pod security policies (PSPs): PSPs allow organizations to enforce security best practices and prevent privileged container execution unless specifically required. PSPs can define restrictions on resource usage, network access, and file system access.
- Role-based access control (RBAC): RBAC in Kubernetes enables organizations to define fine-grained access controls for different users and service accounts. This helps prevent unauthorized access to sensitive resources and actions within the cluster.
- Network policies: Network policies in Kubernetes allow organizations to define how pods and external resources can communicate with each other. This helps prevent unauthorized network traffic and enforce network segmentation.
By implementing these security measures throughout the container lifecycle, organizations can significantly reduce the risk of attacks and ensure the integrity and confidentiality of their containerized applications.
The Importance of a Cloud Security Strategy
A well-defined cloud security strategy is vital for organizations embracing the cloud. It aligns with enterprise objectives and encompasses several key elements:
Risk Assessment
- Identifying potential security risks associated with cloud environments, including data breaches, unauthorized access, and compliance issues.
- Evaluating the sensitivity and criticality of data stored in the cloud to prioritize risk mitigation efforts.
- Conducting regular vulnerability assessments to uncover weaknesses in cloud infrastructure and applications.
Security Policies and Procedures
- Establishing clear and comprehensive security policies that outline the organization’s approach to cloud security.
- Defining roles and responsibilities for cloud security management and incident response.
- Developing detailed procedures for data encryption, access control, and secure configuration of cloud services.
Technology Selection
- Evaluating and selecting appropriate cloud security solutions, such as firewalls, intrusion detection systems, and data loss prevention tools.
- Ensuring that chosen solutions are compatible with the organization’s security infrastructure and policies.
- Considering cloud-native security features and services offered by cloud providers to enhance protection.
Employee Training and Awareness
- Conducting training programs to educate employees about cloud security best practices, potential threats, and their role in maintaining a secure cloud environment.
- Emphasizing the importance of adhering to security policies and procedures, including proper password management and reporting suspicious activities.
Continuous Monitoring and Improvement
- Implementing continuous monitoring tools and processes to detect and respond to security incidents in real time.
- Review security logs and reports regularly to identify trends and patterns indicating potential threats.
- Updating the cloud security strategy based on lessons learned from security incidents, industry best practices, and changes in business requirements.
A robust cloud security strategy ensures that organizations leverage the benefits of cloud computing while mitigating risks and maintaining compliance with regulatory standards. By proactively addressing cloud security concerns, organizations can foster trust among stakeholders and drive enterprise innovation securely and competently.
Cost Management for Security
Effective cloud security requires a delicate balance between protection and cost efficiency. Organizations must develop strategies to optimize security spending while maintaining robust protection.
Security Investment Planning
- Risk-based prioritization of security controls: Identify critical assets and prioritize security controls based on the likelihood and impact of potential threats. Focus investments on controls that address the most significant risks.
- Total cost of ownership (TCO) for security solutions: Consider upfront costs, including hardware, software, and implementation services, and factor in ongoing costs such as maintenance, support, and updates. Choose solutions with a reasonable TCO over their lifetime.
- Integration costs and operational overhead: Evaluate the costs of integrating new security solutions into existing infrastructure. Consider factors such as training and onboarding personnel, managing additional consoles, and potential disruptions to operations.
- Return on security investment (ROSI) calculations: Quantify the benefits of security investments, such as reduced risk of data breaches, compliance with regulations, and improved brand reputation. Compare these benefits to the costs to determine the potential ROSI.
Cost Optimization Strategies
- Consolidating security tools to reduce overlap: Assess existing security tools and identify opportunities for consolidation. Eliminate redundant tools and choose integrated solutions that offer multiple functionalities to reduce costs and simplify management.
- Leveraging native cloud security features: Utilize built-in features offered by cloud providers, such as access control, encryption, and threat detection. These features are often included in cloud subscription fees, eliminating the need for additional tools and reducing costs.
- Automating routine security tasks: Implement automated solutions for repetitive security tasks such as patch management, vulnerability scanning, and log analysis. Automation reduces manual labor, improves efficiency, and frees security personnel to focus on strategic initiatives.
- Implementing proper resource scaling: Monitor cloud resource usage and adjust security controls dynamically to match the current level of risk. Scale up security measures during peak periods or when sensitive data is being processed and scale down during low-risk periods to optimize resource allocation and save costs.
Cloud Migration Strategy and Security
A comprehensive Cloud Migration Strategy should prioritize security considerations throughout the migration process. This includes:
Security Assessment
- Evaluating the security posture of existing applications and infrastructure before migration.
- Identifying potential vulnerabilities and risks associated with the migration process.
- Conducting a thorough risk assessment to determine the potential impact of security breaches or data loss.
Data Security
- Implementing data encryption in transit and at rest to protect sensitive data during migration and storage in the cloud.
- Establishing robust access controls to restrict access to data only to authorized users.
- Implementing data loss prevention measures to prevent unauthorized access, use, or disclosure of sensitive data.
Application Security
- Ensuring applications are secure in the new cloud environment through secure coding practices, such as input validation, escaping, and vulnerability scanning.
- Implementing runtime protection mechanisms, such as intrusion detection and prevention systems (IDPS) and web application firewalls (WAFs), to detect and block attacks.
- Regularly patching and updating applications to address newly discovered vulnerabilities.
Network Security
- Configuring network security measures, such as firewalls, VPNs, and access control lists (ACLs), to protect cloud resources from unauthorized access.
- Implementing network segmentation to isolate different parts of the network and prevent the spread of infections or attacks.
- Monitoring network traffic for suspicious activity and implementing intrusion detection and prevention systems (IDPS) to detect and block malicious traffic.
Compliance
Maintaining compliance with relevant industry regulations and standards throughout the migration process, such as
- GDPR (General Data Protection Regulation): The GDPR is a comprehensive data protection law enacted by the European Union in 2018. It applies to any organization that processes the personal data of EU residents, regardless of where the organization is located. The GDPR imposes strict requirements on organizations regarding collecting, using, and storing personal data. It also gives individuals several rights concerning personal data, such as access, rectification, and erasure.
- HIPAA (Health Insurance Portability and Accountability Act): HIPAA is a US law that protects the privacy of health information. It applies to healthcare providers, insurers, and other entities that handle health information. HIPAA requires these entities to implement security measures to protect health information from unauthorized access, use, or disclosure. It also gives individuals several rights concerning their health information, such as the right to access, amend, and receive an accounting of disclosures of their health information.
- PCI DSS (Payment Card Industry Data Security Standard): PCI DSS is a set of security standards to protect credit and debit card data. It is a self-regulatory standard managed by the Payment Card Industry Security Standards Council (PCI SSC). PCI DSS applies to any organization that processes, stores or transmits credit or debit card data. These organizations must implement security measures to protect card data from unauthorized access, use, or disclosure.
- SOX (Sarbanes-Oxley Act): SOX is a US law enacted in 2002 after several corporate scandals. It is designed to improve corporate governance and financial reporting and imposes requirements on publicly traded companies, including internal controls, financial reporting, and auditor independence.
- CCPA (California Consumer Privacy Act): The CCPA is a California law that protects consumers’ personal information privacy. It applies to any business that collects or processes the personal information of California residents. The CCPA gives consumers several rights concerning their personal information, such as the right to know what information is collected, to opt out of the sale of their information, and to request the deletion of their information.
Cloud Security Architecture Patterns
Modern cloud security demands well-conceived architectural patterns that can be uniformly applied across diverse workloads and environments. These patterns serve as blueprints for effectively and consistently securing cloud deployments.
Reference Architectures
Organizations should establish and maintain reference architectures tailored to the specific security requirements of different workload types. These architectures should encompass the following key security considerations:
- Network Segmentation: Implementing network segmentation strategies to isolate various components and workloads within the cloud environment. This helps contain potential security breaches and limits the impact of compromised systems.
- Identity and Access Management (IAM): Enforcing robust IAM policies to control access to cloud resources. This includes implementing role-based access control (RBAC) and multi-factor authentication (MFA) to ensure that only authorized users can access sensitive data and systems.
- Data Protection: Employing encryption at rest and in transit protects data stored in the cloud. Additionally, implementing data masking and tokenization techniques can further enhance data privacy.
- Monitoring and Logging: Establishing comprehensive monitoring and logging mechanisms to promptly detect and respond to security threats. These systems should be configured to collect and analyze security-related events, providing valuable insights for threat detection and incident response.
- Disaster Recovery: Developing and maintaining a disaster recovery plan to ensure business continuity during a major disruption or outage. This plan should outline procedures for data backup, system recovery, and failover to ensure minimal downtime and data loss.
Microservices Security Considerations
Microservices architectures introduce unique security challenges due to their distributed nature. The following considerations are essential for securing microservices environments:
- Service-to-Service Authentication: Establish secure authentication mechanisms between microservices to prevent unauthorized access and ensure that only authorized services can communicate.
- API Security: Implementing API security measures, such as rate limiting, input validation, and access control, protects APIs from malicious attacks and data breaches.
- Secret Management: Employing robust secret management practices to securely store and manage sensitive information, such as API keys, database credentials, and encryption keys.
- Network Policies: Enforcing network policies to control traffic flow between microservices and external networks helps prevent unauthorized access and the lateral movement of threats within the environment.
- Container Orchestration Security: Securing container orchestration platforms, such as Kubernetes, is crucial. This includes implementing security features like pod security policies, network policies, and admission control mechanisms to enhance the overall security posture of the microservices environment.
Database as a Service (DBaaS) Security
Database as a Service (DBaaS) provides a managed database environment in the cloud, offering scalability, reliability, and ease of management. However, securing DBaaS environments is crucial to protect sensitive data and maintain compliance. DBaaS security involves several key aspects:
Access Control
- Implement robust authentication mechanisms such as multi-factor authentication (MFA) to verify the identity of users accessing the database.
- Define granular authorization policies to control who can access specific data and what actions they can perform.
- Regularly review and update user permissions to align with current business needs.
Data Encryption
- Encrypt sensitive data at rest using encryption algorithms such as AES-256.
- Implement encryption in transit using secure protocols like SSL/TLS to protect data during transmission.
- Manage encryption keys securely and rotate them regularly to prevent unauthorized access.
Regular Backups
- Establish a comprehensive backup strategy that includes regular, automated database backups.
- Store backups in a secure, off-site location to protect them from accidental deletion or hardware failures.
- Test the backup and recovery process periodically to ensure data can be restored quickly and efficiently.
Vulnerability Management
- Regularly update database software with the latest security patches to address known vulnerabilities.
- Conduct vulnerability assessments to identify potential weaknesses in the database configuration and infrastructure.
- Implement security best practices such as firewall configuration and intrusion detection systems to protect against external threats.
Monitoring and Auditing
- Implement database activity monitoring tools to detect suspicious activities such as unauthorized access, data tampering, and SQL injection attempts.
- Establish audit trails to record database events and user actions for compliance and forensics.
- Review monitoring data and audit logs regularly to identify anomalies and potential security incidents.
Compliance
- Ensure that DBaaS security measures align with industry regulations and standards such as PCI DSS, HIPAA, and GDPR.
- Implement data retention policies to manage and dispose of sensitive data per regulatory requirements.
- Conduct regular compliance audits to assess the effectiveness of DBaaS security controls and address any gaps.
By implementing these DBaaS security best practices, organizations can enhance the protection of their sensitive data, mitigate security risks, and ensure compliance with regulatory requirements.
Risks of Cloud Computing
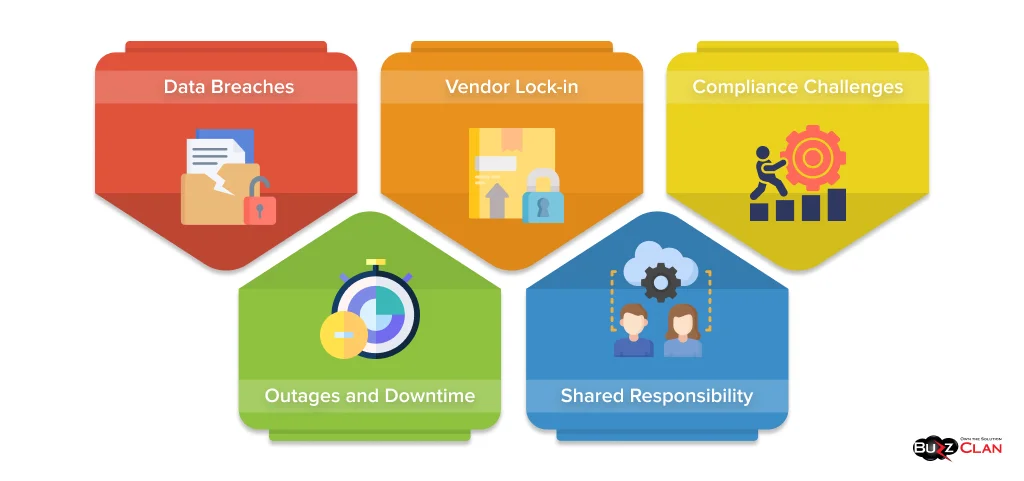
While the cloud offers numerous advantages for businesses, such as cost savings, scalability, and agility, it also introduces inherent risks that must be carefully managed. These risks include:
- Data Breaches: Cloud environments can be vulnerable to data breaches if not adequately secured. This is because cloud providers often have access to customer data, and if their security measures are not robust enough, data can be compromised. To mitigate this risk, businesses should choose a cloud provider with a strong security track record and implement additional security measures such as encryption and access controls.
- Vendor Lock-in: Dependence on a specific cloud provider can limit flexibility and increase switching costs. This is because cloud providers often offer proprietary services and APIs, making it difficult to migrate to another provider. To avoid vendor lock-in, businesses should carefully evaluate their cloud needs and choose a provider with open standards and interoperability.
- Compliance Challenges: The cloud can make meeting regulatory requirements and compliance standards complex. This is because cloud providers are often located in different jurisdictions, and businesses must ensure they comply with the laws and regulations of all the countries where their data is stored and processed. To address this challenge, businesses should work with cloud providers that offer compliance tools and services and clearly understand their shared responsibility model.
- Outages and Downtime: Cloud services can experience outages and downtime, impacting enterprise operations. Cloud providers depend on complex infrastructure and software; even minor technical issues can disrupt service. To mitigate this risk, businesses should choose a cloud provider with a high uptime guarantee and implement disaster recovery and business continuity plans.
- Shared Responsibility: Understanding the shared responsibility model is crucial for ensuring comprehensive cloud security. In this model, cloud providers are responsible for securing the cloud infrastructure, while businesses are responsible for securing their data and applications. To effectively manage this shared responsibility, businesses should work closely with their cloud providers to define clear roles and responsibilities and implement appropriate security measures.
Cloud Security Metrics and KPIs
Measuring an organization’s security posture effectiveness requires the establishment of clear metrics and key performance indicators (KPIs). These metrics serve as quantifiable benchmarks that enable organizations to assess their security posture, track progress over time, and identify areas for improvement.
Key Metrics for Security Effectiveness
- Mean Time to Detect (MTTD) Security Incidents: This metric measures an organization’s average time to identify and detect a security incident. A shorter MTTD indicates a more efficient and responsive security posture.
- Mean Time to Respond (MTTR) to Incidents: This metric measures an organization’s average time to investigate, contain, and remediate a security incident. A shorter MTTR indicates a more effective incident response process.
- Number of Security Incidents: This metric tracks the total number of security incidents experienced by an organization over a certain period. A few incidents indicate a strong security posture and effective prevention measures.
- Compliance Score: This metric assesses an organization’s adherence to industry regulations, standards, and best practices. A high compliance score indicates that the organization is taking proactive steps to mitigate risks and protect sensitive information.
- Security Posture Score: This metric evaluates an organization’s overall security posture based on various factors, such as security controls, vulnerabilities, and risk exposure. A high-security posture score indicates a mature and robust security program.
Security Dashboards
Effective security dashboards are essential tools for visualizing and analyzing security metrics. These dashboards provide real-time insights into the organization’s security status, enabling stakeholders to make informed decisions and respond swiftly to potential threats. Key features of effective security dashboards include:
- Real-Time Visibility into Security Status: Security dashboards should provide real-time visibility into the organization’s security status, including metrics such as active alerts, blocked attacks, and compromised systems.
- Trend Analysis: Dashboards should enable users to analyze trends over time, identifying patterns and anomalies. This helps organizations understand the evolution of their security posture and identify potential areas of concern.
- Risk Indicators: Dashboards should incorporate risk indicators highlighting potential vulnerabilities and threats to the organization. These indicators help prioritize security efforts and focus resources on the most critical risks.
- Compliance Status: Dashboards should display an organization’s compliance status with industry regulations and standards. This enables organizations to monitor compliance requirements and ensure they take necessary steps to protect sensitive information.
By leveraging clear metrics, KPIs, and effective security dashboards, organizations can comprehensively understand their security posture, track progress, and make data-driven decisions to enhance security effectiveness.
Future of Cloud Security
The cloud security landscape constantly evolves, with new technologies and threats emerging regularly. Organizations must be aware of these changes and adapt their security strategies accordingly.
Emerging Technologies
- Quantum-safe cryptography: Quantum computers have the potential to break current encryption standards. Quantum-safe cryptography is a new type of cryptography that is resistant to attack by quantum computers.
- AI-driven security analytics: AI can analyze large amounts of security data to identify potential threats, helping organizations detect and respond more quickly.
- Automated threat hunting: Threat hunting proactively searches for threats within an organization’s network. Automated threat-hunting tools can help organizations quickly identify and respond to threats.
- Zero-trust micro-segmentation: Zero-trust micro-segmentation is a security architecture that assumes all network traffic is untrusted. It involves dividing the network into small segments and restricting traffic between segments.
Evolution of Threats
- Advanced persistent threats: APT are sophisticated attacks designed to remain undetected for long periods. They can cause significant damage to organizations, including data theft, financial loss, and reputational damage.
- AI-powered attacks: AI can create more sophisticated and targeted attacks. AI-powered attacks can exploit vulnerabilities in AI systems or use AI to generate realistic-looking phishing emails.
- Supply chain attacks: It target organizations through their suppliers. Attackers can compromise a supplier’s systems and use them to attack the organization’s customers.
- Zero-day exploits: Zero-day exploits are vulnerabilities that have not yet been patched. Zero-day exploits can be used to attack organizations before they can apply a patch.
Conclusion: Cloud Security as an Evolving Journey
Cloud security is a dynamic and continuous process that requires ongoing attention and commitment. As the cloud landscape evolves rapidly, organizations must adopt a proactive and vigilant approach to safeguard their assets and data. Here are key points to emphasize in the conclusion:
- Dynamic Cloud Landscape
The cloud landscape constantly evolves with new technologies, services, and threats emerging regularly. Organizations must stay informed about these changes and adapt their security strategies accordingly.
- Proactive and Vigilant Approach
Cloud security cannot be achieved through a one-time effort. Organizations must maintain a proactive mindset, continuously monitoring their cloud infrastructure for vulnerabilities and threats. Regular security assessments and penetration testing can help identify and address potential weaknesses.
- Robust Security Measures
Implementing robust security measures is crucial for cloud security. This includes adopting best identity and access management practices, data encryption, network security, and incident response. Organizations should leverage cloud-native security tools and services to enhance their defenses.
- Adherence to Best Practices
Adequate cloud security requires following industry-recognized best practices and security standards, such as:
NIST Cybersecurity Framework: The NIST Cybersecurity Framework (NIST CSF) is a voluntary framework that provides a high-level view of cybersecurity risk management. It is based on existing standards, guidelines, and best practices. The NIST CSF helps organizations identify, prioritize, and mitigate cybersecurity risks. It also helps enterprises improve their cybersecurity posture and align their cybersecurity efforts with business goals.
ISO 27001/27017/27018: ISO 27001 is an international standard that provides requirements for an information security management system (ISMS), a framework for managing cybersecurity risks. ISO 27001 helps organizations protect their information assets from unauthorized access, use, disclosure, disruption, modification, or destruction. ISO 27017 is a related standard that provides specific guidance for implementing ISO 27001 in cloud computing environments. ISO 27018 is another related standard that provides specific guidance for implementing ISO 27001 in connected and automated vehicles.
CIS Controls: The CIS Controls are a set of cybersecurity best practices developed by the Center for Internet Security (CIS). They are based on the NIST CSF and other cybersecurity standards and help organizations identify and mitigate the most common cybersecurity risks.
CSA STAR: CSA STAR is a cloud security certification program developed by the Cloud Security Alliance (CSA). It helps organizations assess and improve their cloud security posture and is based on the NIST CSF and other cybersecurity standards.
- Informed Decision-Making
Staying informed about emerging threats and vulnerabilities is critical for proactive cloud security. Organizations should regularly monitor security advisories, bulletins, and threat intelligence feeds to stay ahead of potential attacks.
- Continuous Monitoring and Incident Response
Continuous monitoring of cloud infrastructure is crucial for promptly detecting and responding to security incidents. Organizations should implement real-time monitoring solutions with automated alerting mechanisms to ensure a rapid response to potential breaches or suspicious activities.
- Skilled Workforce
Building a skilled workforce with expertise in cloud security is essential. Organizations should invest in training and development programs to ensure their security professionals have the knowledge and skills to manage cloud security challenges effectively.
- Regulatory Compliance
Organizations operating in regulated industries must ensure compliance with specific data protection and privacy regulations. Cloud security measures should align with these regulations to avoid legal and reputational risks.
- Continuous Improvement
Cloud security is an iterative process that requires continuous improvement. Organizations should regularly review their security posture, identify areas for improvement, and implement necessary enhancements to stay ahead of evolving threats.
FAQs

Get In Touch
Follow Us
Table of Contents
- What is Cloud Security?
- Key Components of Cloud Security
- Types of Cloud Security Solutions
- Cloud Security Automation
- Cloud Security Best Practices
- Cloud Security for Remote Work
- Cloud Security Threats and Vulnerabilities
- Supply Chain Security Risks in Modern Cloud Applications
- Cloud Security Trends
- Cloud Security for Different Deployment Models
- Container Security in Cloud Environments
- The Importance of a Cloud Security Strategy
- Cost Management for Security
- Cloud Migration Strategy and Security
- Cloud Security Architecture Patterns
- Database as a Service (DBaaS) Security
- Risks of Cloud Computing
- Cloud Security Metrics and KPIs
- Future of Cloud Security
- Conclusion: Cloud Security as an Evolving Journey
- FAQs