What is Malicious Code? The Complete Enterprise Defense Guide for 2025
Ramesh Rastogi
Jun 17, 2025
What is Malicious Code?
Digital villains are not limited to high-profile cyber threats. They can also sneak into your code to steal your data and even hijack your system. Yes, we are talking about malicious code. They come in various shapes, sizes, and threat intensities, including spyware, ransomware, worms, and more.
Just like viruses make people sick, malicious code replicates the same way with computers and networks. Pause for a bit and go down memory lane. Think of the time you downloaded a free music app and it installed spyware on your phone.
All your messages can be monitored, and you surely don’t want that. Remember the Pegasus spyware in 2021, which infected thousands of smartphones? Once it found its place in phones, it could access everything.
Luckily, we won’t let that happen to your business. Thus, we wrote this blog to help you steer clear and stay ahead of all cyber threats.
Types of Malicious Code
The varieties and impact are sure to blow your mind away. However, knowing them will help you be prepared for lurking threats.
| Malicious Code Examples | Impact |
|---|---|
| Virus | Viruses are often attached to files and spread like wildfire! |
| Worm | Worms are hyper-independent, replicate with zero intervention, and can slow down your networks. |
| Trojan Horse | There is no better conman than the Trojan Horse. The widespread “ILOVEYOU” virus caused losses worth $8.7 billion. |
| Spyware | They secretly record user activity and steal passwords. |
| Adware | Distracting you is the favorite pastime of adware. It bombards you with ads to redirect your browser. |
| Ransomware | With 150+ countries impacted during the WannaCry attack, you need to be extra cautious of this cyber threat as it locks files and demands vast sums of money to unlock them. |
| Rootkits | Fooling security tools helps unauthorized users gain access to systems. |
| Cross-site scripting (XSS) | Malicious commands are injected into web applications, causing changes in web content and gaining access to confidential information. |
Detection Methods of Malicious Code
But how do you know if you have been affected by malicious code? Here is how to do it easily. However, before that, heave a sigh of relief that you have detected the issue before it becomes a menace.
- Signature-based detection will help you compare files against known malware libraries. Once you identify issues, you can take action to prevent their spread.
- On the other hand, a heuristic analysis will help you spot unusual activities even without known signatures.
- Sandboxing, at the same time, runs apps in isolated environments to analyze their behavior.
- Similarly, intrusion detection systems help you monitor networks for abnormal traffic patterns.
- User Behavior Analytics (UBA) is another essential tool that will help you detect odd behavior.

How Can You Prevent Viruses and Malicious Code?
You must follow the proper practices and have the best tools to fight malicious code and prevent viruses. Let’s examine how you can achieve both and safeguard your systems.
- Install AntiVirus Software: If your first line of defense is not strong, threats can permeate your system in no time—many small businesses close in less than a year due to cyber attacks. The reason is that they didn’t bother to invest in good antivirus software!
- Avoid Downloading Malicious Code: Use trusted repositories and scan files with antivirus tools to shield your device from hidden threats. Verifying the source is a must to secure your system.
- Make Use of Firewalls: Playing with fire here will help you reap rich dividends! All the bad jokes are on us! Well, firewalls will help you filter traffic and block threats before they harm your system. This way, you keep viruses and malicious code miles away from your system.
- Update Your Software: Outdated software has never brought anyone anything good- only viruses! No one knows this better than the 147 million people whose data were exposed in the Equifax breach due to a missed patch in the software.
- Multi-Factor Authentication To Rescue: Even if your passwords are stolen, MFA ensures that hackers don’t know what’s happening inside your system!
- Be Email-Smart: It is always better to avoid unnecessary “Attachments and Links”. Nothing could be truer in this context. Extra skepticism is welcome, as employees often install viruses through fake emails.
- Backup Regularly: Don’t let ransomware strip the millions you’ve built over the years! Backing up your data regularly will help you bounce back faster after an attack.
- Implement Zero-Trust Architecture: Each access attempt in ZTA is verified as a hacking attempt till identity verification is done. Make it a part of your organizational cybersecurity framework to add that extra layer of security.
- Blend White and Black Box Testing: Both white and black box testing will help you develop a thorough understanding of how your system responds to threats.
- Train Employees: Your employees are the weakest link in the system. Ensure they are trained well to prevent accidental viruses and malicious code installation.
- Avoid Working on Public Wi-Fis: Public Wi-Fis is also used by attackers to deliver malicious code and viruses. Make sure you only use a secure connection.
- Use Pop-Up Blockers: This prevents scripts from serving malicious content in unwanted browser windows.
How Malicious Code Works?
Unfortunately, these codes are organized and work systematically. However, you can follow the same procedure to safeguard your systems.
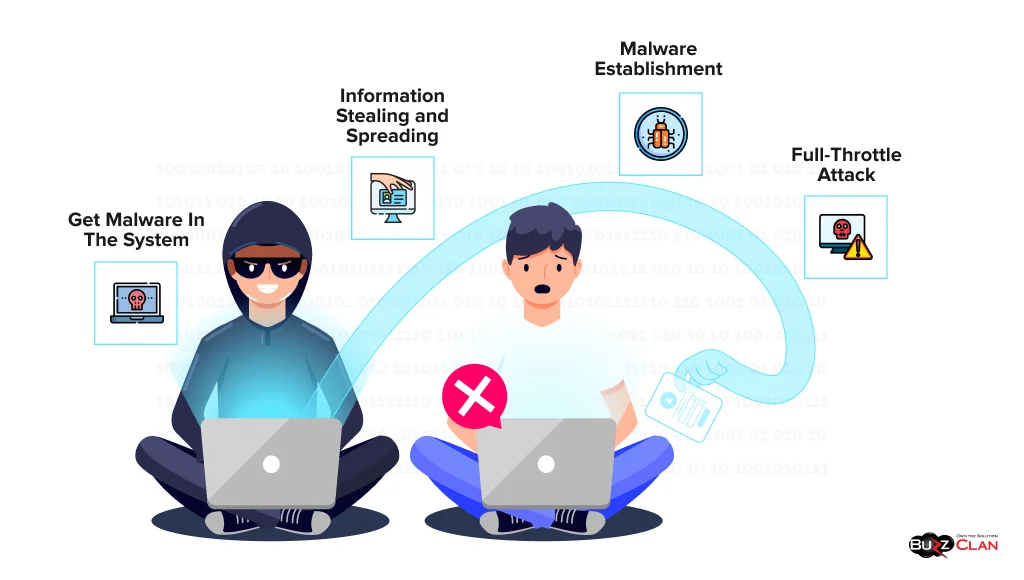
- The first step is to get the malware into the system, usually through harmful attachments or bad links. Hackers then trick your employees into clicking on the links using innovative tactics.
- Secondly, once the malware is on the system, it can steal information and spread to other connected systems. This happens quietly, and you don’t even realize something is wrong.
- The third step is to try to remove the malware. However, some malware is designed to stay in the system for long, emphasizing the importance of robust security systems.
- Finally, the malware launches a full-throttle attack and, in the worst case, takes control of the system. This often leads to delays, damage to your company’s reputation, and monetary losses.
Imagine clicking on a harmless “Netflix Support” link asking you to change your password. Lo and Behold! In a split second, malware has found comfort in your system.
Further Reading
The Role of BuzzClan in Preventing Malicious Code
BuzzClan is your ultimate defense against cyber threats. Our team of experts first understands your organizational landscape, collects detailed requirements, and then suggests the best possible solutions. Moreover, the right blend of tools and in-depth experience has helped us ensure 99.99% downtime, automated monitoring, and fortify your business against attacks. Here is why you should partner with us.
- Thorough risk assessments to eliminate attacking attempts.
- Advanced threat protection for cloud data
- Multi-layered security architecture to protect your systems
- 24/7 threat detection and response for proactive threat detection
- Incident response planning and comprehensive cybersecurity training
Conclusion
After reading about multiple malicious code examples, you know that nothing tops vigilance and using the right tools. Subsequently, with BuzzClan by your side, you can stay ahead of your cybercriminals. Moreover, from automated monitoring to training your team to spot dangers and using the best tools for advanced protection, we ensure that nothing slips through the cracks. The question is, how soon are you taking the plunge?
FAQs

Get In Touch