The Ultimate Guide to Web Application Security: Strategies & Best Practices
Deepak Dube
Apr 29, 2025
Close to 42% of companies face external attacks, and 35% of them have found the cause to be defects in their web applications. Cybercriminals are advancing their tactics with each passing second, making investing in web application security all the more important. The attack on Real Estate Wealth Network in 2023 exposed 1.5 billion records, including names, property history, and tax IDs. Hackers take advantage of vulnerabilities in your web app, leading to millions of losses.
So, what can be done to solve these issues and ensure your business is always protected from these attacks? The key lies in understanding the multiple aspects of web application security. We will help you decode each to implement them and secure your business quickly.
What is Web Application Security?
In simple terms, web application security can be defined as the security system for a house. Just like a home needs doors, windows, and alarms to keep the intruders out, the same applies to web application security. It helps you undertake robust security measures to defend your web applications from cybercriminals.
When your web applications are weak, attackers can target and compromise them, leading to massive data breaches and the disclosure of sensitive customer data. Websites that fail to validate user inputs can manipulate queries and gain unauthorized access to your database. A report suggests that 80% of security incidents involve web applications. Thus, it is a must to secure your web apps and follow security best practices to protect your data.
Why Is Web Application Security Important?
It would be safe to say that most of our personal and professional lives are online. From fulfilling our professional commitments to socializing with peers and finding the best means of entertainment, we share a lot of sensitive information online. However, if this data is not adequately protected, hackers can tamper and access it, harassing you for your ransom and even leaking your data.
The damage doesn’t end here; the aftermath of a web application security breach leads to operational disruptions and loss of reputation for your organization. It can even invite multiple penalties if you are not taking data protection regulations seriously. It is estimated that the cost of cybercrime will reach a whopping $10.5 trillion by 2025.
Secure your web apps to avoid these pitfalls and keep up with the evolving threat landscape. To do so, you need to understand the attacks that harm them and that it is not a one-and-done process but a continuous effort that requires monitoring, improving, and updating your online security online security is not a one-and-done process but a continuous effort that requires monitoring, improving, and updating your strategies and frameworks.
Common Threats to Web Applications
When you know about the common threats your web applications face, you will be more prepared to handle them.

Cross-Site Scripting (XSS)
As per Digital Commons, nearly 60% of web apps have some form of XSS. While the numbers are enough to consider carefully, how do these attacks harm your web apps? In these attacks, cybercriminals inject harmful scripts into the web pages viewed by your customers.
The main targets of these attacks are user sessions. They use their tactics to steal cookies and other data without the users’ consent. If an attacker has injected a script in the comment section, when a viewer sees that comment, the script is executed, and cookies are sent to the attacker’s server.
To ensure that such attacks do not harm your web apps, ensure all user inputs are authenticated to prevent malicious scripts from executing. Also, a content security policy (CSP) should be enforced to limit the content that can be loaded and executed in the browser. Lastly, only secure cookie flags should be implemented to prevent cookies from getting stolen.
Insecure Deserialization
Let us explain how insecure deserialization can threaten your web app. Well, it can lead to codes being executed without your knowledge. Insecure deserialization (converting the stored data into the object) happens when malicious data is acted upon without validation. This lets hackers modify serialized objects (converting object data into a byte stream) and execute code when it is deserialized. With this, they can easily bypass security controls and abuse privileges.
Often, cybercriminals create malicious objects and send them to the server. Once the server deserializes it, the attacker gains control of the system. You can save your web apps from these attacks by implementing integrity checks and signatures on serialized data. Also, you must use safe serialization methods and avoid deserializing untrusted data as much as possible.
Brute Force
Did you know that 80% of attacks on web applications involve brute force techniques? In these attacks, cybercriminals use all password combinations till the correct one is figured out. Usually, these attacks are automated to test combinations rapidly. To protect your web apps from these attacks, ensure you and your employees use strong passwords and implement account-locking mechanisms. The latter will help you lock your accounts after a specified number of attempts. Lastly, use multiple-factor authentication to add an extra layer of security.
Session Hijacking
One of the most common attacks on web applications is session hijacking, where an attacker steals a valid session token and poses as a legitimate user. With this, they gain access to sensitive information. Usually, these attacks are conducted in environments without strong session management practices. To ensure your web applications are safe, only use cookies with “Secure and HttpOnly flags.” You must make it a point to implement Transport Layer Security (TLS) for your data. Lastly, regenerating session tokens should be made a common practice.
Insecure Direct Object References (IDOR)
It is time to be aware if your website has poor access controls. These attacks occur when a web app exposes direct access to files or database entries based on user inputs. Once attackers have access to this information, they can gain access to sensitive information. Often, attackers change user IDs and establish access to multiple users’ data. The solution to preventing these threats is simple. Make sure there are proper access controls in place for every request. You must double-check that you are using indirect references and not exposing internal object references in any form.
Remote Code Execution (RCE)
RCE vulnerabilities are a significant cause of concern. In these attacks, attackers execute arbitrary codes (codes not controlled by the software) on a target system. This is detrimental to web applications as cybercriminals can control the system completely, leading to data theft and denial of service. Protecting your web apps from these attacks is easier than you think. All you need to do is validate and sanitize all user inputs. Other measures that will help you maintain top-notch security include limiting file uploads and regularly applying security patches and updates to your software.
Outdated Encryption Methods
Attackers can easily access your web application when passwords are stored in plain text files or weak ciphers. Despite these threats, multiple organizations still store passwords using weak cryptography. So, how can you ensure that your web apps are safe? Use strong industry-standard algorithms to ensure your business is away from such threats. Also, ensure key management practices are in place and avoid storing sensitive data.
Man-in-the-Middle (MITM) Attacks
What if attackers intercept communication between two parties? In these attacks, cybercriminals insert malicious code into your browser and alter communication between you and another website. This is often done to extract funds. These attacks are common when using public Wi-Fi networks. You can prevent these attacks using a security socket layer (SSL) to secure all communication and educate users and employees about phishing attacks and security practices.
Broken Access Control
When you don’t secure your URLs, unauthorized users can access sensitive data. Multiple attackers have been observed altering URLs to access admin pages and restrict resources. To eliminate these threats, ensure you only allow minimal access to employees and enforce stringent access control checks on your server for all resources.
Further Reading
Impact of Web Application Security Failures
Web application security failures can have dire consequences for organizations, including operational disruptions and the loss of user trust. Here is how they can impact your organization.
- Attacks on web applications mean downtime, higher investigation costs, and the stress of facing lawsuits and fines. You will also need to compensate your users for data theft.
- Your customers will be wary of working with you due to your history of data breaches. Moreover, as the news spreads like wildfire, you will have difficulty finding new customers.
- You will need to spend a fortune to restore your operational efficiency, and this loss of time will lead to poor business performance and your ability to deliver services effectively.
- Such instances related to the finance, healthcare, and government sectors can also result in global-scale attacks and even serve as the foundation for fulfilling political motives.
How Does Web Application Security Work?
The whole purpose of web application security is to protect your web apps from basic and advanced threats. The first line of defense is to get your code right by following secure practices. You must validate all inputs and patch all vulnerabilities in real-time. Before you make the web app live, make sure you simulate attacks to find any loopholes. Once done, you must use firewalls and intrusion detection systems to ensure no suspicious activities occur. Despite all these measures, you need to be hyper-vigilant and invest in automated security testing tools to scan for vulnerabilities and stay ahead of cyber attacks. Regular web application assessments will help you build resilience against evolving threats.
Types of Web Application Security
Protecting your web application means investing in the proper techniques and measures to protect your applications. When you know them, you can create the right models and frameworks to build a culture of security.
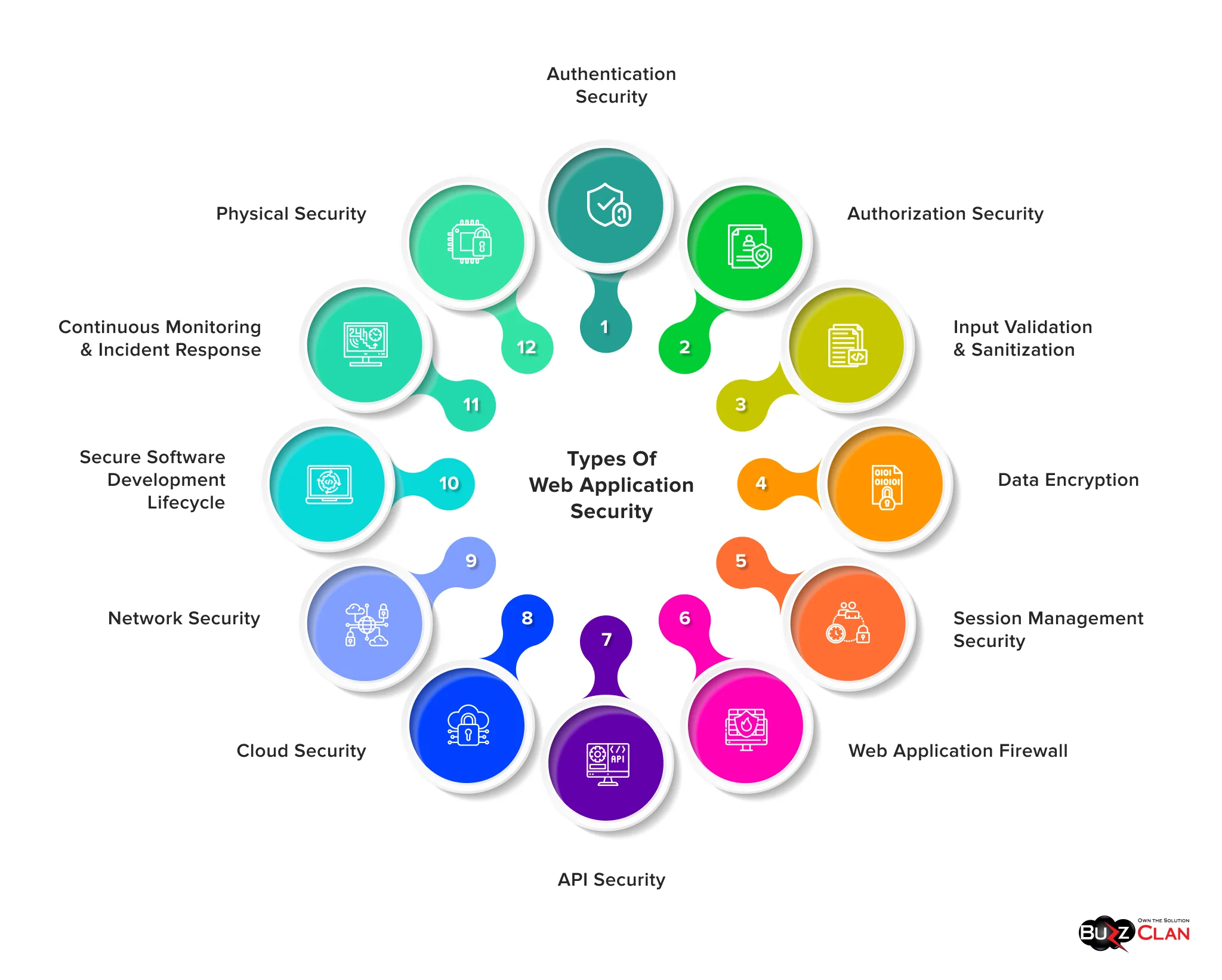
Authentication Security
Half your job is done when only legitimate users can access your web application. All you need to do is verify their identity using biometric verification and multi-factor authentication (MFA). You can also implement Single Sign-On (SSO) to help your users streamline login functions. And how does this benefit your organization? The first thing is that you can enforce an intense login process. This, in turn, helps you prevent brute-force attacks and credential thefts. This simple security measure will save your organization from multiple breaches in the long run.
Authorization Security
Do all your users deserve access to sensitive information? No, right? Thus, you must have proper authorization controls in place. You must put forth measures to decide what a user can/cannot access once logged into your web applications. Doing so will help you prevent the abuse of privileged escalation wherein users meddle with your applications to access resources they don’t have permission to access.
Input Validation and Sanitization
In this web application security technique, all user inputs are first validated and sanitized before the application can take action. This is a must, as it will prevent your applications from SQL injection and XSS, as they exploit poorly handled inputs to execute commands that can harm your application. However, with robust input validation measures in place, all data aspects are thoroughly checked, and sanitization removes the harmful characters, which preserves the integrity of your web application.
Data Encryption
Sensitive information needs to be protected both at rest and in transit. This is what makes encryption techniques a must for businesses. You must ensure secure data transmission between clients and servers to prevent any data from being leaked. This web application security type also involves encrypting information such as passwords and personal databases. As a result, this security aspect helps maintain user trust and maintains the correct sync with data protection regulations like GDPR and HIPAA.
Session Management Security
Often, hackers gain access to user sessions and try to meddle with your web apps. Session management security helps you guard against them by protecting the integrity of user sessions. And how is this done? It is achieved using secure session IDs and setting session timeouts. Not only does this keep user data secure during interactions, but it also helps you create a seamless experience when your customers visit different website pages.
Web Application Firewall (WAF)
It is one of the best security defenses for your web application. But what exactly does it consist of? It is a security layer that filters and monitors HTTP/HTTPS traffic between the application and users. You can easily prevent common web application security threats like XSS, SQL injections, and DDoS attacks by blocking them and not letting them reach your application. The best part is that these firewalls help you prevent both automated and targeted attacks. Lastly, ensure your WAF is configured with the latest security rules to address emerging threats.
API Security
Modern web apps often depend on APIs to ensure data is smoothly exchanged between clients and servers. Securing APIs is necessary as a vulnerable API has led to cybercriminals accessing 650,000 sensitive messages. Multiple passwords were exposed, and penetration testers successfully stole confidential data. To ensure these things don’t happen with your business, authenticate APIs and use rate limiting to prevent abuse of the fed data. Also, secure tokens should be used to allow API access and restrict API endpoints. You must ensure that all data sent from APIs is validated to eliminate risks of injection attacks. If you don’t follow these measures, attackers can easily exploit information if you do not guarantee proper API security.
Cloud Security
Web applications are often hosted on cloud platforms, which is a significant cause of concern. The cloud is vulnerable to multilevel attacks, and you need to actively secure the infrastructure, services, and networks that third-party providers provide. Luckily, cloud security is not rocket science. You can start configuring access controls and encrypting the data stored in the cloud. To ensure advanced protection, you must follow cloud security best practices and comply with regulations.
Network Security
While other web application security types ensure that a particular aspect is addressed, network security covers the entire infrastructure. From firewalls to tools that prevent and detect bad traffic, you can easily monitor and ensure such traffic doesn’t permeate your systems. Wait, there is more to it! You can also leverage virtual private networks (VPNs) to ensure stringent security and limit access to critical resources to get that extra edge.
Secure Software Development Lifecycle (SDLC)
You can better prepare for attacks when web apps are built using the best security practices. Secure SDLC ensures these measures are followed throughout development, and codes are reviewed regularly. This ensures that the code is free of vulnerabilities and that secure design principles further enhance the application’s stability. So, you have to double-check and embed security in every stage of development. This will save you time, hassles, and pain in the later stages and help you build customer trust.
Continuous Monitoring and Incident Response
When you consistently detect suspicious activities and unusual traffic patterns, you can quickly identify recurring patterns and protect your web apps. However, doing this manually can take up much time and resources. Your developers need to handle multiple things and even develop apps for customers. So, to achieve benefits at both ends, ensure you are leveraging Security Information and Event Management (SIEM) tools. These tools are a no-brainer as they help you manage and address the symptoms! Luckily, the benefits don’t end here! They also allow you to minimize potential damages by staying abreast of all the threats and preparing your web apps.
Physical Security
While often ignored, physical security is as essential for web apps as other security types. You must secure your networking equipment, servers, and data centers. But what makes this important? Without physical security, even the most secure applications can be damaged physically. This is why you must have top-notch surveillance, restrict access, and use biometric authentication. This will add a much-needed layer of security and prevent threats from cybercriminals and insiders.
Best Practices for Web Application Security
Web application security involves a careful combination of proactive measures to ensure robust security. You must follow these security metrics to protect your web application from all threats.
- Use Secure Development Practices: When designing your web applications, code them using only industry best practices. This will reduce vulnerabilities and help you address flaws faster. Also, ensure you only implement the features and services needed and permanently disable unnecessary functionality to reduce the attack surface for cybercriminals.
- Protect Your Systems from DDoS Attacks: A simple solution for preventing these attacks is to use DDoS mitigation services. These services are ideal because they use advanced filtration to avoid a surge of malicious traffic from hampering your server’s capacity. As a result, businesses worldwide use these services to protect their servers.
- Multi-Factor Authentication to the Rescue: Adding this extra layer of security is essential for customer trust and top-notch security. Not all your employees and customers need to access sensitive information, so you must ensure they can access limited data.
- Stay Consistent With Security Tests: Automated tools periodically check the system for vulnerabilities and simulate real-world attacks to fix any weaknesses.
- Regular Updates and Patch Management: When your web apps are regularly updated, you can easily prevent supply chain attacks and wade through the most advanced attacks. Also, when you patch application issues proactively, you will know the vulnerable components precisely and can take remedial action.
- Use DNSSEC and Third-party Encryption Management: This ensures that your web application’s DNS (Domain Name System) traffic is sent to the correct servers and is not blocked by attackers. The latter involves renewing certificates and generating private keys to remove the risk of overlooked elements.
- Educate Users and Developers: Training developers and employees is necessary to enforce good cybersecurity practices.
Application Security Testing vs. API Security Testing
Testing the security of your applications and ensuring that your APIs are safe and ideal for establishing communication is necessary. Let’s understand the fundamental differences between application security and API security testing.
| Aspect | Application Security Testing | API Security Testing |
|---|---|---|
| Concept | The focal point is identifying and mitigating vulnerabilities in all application versions. | The focus is limited to identifying and securing issues related to APIs. |
| Main Focus | The focus is on protecting web apps from threats such as SQL injection, XSS, CSRF, and authentication bypass. | The focus is on securing API endpoints from broken object-level authorization, injection, excessive data exposure, and other threats. |
| Key Testing Methods |
|
|
| Common Vulnerabilities Tested |
|
|
| Compliance Requirements | Covers regulations like PCI DSS, GDPR, HIPAA, and OWASP ASVS. | Aligns with OWASP API Security Top 10, GDPR, PCI DSS, and industry-specific API security standards. |
| End Users | Security teams and developers focused on the entire application stack. | API developers, architects, and security professionals are focusing on API-specific risks. |
| Frequency of Testing | Conducted during development, deployment, and periodically in production. | Ongoing during API development, with frequent runtime monitoring in production. |
| Tools Used |
|
|
Advanced Topics in Web Application Security
As the techniques of hackers evolve, so will the security frameworks and tactics. Let’s know about the advanced topics in web application security that will help you stay ahead of cybercriminals.
Zero Trust Security Model
Assuming the worst-case scenario is what this model is perfect at. All bad jokes on us! Well, this is a cybersecurity framework that has “Zero Trust” on all networks. There is an inherent assumption of lurking threats inside and outside the network. Therefore, all entities are verified, monitored, and micro-segmented before giving them access. Employees who wish to access sensitive information must first confirm their identity via multi-factor authentication (MFA) and then undergo device compliance checks. As a result, multiple apps have been released that ensure secure access and don’t rely on traditional network parameters.
How Do Security Misconfigurations Affect Your Web App?
Incomplete configurations, unattended systems, and default settings are a recipe for disaster. Yes, you heard that right! Security misconfigurations happen when your web apps, systems, or servers are assumed to be working in perfect shape. In contrast, they have not been appropriately configured and can easily expose sensitive data. These flaws end up being the ground for high-end data breaches. The well-known Colonial Pipeline data breach was successful due to improper system configurations! This further highlights the need to secure environments effectively. Thus, ensure you never leave unused services enabled or expose sensitive files, as attackers can use them to exploit your system and create losses worth millions of dollars.
Security Automation and DevSecOps
What if you could automate repetitive security tasks and identify issues earlier in the software lifecycle? That would help you detect threats faster and solve problems before they become a giant menace. Luckily, security automation and DevSecOps help you do that and much more! And how do you do that? You must embed them in your CI/CD (Continuous Integration and Continuous Delivery/Deployment) pipelines. Moreover, you use application security testing tools to scan code for vulnerabilities in real time when changes are being made. This will reduce instances of human error, lead to faster deliveries, and facilitate a culture where web application security is a joint responsibility.
Threat Modeling
Have you ever thought about what is needed to destroy a cybercriminal’s pursuits? The answer lies in being thorough and paying keen attention to detail. Threat modeling is one such process that involves an exhaustive analysis of risks and mitigating security risks before they can become a threat. For the same, data flows, application architecture, and potential vectors are scrutinized to predict and address any vulnerabilities in the web application. These models are often used by developers building apps for fintech firms. They create environments to check whether hackers can access customer data or conduct DDoS attacks. You can also automate these processes with tools like Microsoft Threat Modeling Tool or STRIDE.
OWASP ( Open Worldwide Application Security Project )Top 10 Model
laimed to be the bible of cybersecurity frameworks, the OWASP Top 10 helps developers and organizations understand common web app vulnerabilities. As a result, organizations worldwide follow this model to keep their applications and systems safe from minor and advanced attacks. When well-versed in these vulnerabilities and their solutions, you can quickly look forward to secure application development and fulfilling compliance requirements.
Key Tools for Securing Web Applications
Here is a list of web application security solutions to help you secure your web apps.
| DNS Protection | Password Managers | Multi-Factor Authentication |
|---|---|---|
| Cisco Umbrella | 1Password | Authy |
| CleanBrowsing | Dashlane | Duo |
| Neustar | LastPass | Microsoft Authenticator |
| Threat Intelligence | Data Loss Prevention | Web Application Firewall |
| CrowdStrike | Cyberhaven | Akamai |
| Mandiant | Forcepoint | Cloudflare |
| Splunk | Proofpoint | Imperva |
| Antivirus Software | Encryption Tools | Firewalls |
| Bitfinder | Axcrypt | Cisco Umbrella |
| Kaspersky | NordLocker | Fortinet |
| Norton | Veracrypt | Palo Alto |
| VPNs | Email Security | Endpoint Security |
| ExpressVPN | Microsoft Defender | Cisco Secure |
| NordVPN | Mimecast | Crowd Strike |
| Surfshark | Proofpoint | SentinelOne |
| Vulnerability Management | Privileged Access Management | Identity and Access Management |
| Nessus | BeyondTrust | Microsoft Entra ID |
| Qualys | CyberArk | Okta |
| Rapid | One Login | Zluri |
Compliance and Regulatory Standards in Web Security
No organization is entirely immune to cyberattacks. This is what makes complying with cybersecurity standards a must. Doing so will lay the ground for smooth operations and help you build customer trust. Below are some standard regulations that will help your organization stay compliant.
- The California Consumer Privacy Act (CCPA): The benefits consumers by giving them more control over the data businesses collect about them. The act applies to multiple organizations, which must be transparent about their data practices.
- Cybersecurity Maturity Model Certification (CMMC): The act has helped multiple organizations implement strong cybersecurity measures and protect sensitive information. It applies to all organizations that handle controlled unclassified information (CUI). For the same, you need to receive an audit from a third-party organization to see if you fulfill the minimum requirements to bid on U.S. Department of Defense (DoD) contracts.
- Payment Card Industry Data Security Standard (PCI DSS): This compliance standard ensures that all organizations offer a secure environment to store credit card information. Organization compliance must be validated every year.
- The Health Insurance Portability and Accountability Act (HIPAA): It is a requirement for all healthcare providers or professionals who handle protected health information (PHI).
- System and Organization Control 2 (SOC 2): This standard lays down guidelines for securely handling customer records and maintaining their integrity and privacy. However, the reports are tailored to the organization’s structure, and the managers are responsible for designing their controls and procedures. This compliance standard is significant in securing data for software as a service (SaaS) and cloud computing vendors.
- General Data Protection Regulation (GDPR): This is a well-known standard and applies to organizations located in the European Union (EU) or that target individuals in the EU (irrespective of their location).
- National Institute of Standards and Technology (NIST): This standard aims to promote innovation and boost the quality of life through technological advancements. The framework lays down guidelines for managing information security systems effectively and reducing supply chain risks.
- The Sarbanes-Oxley Act (SOX): It applies to publicly traded companies and focuses on ensuring top-notch financial reporting and data integrity. It will help you implement safeguards to prevent data tampering and maintain audit trails to keep your data accurate.
How Application Security Testing Reduces Organizational Risk?
Reducing cyber risks is a must for all organizations. Let’s see how application security testing aids this:
- It identifies and mitigates vulnerabilities that hackers can exploit to steal sensitive data.
- Application security testing ensures customer data is protected against breaches and leaks and complies with data protection regulations.
- It protects against fines, penalties, and legal consequences for not meeting compliance standards.
- Since these tests are conducted early in the development lifecycle, you can reduce the cost of addressing security issues in the later stages.
Further Reading
Protect Your Web Applications With BuzzClan’s Enterprise-Grade Security
Protecting web applications from advanced attacks can be challenging. It requires more than using the right tools and techniques. We understand this and thus provide you with the best audits and logging functionalities to protect your systems from threats. Our team of experts builds a detailed roadmap following security best practices to ensure your systems are always protected and secured from basic and advanced threats. BuzzClan provides enterprise-grade security that helps you detect the most complex attacks and safeguard your systems.
- Multi-layered security architecture to protect your systems
- Automated compliance monitoring to ensure zero legal hassles
- 24/7 threat detection and response for proactive threat detection
- Incident response planning and comprehensive cybersecurity training
- 99.99% guaranteed uptime
Conclusion
A good business prevents and does not mitigate threats. While these words sound exciting, there are times when you will be at your wits’ end on how to stay on par with cybercriminals. Fret not, and take a deep breath. Just ensure you have a detailed plan to secure your sensitive web applications. Nothing is better than having an inventory of all your web applications!
While you cannot avert all attacks, you must prioritize updating your cybersecurity knowledge and imparting it to your team. When they know system vulnerabilities, they can take proactive steps to prevent them. Investing in the right tools, following security best practices, and staying updated on trends will set the proper foundation for your business and help you build a robust web security landscape.
FAQs

Get In Touch