What is the Goal of an Insider Threat Program? Why Enterprises Need to Care?
Priya Patel
Apr 9, 2025
What is Insider Threat?
An insider threat is a type of cyberattack caused by the intentional or unintentional harm motive of a company’s “insiders.” These insiders can be former or existing employees, business partners, third-party vendors, or contractors. An insider threat occurs when the authorized access of a company’s system, data, or network is misused (purposefully/accidentally).
The aftermath of an insider threat can be financial losses, reputational damage, data spillage, or even legal consequences. While other businesses and third-party vendors are also types of insider threats, the primary factor remains human error. It ranks top, accounting for over 61% of insider threat incidents. This means that most insider threats aren’t malicious but accidental and done by trusted employees.
Types of Insider Threats
There are five major types of insider threats:
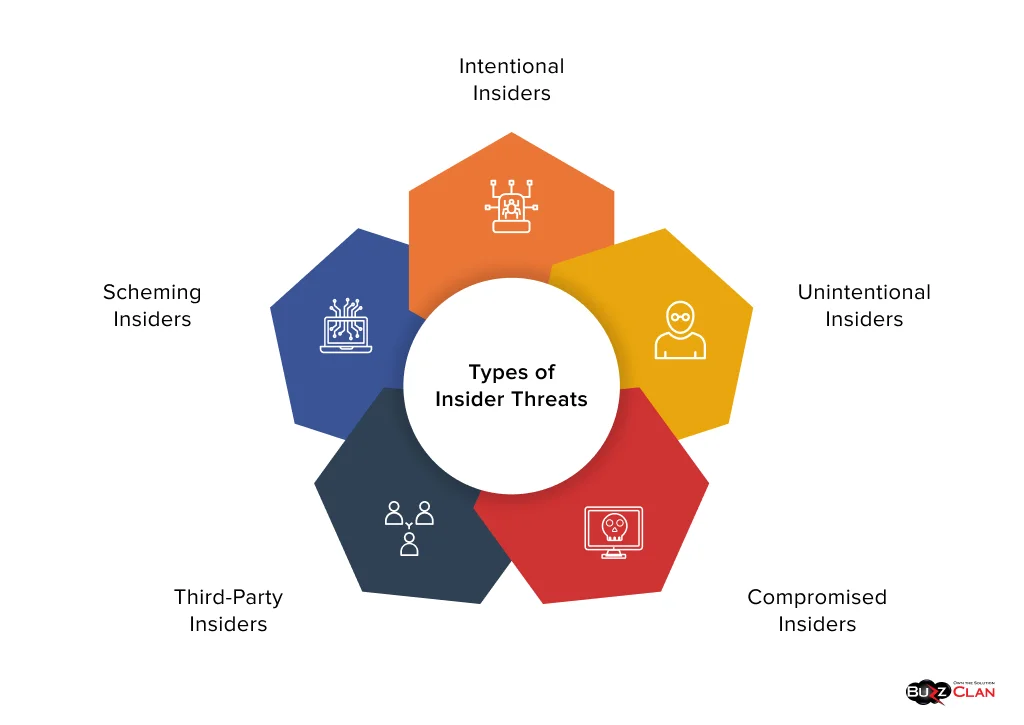
Intentional Insiders
An intentional insider is someone who purposefully misuses authorized access and leaks sensitive information. Their detection becomes challenging as they have legitimate access to the system.
For example, an IT admin may sell company data on the dark web for monetary benefits or because of resentment.
Unintentional Insiders
These insiders don’t maliciously leak sensitive information, but their actions do. They accidentally do something that results in data misuse.
For example, a manager may send a confidential email that should have been sent to a client but was sent to her friend by mistake, which can lead to data leaks.
Compromised Insiders
Compromised insiders are employees or stakeholders whose access has been breached by an outside cyber criminal. This can happen because of their negligence or lack of awareness.
For example, vishing, phishing, or social engineering attacks on employees can lead to the leak of essential emails, company details, or PII.
Third-Party Insiders
Businesses that share customer databases, PII, and others with their service providers or clients stay highly vulnerable to insider threats. These parties may have weak security protocols, which the attackers can break, indirectly exposing your database.
Scheming Insiders
In this type, one or more company insiders scheme with an external party to provide what they want to launch an attack on, such as digital assets or intellectual properties. They then launch cybersecurity attacks, like ransomware-as-a-service, malware, and other key threats.
What is the Goal of an Insider Threat Program?
An insider threat program is a set of strategies that protect a company’s valuable digital assets and data from employees, malicious actors, and third parties. The main goal of an insider threat program is to deter insiders, detect risks, and mitigate threats. Let’s understand them in detail below:
Deter Insiders
How to prevent insider threats? By deterring. Deterring insiders involves preventing or discouraging individuals with authorized access to an organization’s data from acting maliciously or negligently, potentially causing harm. It involves:
- Laying the foundation of a solid security framework with clear policies and procedures regarding access and security behaviour.
- Providing training and awareness programmes to educate employees about cyber risks and the do’s and don’ts to save themselves from attacks.
- Using high-tech for detecting unusual behaviours, like changes in performance or increased secrecy.
Detect Risks
Some insider risks persist even after preventive measures are taken. For such risks, effective detection should take place. Insider threat programs consist of various essential processes and technologies, detecting the smallest of risks that can cause insider threats:
- User behavior analytics and sophisticated monitoring systems that detect sudden or unfamiliar patterns.
- Organizations implement incident response plans so that when a potential risk is detected, they can eliminate it ASAP.
- Frequent risk assessments all over the company, quarterly, half-yearly, or yearly.
- Most of the threats are human error. Foster a security culture where people can report suspicious behaviours or moments.
Mitigate Threats
Even with deterrence and detection, some insider threats still materialize in companies. Now, how to mitigate insider threats? Consider the following:
- Launch incident response plans in the affected areas to stop the threat from expanding. Prepare a solid plan that includes containment (limiting the attack), remediation (fixing the damage), and recovery (bringing damaged data back).
- Data loss prevention is done to prevent data from being exfiltrated further.
- Limit access to sensitive information based on the principle of least privilege.
- Access control revocation (the act of quickly withdrawing/disabling access) is used for employees who don’t have a legitimate need to access specific systems or data, minimizing the risks.
The Role of AI and Automation in Insider Threat Detection
AI in cybersecurity has revolutionized companies and their security infrastructure. Let’s see how AI and automation evolve the standard insider threat detection in businesses:
Real-time Monitoring & Response
AI-powered systems and tools monitor much data in real time (at a far more human pace). This helps companies monitor everything quickly and continuously, identifying suspicious activities faster than ever. After this, automation does its magic. Automation applies response plans automatically and swiftly, as soon as any threat occurs. Just like that, AI saves money, data, and companies’ reputations, mitigating threats.
Behavioural Analysis and Anomaly Detection
AI (specifically ML) continuously monitors user behavior (login times, access, files, network) to identify abnormal activities indicating potential threats. This automatically improves a company’s insider risk posture.
AI-Augmented DFIR
What’s DFIR? It is digital forensics and incident response. It is like the team investigating if a breach/break-in happened (digital forensics) and figuring out how to fix the damage and prevent it from happening again (incident response). AI here is like a super-assistant that watches everyone’s actions inside the house and works with the detective tools. XAI and federated learning are instilled in this tech, making its operations trustworthy and reliable.
Similar to these roles of AI in insider threat detection, a trendy strategy is AI-powered emotional analysis. Under this, AI tools are deployed to analyze employee communication patterns from emails or group chats, examining people’s emotions that can result in potential risks later on.
How can BuzzClan help you leverage AI and automation? With its AI-driven tech stack, BuzzClan can help your business by providing predictive analytics, security operations optimization, incident investigation, and more.
How to Build an Insider Threat Program?
Given the average cost of an insider threat breach, $17.4 million in 2025, having an insider threat program is necessary than ever before. Follow these phases and build an effective insider threat program for your business:
Phase 1: Establishing the Foundation
Efforts don’t last long if the foundation isn’t strong enough to withstand the impacts of security breaches.
- Leadership Buy-in: Get leaders’ support and resources and specify the scope.
- Define Assets & Risks: What are your assets? Where and how lethal are the insider risks? These answers are defined in this stage.
- Clear Policies & Team: Form rules and processes with a code of conduct matching the business objectives. Alongside this, a team should be created to carry out the program.
Phase 2: Implementing the Program
The program should be implemented using best practices, employee contributions, and conscious awareness in this phase.
- Technical Controls: Implement access control systems, data loss prevention capabilities, endpoint security, and regular checks for behavior analysis and log monitoring.
- Employee Training: Teach employees to recognize suspicious behavior while determining the processes to detect possible threats.
- Incident Response Plan: A strategic plan should be developed to respond correctly when a threat materializes.
Phase 3: Maintaining and Improving the Program
Things sustain themselves when they are maintained. Similarly, maintaining and improving the program becomes the highest priority, as not keeping up with advanced technology can result in its outdating.
- Continuous Improvement: Regularly review policies, monitor systems, assess risks, foster a security culture, and learn from incidents.
How an Insider Threat Program Benefits Your Organization
We answered the question: What is the goal of an insider threat program? Let’s see how the program benefits organizations by strengthening their cybersecurity initiatives and infrastructure.
- Reduced Vulnerability: When internal risks are identified and reduced, the company’s overall vulnerabilities are minimized.
- Business Growth & Continuity: The company automatically grows when the security is robust. Because of breaches, the company loses millions of dollars, leading to declined growth.
- Regulatory Adherence: These programs let organizations enter the security criteria of regulatory jurisdictions, which is further needed to carry out operations.
- Promoting Security Culture: Businesses promote accountability by implementing security policies and procedures. This encourages employees to report suspicious activities if they occur, hence enhancing a security culture.
Best Practices to Implement and Maintain an Insider Threat Program
Want to see insider threat programs work effectively over a long period? Follow these best practices:
- Sort valuable assets along with vulnerable points that need special attention.
- The organization should support active cooperation between IT staff, HR managers, and legal officials to develop comprehensive security measures.
- Your organization must execute periodic updates to security protocols and incident management procedures.
- The workplace should maintain a system allowing employees to report unusual conduct without backlash.
- For the detection stage, integrate data analytics and machine learning so that anomalies can be detected.
Conclusion
To summarize, insider threat programs are internal patrol systems within the castle (business) for preventing and monitoring potential or actual insider threats. Without them, the possible and actual risks spread by types of insiders (employees, third parties, or malicious actors) can cause significant financial loss and damage to company goodwill. To avoid this, a business must implement an insider threat program. The program aims to deter, detect, and mitigate insider threats.
Run in the race of AI for success! Organizations step up their cybersecurity infrastructure with AI and automation, like an extra shield. Don’t get left behind! You should also do the same with the points mentioned earlier. Moreover, an effective insider threat program should be built with best practices to maintain the program over long periods. However, if you want a serene mind and a concrete cyber defense, contact BuzzClan for their valuable contributions and AI-driven security practices.
FAQs

Get In Touch