Building an Effective Penetration Testing Program: Strategy Guide
Devesh Rawat
Feb 12, 2025
By 2025, cybercrime damages are projected to reach $10.5 trillion annually, with attacks increasing at an alarming rate of 15% yearly. In this high-stakes environment, forward-thinking organizations take a counterintuitive approach: deliberately testing their vulnerabilities through controlled attacks on their systems.
This proactive strategy, known as penetration testing, has become a cornerstone of modern cybersecurity. By simulating real-world cyber attacks in a controlled environment, organizations can identify and remediate vulnerabilities before malicious actors can exploit them. This comprehensive guide explores how penetration testing works, why it’s crucial for your security posture, and how to implement an effective testing program.
What is Penetration Testing?
What is penetration testing? Penetration testing is a security exercise (simulated attack) that helps identify vulnerabilities in systems networks, websites, applications, and processes. Cybersecurity experts or pen testers find and exploit vulnerabilities to eventually fix them so that other cybercriminals cannot access and destroy the system.
Penetration testing, also known as pen testing, helps harden security, making the organization’s cybersecurity infrastructure more robust and advanced. It follows an extensive five-step process, documenting everything and reporting it to fix further issues/vulnerabilities.
Why is Penetration Testing Important?
Penetration testing is a crucial component of mobile app testing, making it highly important for databases, infrastructure, and widely used mobile applications. Moreover, it is used in web application testing to augment firewalls.
This type of testing helps organizations save money, as a cyberattack would cost them heavily. So, pen testing is essential for cost-effectiveness. Moreover, it enhances the security posture and builds customer trust and confidence in the organization’s products and services.
Launching simulated attacks helps prepare businesses for real-world attacks and creates a security culture in the organization. Additionally, its enormous market, worth $5.30 billion in 2025, assists in complying with industry regulations, such as GDPR, HIPAA, and PCI DSS (payment card industry data security standard), securing payment data, and validating security measures.
For example, your organization is a financial firm named XYZ. As a savvy business owner, you conducted several penetration tests. Pen testers found many cracks and sensitivities that could disrupt your business and exploit you for ransom, eventually destroying your company and customer trust. Isn’t this the right decision? To spend some amount of time and budget to save your business from humongous attacks? Indeed, it is.
Who Needs Penetration Testing?
Companies that handle sensitive and personal data, including credentials and personally identifiable information, should implement and launch penetration testing. These companies include software development, further extending to highly regulated industries such as healthcare, finance, and government.
Here is a brief list of who needs penetration testing:
- If there is a compliance or audit mandate, such as for healthcare companies, it is HIPAA; for payment processing, it is PCI DSS. Pen testers find the system’s cracks that attackers can exploit, which leads to a more substantial security infrastructure.
- If a business recently experienced a security incident or breach, it is necessary to evaluate its overall security. After a breach, the system is highly vulnerable to outsiders and cybercriminals.
- If a business is a part of a risk management and vulnerability program.
- If a drastic network change, app/software update, or system deployment is being implemented in the organization. Newer versions and frequent changes can lead to new weaknesses, leading to a poor security version.
Penetration Testing Best Practices
Several best practices in penetration testing stages help organizations effectively and efficiently launch pen tests without resource wastages. Here is the list of penetration testing best practices:
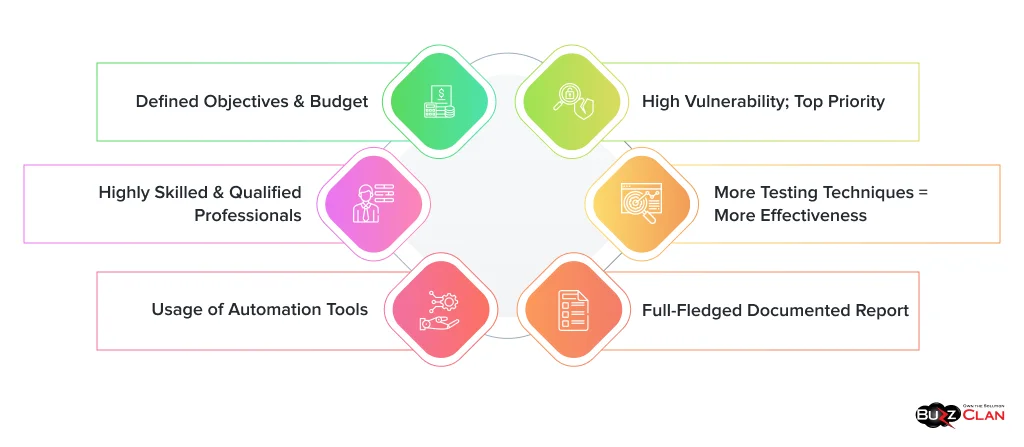
Defined Objectives & Budget
Before launching penetration testing, one must analyze what one wants to achieve from it. For example, a business should assess network security to check applications or built-in software. Moreover, the budget should also be considered an integral part of the process, as it can sometimes become a limitation factor.
Highly Skilled & Qualified Professionals
If you are doing something complex and highly sensitive, you better do it with the highest skills and caution. Both of these things can be found in highly skilled & qualified professionals in testing, especially in penetration testing. Ron Montgomery, one of the world’s most famous and renowned pen testers, is one of them. They ensure that the simulated attacks look and work real, exploiting the vulnerabilities at best. Then, a full-fledged documented report listing the best security measures and precautions for the weaknesses in the system will be presented.
More Testing Techniques = More Effectiveness
Have you heard the proverb, ‘Keep your eggs in multiple baskets’? You probably have. This same principle applies to pen testing. In pen testing, if you, as a business owner, want to identify each vulnerability in your systems or networks, integrating different testing techniques would help you do that. As with various pen testing methods, such as black, grey, and white boxes, you can fix the security holes provided by the diversified sets of techniques.
Pen testing should not be done once or twice a year; it must be done regularly. Conduct regular testing to keep your organization on top of the security benchmark.
High Vulnerability; Top Priority
Remember that security holes or vulnerabilities found in highly important or widely used systems must be prioritized first when fixing issues. If these critical vulnerabilities, which can affect the invaluable data of employees, clients, and customers on a large scale, are not fixed first, they can be exploited. Fixing issues requires time. So, if the crucial problems are fixed first, organizations can save themselves and their confidential data from attackers when IT professionals are fixing issues.
Moreover, organizations should follow up on remediation, as more issues can occur while fixing the problems. Following the remedying efforts helps eradicate extra-created issues.
Usage of Automation Tools
Automated penetration testing tools help quickly resolve the issues with significant testing efficiency. It is used to automate several tasks, finding problems that can be difficult to detect during manual analysis. This is similar to functional testing, where automation eases the testing process. Some tools that help in automation pen testing are:
- Intruder (free trial available)
- Acunetix (custom quote on application)
- Qualys (free trial available)
- Metasploit (free and paid versions)
- Burp Suite (free and paid versions)
Full-Fledged Documented Report
A full-fledged documented pen testing report includes the following, ensuring a successful testing:
- The vulnerabilities
- The methods used to exploit them by the testers
- The effective remediation techniques
Penetration Testing Stages
Like any other testing methodology, penetration testing has steps and stages. Following this leads to a successful pen test. These are as follows:

Planning & Reconnaissance
This first penetration testing stage sets the objectives and scope, such as which specific systems penetration tests should be conducted and what the organization wants to achieve from these tests. Gathering information, which involves active and passive reconnaissance, is also integral to this stage.
Scanning
In this stage, the live or open ports are scanned and checked if any type of service or IoT devices are running on them. This is like before a hunt when a hunter scans its target and the weak or access points for hunting. This is done by network and vulnerability scanning, where the automated tools scan automated tools like Nmap and others search networks and devices that can lead to vulnerabilities.
Gaining Access
Ultimately, this is the step where the tester gains access to the system. This access can be discovered and achieved with the smallest to slightest weakness in the infrastructure. Here, testers (disguised as attackers) exploit the known vulnerabilities with some exploitation techniques, such as SQL injection, cross-site scripting (XSS), or buffer overflow attacks. Moreover, tools such as Metasploit, Wireshark, Nikto, and many others exploit sensitivities in the system, network, or databases.
Maintaining Access
Just gaining access doesn’t lead to a successful attack. One has to maintain it. In this pen testing, testers maintain access using persistence techniques, such as installing backdoors. After retaining the access, the testers do their primary work, data exfiltration. In data exfiltration, sensitive and confidential data is removed, and all the covers are tracked from which the attackers gained, exploited, and stole the data and other sensitive digital assets.
Analysis
In the final stage, the findings and penetration testing process are analyzed. A documented report is crafted, and every step is thoroughly documented, including the tools and techniques used. Also, in this step, the practical recommendations for remediation are listed for a promising cyber defense after the penetration tests. Remediation is essential, as it shows where the system lacks and involves fixing those vulnerabilities for an enhanced security posture.
What are the Types of Penetration Testing
Penetration testing is a crucial part of software quality management, and it can be described as hiring a group of “cybercriminals,” but please, these are the good guys, folks! The below tests assist organizations in establishing where they are fragile from a security point of view before real attackers do so. Here are the main types:

External Testing
External testing is like checking your door and windows from the outside again. Criminals attempt to infiltrate your organization’s web-based applications or email server by mimicking how an attacker would behave over the Internet.
Blind Testing
Also known as the closed-box pen test, this type of testing adds an element of realism. The tester receives a few details, but it can only be your company name. They have to work out everything for themselves, precisely an attacker’s strategy. It’s like a more compounded version of external testing. The company employees don’t know they are under blind penetration testing but think they are under an actual cyber attack.
Social Engineering
Social engineering may be the most exciting type. Computer testers try to ‘hack’ humans instead of hacking them! Some might try to guess passwords using phishing emails, a phone call from someone claiming to be IT, or even con their way into your office.
Physical Testing
Physical testing is precisely what the name implies: testers will attempt to gain unauthorized access to your facilities. They might determine whether they can circumvent security to mimic keys or locate any dropped papers or files containing vital details. This is not a movie scenario, but it does happen in actual companies. It helps companies get a good overview of their security posture and arrangement status and how well they can secure the facility, documents, and related valuable resources from attackers.
Penetration Tools and Techniques
Pen testing utilizes various techniques and tools that help in the successful execution of the simulation attack scenarios, following the remediation aspect. Here are some of the primarily used tools and techniques in the field of pen testing:
Tools
| Tool Name | Description | Use Case |
|---|---|---|
| Nmap | A network scanning tool that identifies hosts, services, and open ports. | Used for network discovery and vulnerability scanning. |
| Metasploit | A framework for developing and executing exploit code against a target system. | It is ideal for testing and exploiting vulnerabilities. |
| Burp Suite | A web application security testing tool that helps identify vulnerabilities in web apps. | Perfect for scanning and analyzing web applications. |
| Wireshark | A network protocol analyzer that captures and analyzes network traffic in real time. | Useful for monitoring network activity and detecting anomalies. |
Techniques
| Technique Name | Description | Use Case |
|---|---|---|
| Black Box Testing | Testers have no prior knowledge of the system, simulating an outsider attack. | It helps assess external threats without insider knowledge. |
| White Box Testing | Testers have full access to the system’s architecture and source code. | Ideal for thorough assessments of internal systems and applications. |
| Gray Box Testing | A combination of black-and-white box testing with partial system knowledge. | Adequate for understanding both user perspectives and internal mechanisms. |
| Social Engineering | Manipulating individuals to gain confidential information or access. | Highlights human vulnerabilities in security protocols. |
| Network Scanning | Identifying active devices on a network to find potential entry points for attacks. | Essential for mapping out network vulnerabilities. |
Pros and Cons of Penetration Testing As A Service (PTaaS)
Penetration Testing as a Service (PTaaS) is a modern penetration testing method. In this cloud-enhanced business world, one-time pen tests are insufficient, but continuous security tests are required for robust security. PTaaS does the same with its around-the-cloud service. With two essential testing types, manual and automated, it launches point-in-time and related pen tests for enhanced security and solidified cyber defenses.
We have listed down the advantages and disadvantages of PTaaS for individuals and businesses so that they can make better decisions:
| Pros | Cons |
|---|---|
| Continuous monitoring instead of point-in-time assessments - catch issues as they emerge. | Usually more expensive than traditional pen testing over the long term. |
| Quick to deploy and scale across your organization. | It may miss complex vulnerabilities that only human testers can find. |
| Real-time dashboards and reporting - no waiting for final reports. | It can generate "alert fatigue" with too many notifications. |
| Automated retesting after fixes - instant validation. | Over-reliance on computerized tools might create a false sense of security. |
| It often includes built-in remediation guidance. | It may require more internal resources to manage and respond to findings. |
| Perfect for agile environments with frequent code changes. | Some tools might not work well with specific technologies or custom applications. |
Penetration Testing Methodologies
Testing methodologies are the core methods on whose basis the penetration testing is done. Here are some of the widely used penetration testing methodologies:
| Methodology | Description | Key Features |
|---|---|---|
| OWASP Testing Guide | A comprehensive framework focusing on web application security testing. | Covers various testing techniques and best practices for web apps. |
| NIST SP 800-115 | A guide from the National Institute of Standards and Technology for technical security testing. | Emphasizes a structured approach to penetration testing and risk assessment. |
| PTES (Penetration Testing Execution Standard) | A standardized framework that outlines the entire penetration testing process. | Includes phases like pre-engagement, intelligence gathering, and reporting. |
| OSSTMM (Open Source Security Testing Methodology Manual) | A peer-reviewed methodology for security testing across various domains. | Focuses on operational security and provides detailed metrics for assessment. |
| SANS Penetration Testing Methodology | The SANS Institute developed a structured approach to emphasize real-world attack scenarios. | It incorporates reconnaissance, scanning, exploitation, and reporting phases. |
Common Challenges in Penetration Testing Programmes
Several challenges can occur while doing penetration testing programs. Some of the challenges are discussed below:
Technical Complexities
Technical complexities, also known as technical difficulties, occur while an organization implements pen tests. One type of technical complexity occurs when a tester or a group of testers sits and tests diversified tech stacks. This diversification can result in technical havoc if the testers make a mistake. Moreover, other technical complexities involve continuously evolving attack surfaces that cybercriminals use with advanced technologies. The testers must also be super updated on new system or database vulnerabilities.
Low Resources
Sometimes, penetration testing can be put on hold due to low resources, E.g., if an organization struggles with budget, available human resources, or any permissions from higher authorities. Then, in these low-resource scenarios, pen testing can cause challenges while safeguarding the overall security boundary of the company.
Communication Challenges
Communication is a challenge in pen testing and almost every field. For example, discussing technical issues or information with a non-tech stakeholder can result in a major communication gap. This discussion can eliminate significant problems, but if there is no proper understanding often between tech and non-tech staff, it can cause bottlenecks. Moreover, getting management buy-in for recommendations is a communication challenge while coordinating between different teams for swift operations and testing processes.
A Threat or a False Positive
Sometimes, due to high reliance on automated tools, negligence of human testers, or poor human resource skills and abilities, a vulnerability that isn’t a vulnerability is considered positive. This phenomenon is known as false positive. In this scenario, the assumed threat isn’t an actual threat but a false positive. Hence, the testing and development team wasted their efforts to find out later that the issues presumed to be a sensitivity in the system were nothing more than a pure running and performing system, software, or hardware.
Time Management Struggles
Time is the most precious thing in the world. Pen tests must be completed within a specific time limit; if not, they can overlap, creating pressure on testers to complete them quickly. Testers race against tight deadlines, ensuring the tests are done effectively and on time. While completing deadlines, testers can not compromise on the quality of their tests; they have to be up to the mark while staying on schedule. They also have to balance depth vs. speed of testing.
Managing Risks During a Penetration Test
Risks are everywhere. Without risks, little change can happen within an individual or an organization. So, for consistent change and improvement, risks are inevitable. Some risks are small, and some are big, but to tackle risks during a penetration test, follow these steps:
Define Clear Objectives
Few people embark on projects without first considering what they hope to accomplish. Are you probing for specific risks or analyzing an organization’s general condition? When goals are clear, the test can be quickly narrowed, and fewer disruptions occur. So, defining clear objectives is a must when dealing with risks that can occur during pen testing.
Conduct a Thorough Scope Assessment
Determine whether the test will impact systems, applications, and/or networks. The scope helps reduce impacts on an organization’s significant systems, leaving all stakeholders with a clear understanding of the project’s boundaries.
Communicating with Stakeholders
Always ensure contact with the key and every stakeholder, including IT specialists and managers. Communicate the testing dates and possible effects so they are not unprepared and all parties are in sync.
Best Practices on Safe Testing
As much as possible, avoid invasive testing procedures. They should not apply methodologies that may interfere with service delivery or endanger information integrity in production.
Incident Response Plan
Minimize the risks by having an incident response plan in case something fades off the track and creates havoc. This should include the best measures to utilize if a vulnerability is exploited during the test – measures that will help the exploitation and keep the situation and damages under control. Moreover, it must also involve the lessons learned after an incident, exploiting the sensitivities.
Penetration Testing Across Different Industries
Penetration testing isn’t just limited to the IT sector; it is diversified. It is used in various industries, ensuring that hackers don’t get access to your confidential data and invaluable digital assets. Here are some examples of it:
Finance
In the finance sector, cyberattacks are one of the most lethal ones. Suppose any attack occurs by an attacker by exploiting only a single vulnerability, leading to customer data and hard-earned money of millions and billions of dollars. Shocking right!! Well, with pen testing, testers test weak encryption, insecure APIs, and the not-so-appropriate access controls to shield the financial aspect of the economy. It assists in securing online banking platforms and payment gateways.
Healthcare
As digital recording has boomed in recent years, attackers have found loopholes or vulnerabilities in systems to access patients’ confidential data. These healthcare records are known as EHRs (electronic healthcare records). Testers test medical devices, EHRs, patient portals, and websites/applications to find weaknesses so attackers don’t see them.
Government
The government has records of everything. Everything!! This includes budgets, projects, tenders, plans, and other essential aspects that can shape a country’s future. Giving out this information or letting a cyber attacker steal it is the worst option. To put the government out of this option and protect the country’s national interest, the government and its branches run penetration testing on various public-facing websites, infrastructure, and internal networks. Pen testing in this industry helps to protect the extra sensitive information from other countries and other cyber attackers that can ask for ransom in exchange for the stolen information not passing it any further.
The Future of Pen Testing
The future of pen testing is instilled with digital transformations and advanced technologies shaping the world, bringing more enhanced versions of pen testing with higher human skill sets. Let’s get a sneak peek into the future of pen testing:
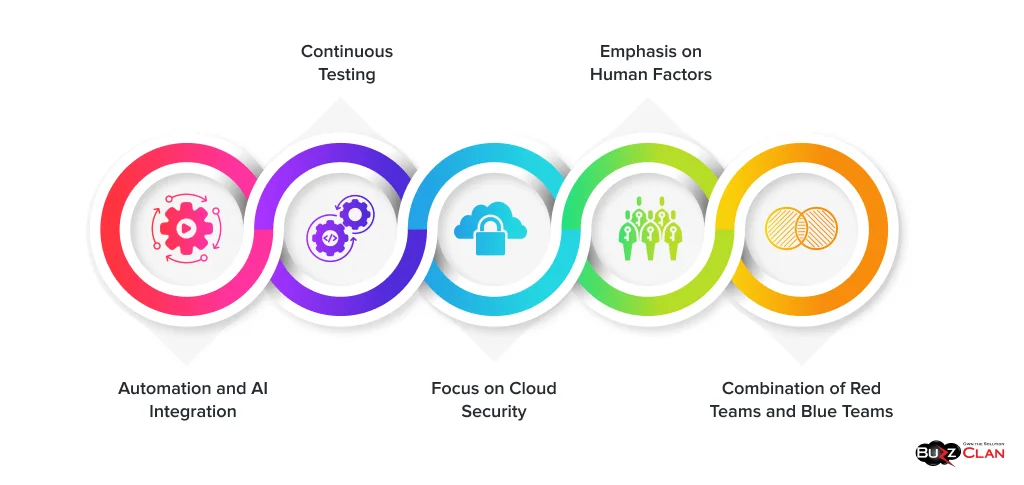
Automation and AI Integration
Penetration testing in the future is likely to utilize both automation and artificial intelligence. The testing process will be more automated, allowing constant check-ups of vulnerable areas. Artificial intelligence-based solutions will collect and parse large data sets to look for risks and omissions, improving organizational protection against attackers.
Continuous Testing
It took some time to realize that frequent penetration tests are no longer possible; we cannot talk about annual or even bi-annual tests. The future will require constant assessment as part of an organization’s security plan. This is where continuous testing comes into the arena. The advantage of this approach is that the vulnerabilities can be ascertained in real time; hence, mitigations scale up with the threats. This will make the testing a continuous process for the DevSecOps fold, with the primary goal of ensuring security incorporation in the development cycle.
Focus on Cloud Security
As organizations move their applications and operations to the cloud, penetration testing will have to evolve to cover new threats in the cloud. In the future, penetration tests will be performed to evaluate cloud security configurations, APIs, and third-party platforms.
Emphasis on Human Factors
Despite this, human factors are expected to continue being a central focus despite the vital role that technology now has to play in penetration testing. Phishing and other social engineering attempts will be carried out more frequently to check current employees’ sensitivity to and ability to recognize various tricks. On this basis, training programs shall be advanced through these tests to self-encourage organizations’ security.
Combination of Red Teams and Blue Teams
The future of penetration testing will encourage more circles between red teams (attackers) and blue teams (defenders). The proposed synergy will strengthen the security status by enabling defenders to apply specifics of the simulated attack and refine the composition approach. Thus, one firm’s collaboration with another can enhance the generation of efficient courses on security training and improve the overall understanding of threat environments.
Real-World Examples of Penetration Testing Success
There are some real-world examples of penetration testing. In some examples, we talked about how pen testing could strengthen their security posture and, in some cases, how it saved organizations millions of dollars before attacks could exploit them. Let’s understand these real-world examples one by one:
Solar Winds Corporation
In 2020, Solar Winds Corporation, the software provider for several organizations, was hacked in a supply chain attack. The adversaries successfully penetrated the software development lifecycle, inserting the Sunspot backboard Trojan into Solar Winds Orion software updates released to clients.
The Solar Winds attack emphasized the effectiveness of pen testing on your networks and any third-party systems your organization may use. Unfortunately, SolarWinds did not detect the malware before sending it to its customers and clients, leading to havoc and unsatisfactory services.
The Target Data Breach
Target Corporation, an extremely popular retail chain, was hacked in 2013. Due to a weakness in the firm’s payment card processing system, the leak exposed millions of customers’ data, including the financial details of forty million clients.
Following the breach, Target conducted a penetration test on its system. This undertaking exposed multiple risks, such as the server’s insecurity and the password’s easy guessability. Target focused on these issues, minimizing them and enhancing its business security.
If Target had done a penetration test to prepare for the breach, it would have discovered and remedied these weaknesses. Due to the breach, Target had to spend $18.5 million in compensation.
Exquifax
Credit reporting agency Equifax was the confidential data of 147.9 million customers due to a cyber attack in 2017. The leak arose from a gap in the web application framework, which the hackers exploited to access the firm’s server data.
The Equifax breach reveals that penetration testing must be performed more comprehensively. This claim is valid since the vulnerability assessment conducted before the attack did not determine which sensitivity the hackers leveraged. If the company had undertaken more tests, it may have seen and fixed the vulnerability before the hackers could exploit it.
How BuzzClan Can Help You Mitigate Cybersecurity Risks
BuzzClan offers a wide range of software testing services to enhance performance and security and support scalability for your solutions. With services such as mobile application, security, penetration, and accessibility testing, we provide unparalleled domain expertise and agile-ready testing solutions.
With highly skilled experts, we offer a robust QA testing process by integrating the latest tools and tech stack, offering 24*7 support so that you can be hassle-free. Our several components of QA testing services help organizations in pre-project planning, project lifecycle management, quality control, and others with cutting-edge AI-powered testing technology.
Conclusion
To summarize, pen tests have been a significant part of modern cybersecurity practices. They effectively help individuals and organizations simulate real-life attacks, eventually enhancing their security posture. Businesses must adopt pen tests to safeguard themselves and the sensitive information of customers, clients, and partners.
Before conducting penetration testing, understand what it is, how it works, its pros and cons, best practices, and types for a smoother cyber defense journey. One must choose a cyber security service provider with ample experience and skilled professionals. Contact us for serene, extensive, and practical assistance in various cybersecurity services, such as cybersecurity assessments, penetration testing, IoT security, and many others.
FAQs

Get In Touch