Understanding the OWASP Top 10: A Comprehensive Guide for Security Professionals
Devesh Rawat
Aug 8, 2024
Introduction
The Open Web Application Security Project (OWASP) is a non-profit organization dedicated to improving the security of web applications. One of their most significant contributions is the OWASP Top 10, a regularly updated list of web applications’ most critical security risks. This list is an essential guide for developers, security professionals, and organizations to prioritize their security efforts and protect against the most prevalent threats.
The OWASP Top 10 has evolved over the years, reflecting the changing landscape of web application security. As new technologies emerge and attackers find novel ways to exploit vulnerabilities, the list adapts to highlight the most pressing risks. Organizations can proactively address these risks by staying informed about the OWASP Top 10 and strengthening their security posture.
Unveiling the OWASP Top 10 List
The OWASP Top 10 is a standard awareness document representing a broad consensus about web applications’ most critical security risks. The list is based on data from various security organizations and industry surveys, reflecting the real-world experiences of security professionals and the frequency and severity of vulnerabilities discovered in web applications.
To be included in the OWASP Top 10, a vulnerability must meet specific criteria, such as being widespread, having a high impact, and being exploitable. The list is reviewed and updated every few years to ensure it remains relevant and reflects the current state of web application security.
The Current State of Web Application Security
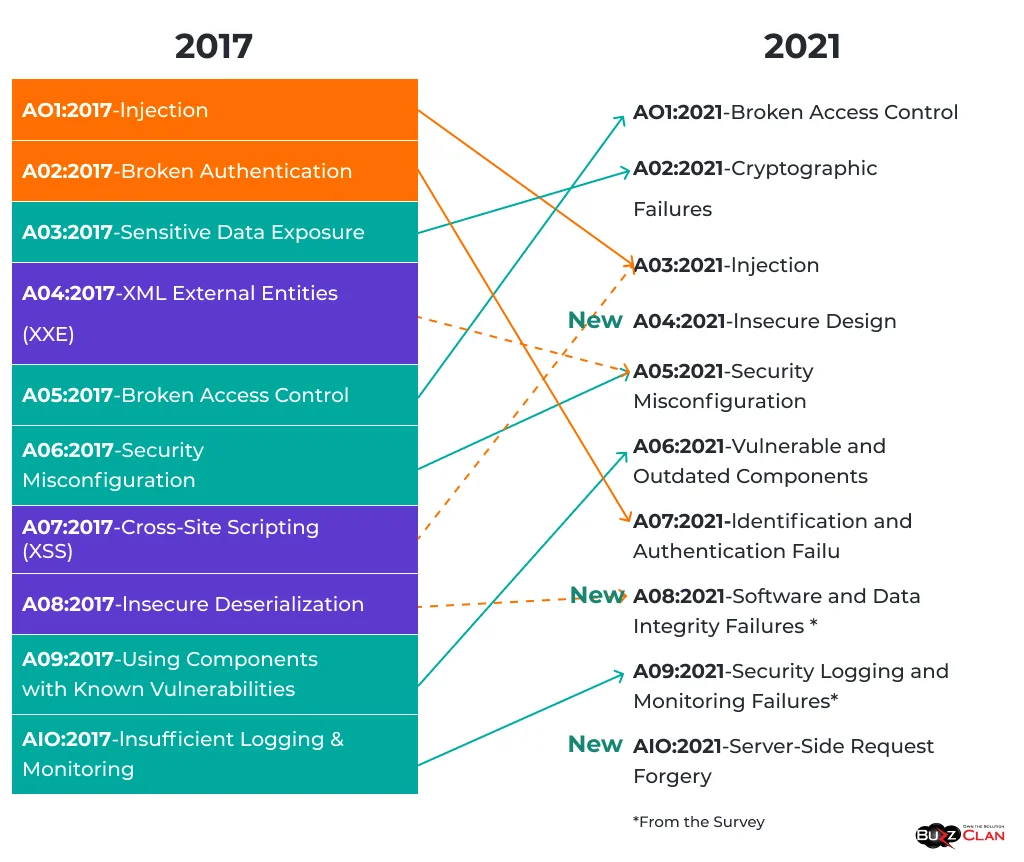
The Open Web Application Security Project (OWASP) Top 10 list is a widely recognized compilation of the most critical security risks. It is updated regularly to reflect the evolving threat landscape, and the latest list contains the following vulnerabilities:
| Vulnerabilities | Description |
|---|---|
| Broken Access Control | It occurs when an attacker gains unauthorized access to resources that should be restricted. Misconfigurations, insecure coding practices, or weaknesses in authentication and authorization mechanisms can cause this. |
| Cryptographic Failures | It result from the improper use or implementation of cryptographic algorithms, protocols, or libraries. These failures can lead to the disclosure of sensitive information, such as passwords or credit card numbers, or the ability to impersonate other users. |
| Injection | Injection occurs when an attacker inserts malicious code into an application through a web form or database query. This can allow the attacker to gain control of the application or access sensitive data. |
| Insecure Design | Insecure Design refers to architectural flaws in an application that make it vulnerable to attack. Examples include using insecure protocols, unencrypted data storage, or a need for input validation. |
| Security Misconfiguration | This occurs when an application is not properly configured, leaving it vulnerable to attack. This can include insecure default settings, outdated software, or misconfigured security controls. |
| Vulnerable and Outdated Components | An application uses components with known vulnerabilities or are no longer supported. Attackers can exploit known vulnerabilities in these components to make the application vulnerable to attack. |
| Identification and Authentication Failures | This result from weak or ineffective identification and authentication mechanisms. This can allow attackers to impersonate legitimate users or access accounts without authorization. |
| Software and Data Integrity Failures | This occur when the integrity of software or data is compromised. Malicious attacks, accidental damage, or natural disasters can cause this. |
| Security Logging and Monitoring Failures | It result from inadequate logging and monitoring of security events. This can make it difficult to detect and respond to security incidents promptly. |
| Server-Side Request Forgery (SSRF) | It occurs when an attacker tricks a server-side application into requesting an arbitrary URL. This can attack internal resources, such as databases or other applications, that are not normally accessible from the Internet. |
Understanding and mitigating the risks associated with these vulnerabilities is essential for securing web applications. Organizations should implement a comprehensive security program that includes regular security assessments, secure coding practices, and effective logging and monitoring.
The latest top 10 list has seen some notable changes compared to the previous iteration. “Insecure Design” and “Software and Data Integrity Failures” are new additions, highlighting the importance of secure design principles and ensuring the integrity of software updates and critical data. The consolidation of “XML External Entities (XXE)” and “Insecure Deserialization” into “Security Misconfiguration” reflects the evolving nature of these vulnerabilities.
Deep Dive into the Top Vulnerabilities
Look closely at some of the most significant vulnerabilities from the OWASP Top 10 list.
Injection Flaws: From SQL to NoSQL
Injection flaws, such as SQL and NoSQL injection, occur when untrusted data is sent to an interpreter as part of a command or query. Attackers can exploit these flaws to execute unintended commands, access sensitive data, or modify data in the database.
Example: A web application that doesn’t properly sanitize user input in a search form could allow an attacker to inject malicious SQL statements, potentially revealing sensitive information or manipulating data.
Prevention strategies include using parameterized queries, validating and sanitizing user input, and implementing least privilege access controls.
Broken Authentication: Risks and Defense
Broken authentication vulnerabilities allow attackers to compromise passwords, keys, or session tokens or to exploit implementation flaws to assume user identities. This can lead to unauthorized access, data breaches, and identity theft.
Example: A web application that uses weak or default passwords, exposes session IDs in URLs, or doesn’t properly invalidate sessions upon logout can be vulnerable to broken authentication attacks.
To secure authentication processes, implement strong password policies, use multi-factor authentication, securely manage session IDs, and follow secure coding practices for authentication and session management.
Sensitive Data Exposure and Protection
Sensitive data exposure occurs when web applications don’t adequately protect sensitive information, such as financial data, healthcare records, or personally identifiable information (PII). Attackers can exploit these vulnerabilities to access and steal sensitive data.
Example: A web application that stores unencrypted credit card numbers or transmits sensitive data over unencrypted channels (e.g., HTTP) can be vulnerable to sensitive data exposure.
Best practices for data protection include encrypting sensitive data at rest and in transit, using strong encryption algorithms and key management, and implementing access controls and monitoring to detect and respond to potential breaches.
Implementation of OWASP Top 10 in Security Protocols
To effectively address the OWASP Top 10 vulnerabilities, organizations should integrate these risks into their security protocols and develop a security-aware culture in software development. This involves:
| Sr.No | Secure Development Practice |
|---|---|
| 1 | Establishing secure coding guidelines and standards based on the OWASP Top 10. |
| 2 | Conducting regular security training for developers, QA, and security teams. |
| 3 | Implementing secure development lifecycle (SDLC) practices, such as threat modeling, secure code reviews, and penetration testing. |
| 4 | Utilizing automated security testing tools to identify and remediate vulnerabilities early in development. |
| 5 | Monitoring and updating web applications and components to address newly discovered vulnerabilities. |
Organizations can proactively identify and mitigate risks by making the OWASP Top 10 an integral part of their security protocols, reducing the likelihood of successful attacks and data breaches.
Security Tools and Resources for OWASP Top 10
Various tools and resources are available to help organizations address the OWASP Top 10 vulnerabilities. These include:
- OWASP ZAP (Zed Attack Proxy) is an open-source web application security scanner that can help identify vulnerabilities in web applications.
- Burp Suite is a comprehensive web application security testing platform with tools for scanning, intercepting, and manipulating HTTP/S traffic.
- Acunetix: A web vulnerability scanner that detects and reports OWASP’s Top 10 vulnerabilities.
- OWASP Dependency-Check: A tool that identifies project dependencies and checks for known vulnerabilities.
- OWASP Web Security Testing Guide: This comprehensive guide for testing web application security covers the OWASP Top 10 and more.
These tools can be used with manual testing techniques, such as code reviews and penetration testing, to provide a comprehensive approach to identifying and addressing vulnerabilities.
The Role of Penetration Testing
Penetration testing, or pen-testing, is crucial to a comprehensive web application security strategy. In the OWASP Top 10 context, pen-testing involves simulating real-world attacks to identify vulnerabilities and assess the effectiveness of an organization’s security controls.
Regular pen testing can help uncover potential security risks before attackers exploit them. By engaging skilled pen-testers to test web applications against the OWASP Top 10, organizations can gain valuable insights into their security posture and prioritize remediation efforts based on the severity and potential impact of discovered vulnerabilities.
Automation in Security: Static and Dynamic Analysis
Automated security testing tools have become essential in detecting and mitigating OWASP Top 10 risks in web applications. These tools streamline the testing process, save time and resources, and comprehensively analyze the application’s security posture. Two primary approaches to automated security testing are Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST).
Static Application Security Testing (SAST) is a white-box testing method that analyzes the application’s source or compiled code without executing it. SAST tools scan the codebase to identify potential vulnerabilities, such as injection flaws, cross-site scripting (XSS), insecure configurations, and weak cryptography. By examining the code structure, data flows, and control flows, SAST tools can pinpoint the exact location of vulnerabilities and provide developers with actionable insights to remediate them.
SAST tools offer several advantages
- Early Detection: SAST can be integrated into the development process, allowing vulnerabilities to be identified and fixed early in the software development lifecycle (SDLC). This reduces the cost and effort required to address security issues later in development.
- Comprehensive Coverage: SAST tools can analyze the entire codebase, including rarely executed code paths, ensuring a thorough assessment of the application’s security.
- Language-Specific Analysis: SAST tools are often language-specific, providing more accurate and relevant results by understanding the intricacies of the programming language used.
However, SAST tools also have some limitations
- False Positives: SAST tools may generate false positives, flagging issues that are not vulnerabilities. This can lead to unnecessary effort in investigating and resolving these issues.
- Lack of Runtime Insight: SAST tools analyze code without executing it, so they may miss vulnerabilities that manifest only during runtime, such as authentication and authorization issues.
On the other hand, dynamic Application Security Testing (DAST) is a black-box testing method that interacts with the web application during runtime. DAST tools simulate attacks against the application, mimicking the behavior of a malicious user. They send malformed inputs, manipulate URLs and parameters, and analyze the application’s responses to identify vulnerabilities that may not be detectable through static analysis alone.
DAST tools offer the following benefits
- Runtime Insight: DAST tools can identify vulnerabilities that only manifest during runtime, such as authentication bypasses, session management issues, and access control flaws.
- Technology-Agnostic: DAST tools interact with the application through its exposed interfaces, making them independent of the underlying technology stack. This allows for testing of applications built with different programming languages and frameworks.
- Realistic Attack Simulation: DAST tools simulate real-world attacks, providing a more accurate assessment of the application’s security posture from an attacker’s perspective.
However, DAST tools have some drawbacks
- Limited Code Coverage: DAST tools can only test the application’s exposed functionality and may miss vulnerabilities in unexposed or rarely accessed code paths.
- False Negatives: DAST tools may fail to identify some vulnerabilities if the application’s responses do not indicate the presence of a security flaw.
Organizations should incorporate SAST and DAST into their development to achieve a comprehensive and effective security testing strategy. Organizations can identify and address a wider range of vulnerabilities early in the SDLC by combining static and dynamic analysis. This proactive approach reduces the risk of successful attacks, minimizes the cost of remediation, and enhances the overall security posture of the web application.
Furthermore, integrating SAST and DAST into the continuous integration and deployment (CI/CD) pipeline allows for automated and continuous security testing. Each code change can be automatically scanned for vulnerabilities, and the results can be fed back to the development team for prompt remediation. This integration ensures that security testing becomes an integral part of the development process rather than an afterthought.
Training and Awareness: Building the First Line of Defense
Training and awareness are essential to a strong web application security strategy. Developers, QA professionals, and security teams should receive regular training on the OWASP Top 10 and secure coding practices. This helps create a security-aware culture and ensures that everyone involved in the development process understands their role in preventing vulnerabilities.
Resources available for OWASP Top 10 training and certification include
- OWASP Top 10 Project: This website provides a wealth of information, including the Top 10 list, risk descriptions, and prevention strategies.
- OWASP AppSec Conference: An annual conference offering training sessions and web application security workshops, including the OWASP Top 10.
- OWASP Secure Coding Practices is a comprehensive guide that provides developers with practical guidance on avoiding common vulnerabilities.
- Certified Secure Software Lifecycle Professional (CSSLP): A certification offered by (ISC)² that covers secure software development practices, including the OWASP Top 10.
By investing in training and awareness, organizations can build a strong first line of defense against web application vulnerabilities, reducing the risk of successful attacks and data breaches.
Preparing for the Future: Anticipating the Next OWASP Top 10
As web technologies evolve and attackers find new ways to exploit vulnerabilities, the OWASP Top 10 will change and adapt. To stay ahead of emerging threats, organizations should proactively monitor the web application security landscape and anticipate potential changes to the OWASP Top 10.
This involves:
- Keeping up with the latest web application security research and trends.
- Participating in the OWASP community and contributing to developing new security standards and best practices.
- Regularly assess web applications against OWASP Top 10 and other relevant security standards.
- Implementing a continuous improvement process for web application security, including regular testing, monitoring, and updating security controls.
By taking a proactive approach to web application security and staying informed about emerging threats, organizations can better prepare for the next iteration of the OWASP Top 10 and maintain a strong security posture over time.
Conclusion
The OWASP Top 10 is a critical resource for organizations seeking to protect their web applications from the most prevalent and severe security risks. Organizations can significantly reduce the risk of successful attacks and data breaches by understanding the current Top 10 vulnerabilities, implementing secure coding practices, utilizing security tools and resources, and investing in training and awareness.
However, web application security is an ongoing process that requires continuous vigilance and improvement. As the threat landscape evolves, organizations must remain proactive in their approach to security, anticipating emerging risks and adapting their defenses accordingly.
By making the OWASP Top 10 an integral part of their security strategy and fostering a security-aware culture, organizations can build more secure web applications, protect sensitive data, and maintain the trust of their users. Ultimately, prioritizing web application security is not just a matter of compliance but a critical component of business success in the digital age.
FAQs

Get In Touch
Follow Us

Get In Touch
Follow Us
Table of Contents
- Introduction
- Unveiling the OWASP Top 10 List
- The Current State of Web Application Security
- Deep Dive into the Top Vulnerabilities
- Security Tools and Resources for OWASP Top 10
- Training and Awareness: Building the First Line of Defense
- Preparing for the Future: Anticipating the Next OWASP Top 10
- Conclusion
- FAQs