HIPAA Compliance: The Ultimate Guide for Protecting Patient Information
Yarun Ghawana
Jul 24, 2024
Introduction
In today’s digital age, the protection of patient information has become a critical concern in the healthcare industry. As medical records transition from paper to electronic formats and data breaches become increasingly sophisticated, the need for robust safeguards to protect sensitive health information has never been more pressing. This is where the Health Insurance Portability and Accountability Act, commonly known as HIPAA, comes into play.
This comprehensive guide will delve deep into the world of HIPAA compliance, providing healthcare professionals, administrators, and related entities with a thorough understanding of its requirements, implications, and best practices. From the basics of what HIPAA entails to the intricacies of its privacy and security rules, we’ll cover everything you need to know to ensure your organization remains compliant and protects patient information effectively.
Throughout this blog, we’ll explore the key components of HIPAA, including its privacy and security rules, common violations and their consequences, training requirements, and implementation strategies. We’ll also examine how HIPAA applies in different contexts and discuss future trends that will likely shape compliance efforts in the coming years.
Whether you’re new to HIPAA or looking to enhance your compliance program, this guide will be invaluable in navigating the complex landscape of healthcare information protection.
What is HIPAA?
The Health Insurance Portability and Accountability Act, or HIPAA, is a federal law enacted in 1996 to provide data privacy and security provisions for safeguarding medical information. It was designed to improve the efficiency and effectiveness of the healthcare system by establishing standards for electronic healthcare transactions while protecting the privacy and security of patient health information.
HIPAA is more than just a set of rules; it’s a comprehensive framework that governs how healthcare providers, insurers, and their business associates handle protected health information (PHI). The act aims to strike a balance between allowing the flow of health information needed to provide and promote high-quality health care and protecting the privacy of individuals who seek care.
The acronym HIPAA stands for:
H – Health
I – Insurance
P – Portability
A – and
A – Accountability
HIPAA was enacted on August 21, 1996, by President Bill Clinton. The act was created in response to several concerns:
- The need for health insurance reform: HIPAA was designed to make health insurance more portable when people changed jobs.
- The increasing use of electronic transactions in healthcare: As healthcare providers began transitioning from paper to electronic records, standardized formats for health data became necessary.
- Growing concerns about the privacy and security of health information: With the rise of electronic health records, there was an increased risk of unauthorized access to sensitive health information.
Since its enactment, HIPAA has undergone several modifications and additions, including the Privacy Rule in 2003, the Security Rule in 2005, and the HITECH Act in 2009, strengthening its privacy and security protections.
HIPAA Compliance
HIPAA compliance refers to the adherence to the regulations outlined in the Health Insurance Portability and Accountability Act. It involves implementing safeguards to protect the confidentiality, integrity, and availability of protected health information (PHI).
A basic HIPAA compliance checklist includes:
- Conduct a risk analysis
- Implement security measures
- Develop and implement policies and procedures
- Train employees on HIPAA requirements
- Establish business associate agreements
- Document compliance efforts
- Regularly review and update compliance measures
Maintaining HIPAA compliance is crucial for healthcare organizations for several reasons:
- Legal Obligation: HIPAA is a federal law, and non-compliance can result in severe penalties and fines.
- Patient Trust: Compliance demonstrates a commitment to protecting patient privacy, essential for maintaining trust in the healthcare system.
- Data Security: HIPAA compliance helps protect sensitive health information from data breaches and unauthorized access.
- Operational Efficiency: Standardized processes for handling health information can improve operational efficiency.
- Risk Management: Compliance measures help mitigate the risk of data breaches and associated costs.
HIPAA Privacy Rule
The HIPAA Privacy Rule, also known as Standards for Privacy of Individually Identifiable Health Information, establishes national standards for protecting individuals’ medical records and other personal health information. It applies to health plans, healthcare clearinghouses, and providers conducting certain healthcare transactions electronically.
Key aspects of the Privacy Rule include:
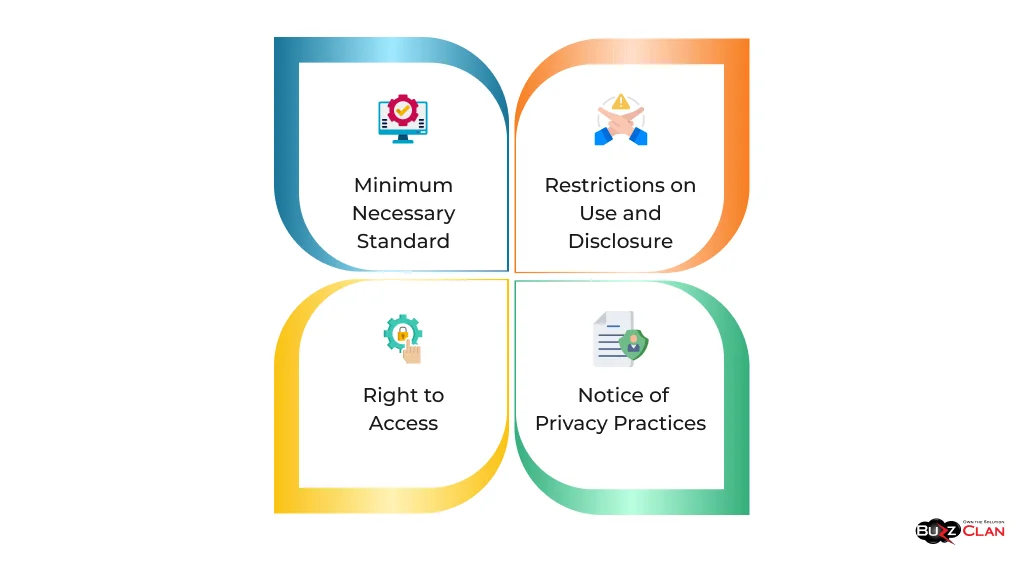
- Right to Access: Patients can access their health information and request corrections.
- Restrictions on Use and Disclosure: The rule limits how health information can be used and disclosed without patient authorization.
- Notice of Privacy Practices: Covered entities must notify patients of their privacy practices.
- Minimum Necessary Standard: When using or disclosing PHI, covered entities must make reasonable efforts to use, disclose, and request only the minimum amount of PHI needed to accomplish the intended purpose.
Protected Health Information (PHI) refers to individually identifiable health information that is transmitted or maintained in any form or medium by a covered entity or its business associate. This includes:
- Information about physical or mental health conditions
- Healthcare services provided to an individual
- Payment for healthcare services
The minimum necessary standard is a key principle of the HIPAA Privacy Rule. It requires covered entities to limit PHI’s use, disclosure, and requests to the minimum necessary to accomplish the intended purpose. This standard helps protect privacy while allowing the necessary flow of health information for treatment, payment, and healthcare operations.
HIPAA Security Rule
The HIPAA Security Rule complements the Privacy Rule by setting national standards for protecting electronic PHI (ePHI). It requires appropriate administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of ePHI.
Key components of the Security Rule include:
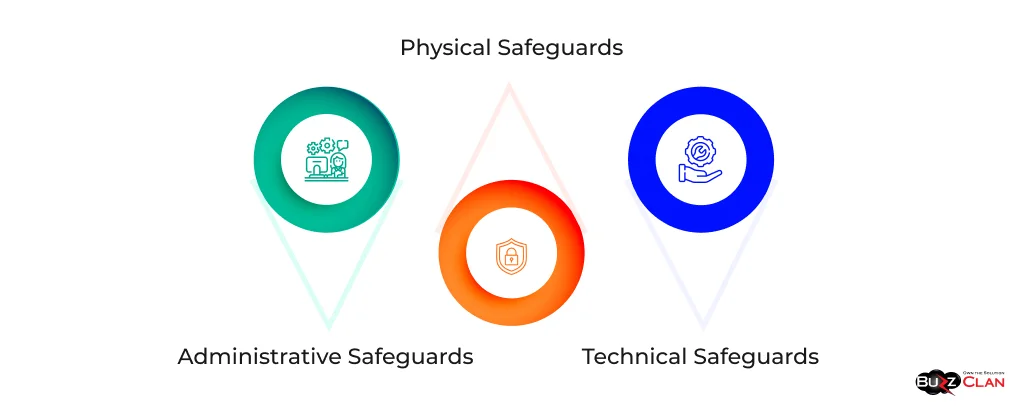
- Administrative Safeguards: Policies and procedures designed to clearly show how the entity will comply with HIPAA.
- Physical Safeguards: Physical measures, policies, and procedures to protect electronic information systems and related buildings and equipment from natural and environmental hazards and unauthorized intrusion.
- Technical Safeguards: Technology and the policies and procedures for its use that protect ePHI and control access to it.
The Security Rule applies to:
- Covered Entities: include health plans, healthcare clearinghouses, and healthcare providers who transmit health information electronically.
- Business Associates: Persons or entities that perform certain functions or activities involving the use or disclosure of PHI on behalf of, or provide services to, a covered entity.
Covered entities and business associates must implement appropriate safeguards to protect the confidentiality, integrity, and availability of ePHI. This includes conducting regular risk assessments, implementing access controls, using encryption, and maintaining audit trails.
HIPAA Violations and Penalties
HIPAA violations occur when covered entities or business associates fail to comply with HIPAA rules. Common violations include:
- Unauthorized access to PHI
- Improper disposal of PHI
- Lack of patient access to their PHI
- Failure to conduct a risk analysis
- Lack of business associate agreements
- Failure to implement appropriate safeguards
HIPAA violations can result in significant penalties and fines. The penalties are tiered based on the level of culpability:
| Tier | Violation Range | Annual Cap |
|---|---|---|
| Tier 1 (No Knowledge) | $100-$50,000 per violation | Up to $1.5 million per year |
| Tier 2 (Reasonable Cause) | $1,000-$50,000 per violation | Up to $1.5 million per year |
| Tier 3 (Willful Neglect - Corrected) | $10,000-$50,000 per violation | Up to $1.5 million per year |
| Tier 4 (Willful Neglect - Not Corrected) | $50,000 per violation | Up to $1.5 million per year |
In addition to monetary penalties, HIPAA violations can result in criminal charges in severe cases.
Reporting HIPAA violations is crucial for maintaining the integrity of the healthcare system. Individuals who believe their health information privacy rights have been violated can file a complaint with the Office for Civil Rights (OCR). Covered entities and business associates must report breaches of unsecured PHI to the OCR and affected individuals.
HIPAA Certification and Training
While the Department of Health and Human Services does not recognize an official HIPAA certification, many organizations offer HIPAA certification programs. These programs can be valuable for healthcare professionals and organizations to demonstrate their knowledge and commitment to HIPAA compliance.
HIPAA training is crucial for ensuring all employees understand their responsibilities under HIPAA.
Key aspects of HIPAA training include:
- Overview of HIPAA regulations
- Understanding PHI and ePHI
- Privacy and security best practices
- Recognizing and reporting HIPAA violations
- Patient rights under HIPAA
HIPAA authorization and consent forms are essential documents in HIPAA compliance. A HIPAA authorization form is a document that allows an individual to give their permission for a covered entity to use or disclose their PHI for specified purposes, which are generally other than treatment, payment, or health care operations, or as otherwise permitted by the Privacy Rule.
Implementing HIPAA Compliance
Implementing HIPAA compliance involves several key steps:
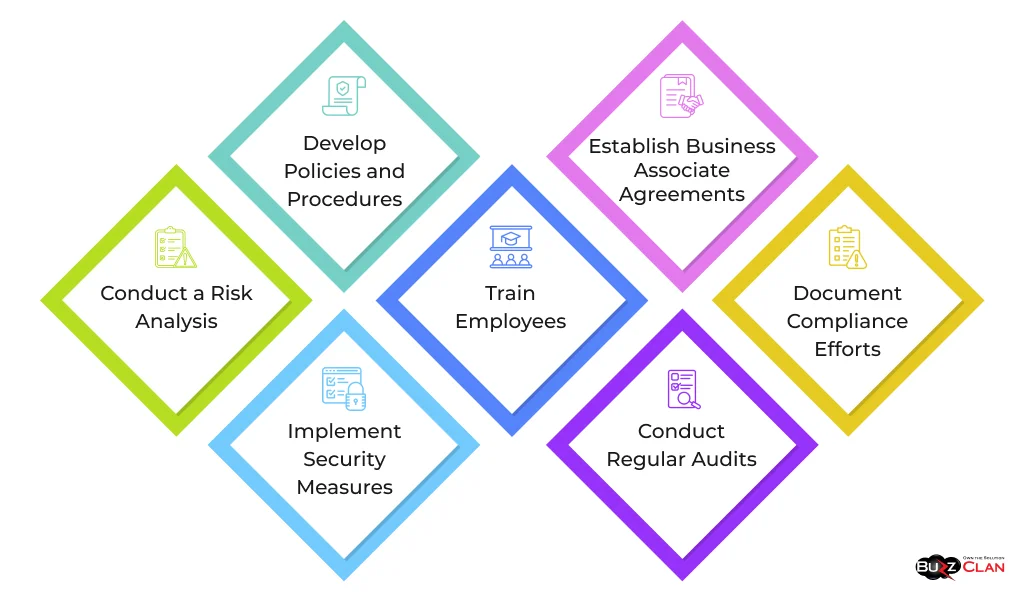
- Conduct a Risk Analysis: Identify potential risks and vulnerabilities to PHI.
- Develop Policies and Procedures: Create comprehensive policies that address all aspects of HIPAA compliance.
- Implement Security Measures: Put administrative, physical, and technical safeguards in place to protect PHI.
- Train Employees: Provide regular HIPAA training to all employees who handle PHI.
- Establish Business Associate Agreements: Ensure all business associates know their HIPAA obligations.
- Conduct Regular Audits: Perform internal audits to ensure ongoing compliance.
- Document Compliance Efforts: Maintain thorough documentation of all compliance activities.
Internal audits and assessments are crucial for maintaining HIPAA compliance. They help organizations identify potential vulnerabilities, ensure policies and procedures are being followed, and demonstrate a commitment to compliance.
Proper documentation and record-keeping are essential aspects of HIPAA compliance. Organizations should maintain detailed records of their compliance efforts, including policies and procedures, risk assessments, training records, and audit results.
Employee training and awareness play a critical role in HIPAA compliance. All employees who handle PHI should receive regular training on HIPAA regulations, privacy and security best practices, and their specific responsibilities in maintaining compliance.
Technology solutions can significantly aid in maintaining HIPAA compliance. These may include:
- Encryption software for protecting ePHI
- Access control systems to manage who can view and modify PHI
- Audit trail and integrity controls to track access to PHI
- Secure communication platforms for sharing PHI
HIPAA in Different Contexts
HIPAA’s impact extends beyond just healthcare providers and insurers. It also affects research activities, government programs like Medicare and Medicaid, and other industries that handle health information.
In research, HIPAA includes activities related to the creation, use, or disclosure of PHI for research purposes in its definition. Researchers must obtain authorization from individuals to use their PHI unless an Institutional Review Board (IRB) or Privacy Board has approved an authorization waiver.
HIPAA plays a crucial role in Medicare and Medicaid programs. The Centers for Medicare & Medicaid Services (CMS) and its Center for Medicare and Medicaid Innovation (CMMI) must comply with HIPAA regulations in handling beneficiary information.
HIPAA’s influence extends to other industries as well. For example, insurance companies that handle health information must comply with HIPAA. Similarly, IT companies that provide services to healthcare organizations may be considered business associates and thus subject to HIPAA regulations.
Future Trends in HIPAA Compliance
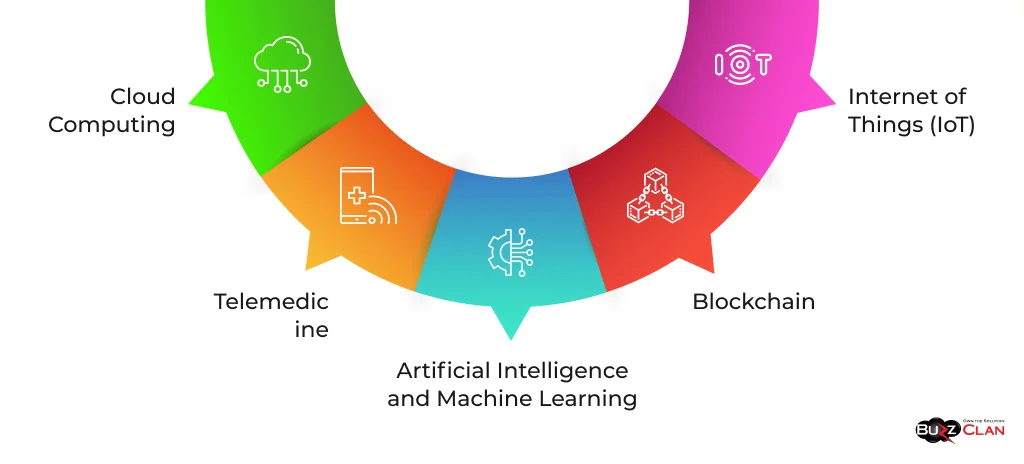
As technology continues to evolve, so does the landscape of HIPAA compliance. Some key trends to watch include:
- Artificial Intelligence and Machine Learning: These technologies are increasingly used to enhance security measures and detect potential HIPAA violations.
- Blockchain: This technology could securely revolutionize storing and sharing health records.
- Telemedicine: The rapid growth of telehealth services presents new challenges for HIPAA compliance.
- Internet of Things (IoT): The increasing use of connected devices in healthcare raises new privacy and security concerns.
- Cloud Computing: As more healthcare organizations move to the cloud, HIPAA compliance in cloud environments becomes crucial.
The globalization of healthcare and increasing international data sharing are also influencing HIPAA compliance efforts. While HIPAA is a U.S. law, many international organizations are adopting similar standards to facilitate data sharing with U.S. entities.
Emerging cybersecurity threats continue to shape HIPAA compliance strategies. As cyber-attacks become more sophisticated, healthcare organizations must continually update their security measures to protect PHI.
Conclusion
HIPAA compliance is a critical aspect of modern healthcare operations. It protects sensitive patient information, promotes trust in the healthcare system, and facilitates the efficient exchange of health information.
Throughout this guide, we’ve explored the key components of HIPAA, including its Privacy and Security Rules, the implications of non-compliance, and implementation strategies. We’ve also examined how HIPAA applies in different contexts and discussed future trends likely to shape compliance efforts.
As the healthcare landscape continues to evolve, with new technologies and increasing digitization, the importance of HIPAA compliance will only grow. Healthcare organizations must stay informed about these changes and adapt compliance strategies to protect patient information effectively.
By prioritizing HIPAA compliance, healthcare organizations meet their legal obligations and demonstrate their commitment to patient privacy and data security. This, in turn, can enhance patient trust, improve operational efficiency, and ultimately contribute to better health outcomes.
Remember, HIPAA compliance is not a one-time achievement but an ongoing process. It requires constant vigilance, regular training, and a commitment to continuous improvement. By embracing this approach, healthcare organizations can confidently navigate the complex health information privacy and security world.
FAQs

Get In Touch
