Mastering Secure Access: A Comprehensive Guide to Authentication and Authorization
Rahul Rao
May 30, 2024
Introduction
Secure access to systems and resources is paramount in today’s digital landscape. With the increasing number of online interactions and data exchanges, it is crucial to understand the mechanisms that protect our digital assets. Authentication and authorization are two fundamental concepts that form the backbone of secure access.
Understanding the differences between authentication and authorization is essential for individuals and organizations. It helps implement robust security measures and enables informed decision-making when granting access to sensitive information. By grasping the nuances of these concepts, we can create a more secure digital environment and safeguard our valuable resources.
This blog post will explore definitions of authentication and authorization, key differences, and real-world applications. We will also discuss common misconceptions, examine authentication and authorization in the context of APIs, and delve into advanced topics such as OAuth. By the end of this post, you will have a comprehensive understanding of these critical security concepts and be better equipped to make informed decisions regarding secure access.`
Understanding Authentication and Authorization
Authentication and authorization are two distinct but interrelated concepts in secure access. Let’s examine each one more closely.
Authentication
Authentication is the process of verifying the identity of a user or entity. It answers the question, “Who are you?” When a user attempts to access a system or resource, authentication mechanisms ensure the user is who they claim to be.
There are various methods of authentication, including:
- Passwords: Users provide a secret password to prove their identity.
- Biometrics: Physical characteristics such as fingerprints or facial recognition authenticate users.
- Two-Factor Authentication (2FA): Users must provide additional information, such as a one-time password (OTP) sent to their mobile device, in addition to their password.
Authorization
Authorization, conversely, is the process of granting or denying access to specific resources based on the authenticated user’s privileges. It answers the question, “What are you allowed to do?” Once a user’s identity is verified through authentication, authorization determines what actions they can perform and what resources they can access.
Authorization methods include:
- Permissions: Users are granted specific permissions to perform certain actions, such as reading, writing, or executing files.
- Roles: Users are assigned roles, such as admin or guest, which determine their level of access to different resources.
- Policies: Access control policies define the conditions under which users are granted or denied access to resources.
It’s important to note that authorization is a step that occurs after successful authentication. Authentication verifies the user’s identity, while authorization determines what they can do based on their authenticated identity.
Key Differences
To better understand the distinctions between authentication and authorization, let’s compare them side by side:
| Aspect | Authentication | Authorization |
| Purpose | Verifies user identity | Grants or denies access to resources |
| Process | Checks credentials (e.g., password) | Checks permissions or roles |
| Timing | Occurs before authorization | Occurs after successful authentication |
| Example | Logging into a website | Accessing specific web pages or features |
Real-World Scenarios:
- Authentication: When you log into your email account, you provide your username and password. The email service authenticates your identity by verifying the provided credentials against the stored information.
- Authorization: Once logged into your email account, you can view your inbox, compose new emails, and access settings. However, you may not have permission to view other users’ emails or modify certain account settings. The email service authorizes your actions based on your assigned permissions.
Deep Dive
Let’s explore the authentication and authorization processes in more detail.
Authentication Processes:
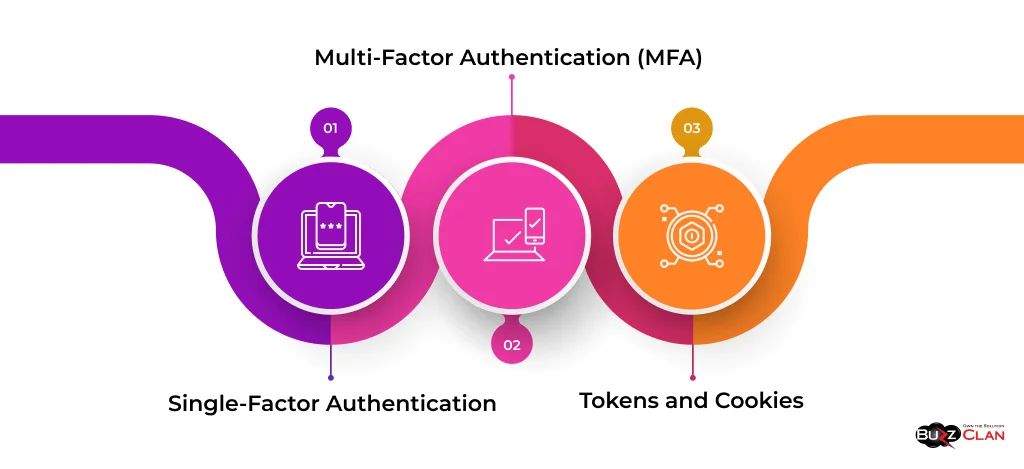
- Single-Factor Authentication: This is the most basic form of authentication, where users provide a single piece of information, typically a password, to verify their identity.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple pieces of evidence to authenticate their identity. This can include a combination of something the user knows (password), something the user has (security token), or something the user is (biometrics).
- Tokens and Cookies: Authentication tokens and cookies are used to maintain user sessions after successful authentication. Tokens are typically generated by the server and sent to the client, while cookies are stored on the client-side and sent with each subsequent request to the server.
Authorization Processes:
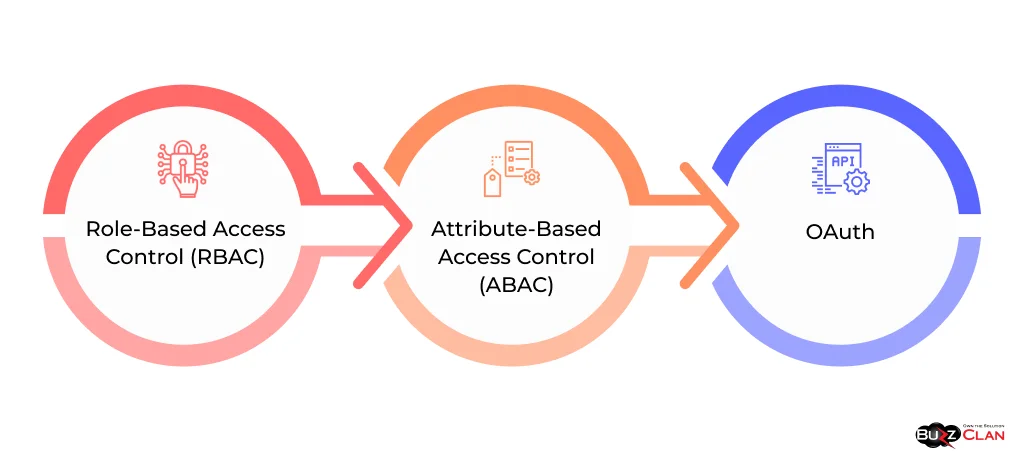
- Role-Based Access Control (RBAC): RBAC is a common authorization model that grants access based on the user’s assigned role. Roles are predefined sets of permissions that determine what actions a user can perform on specific resources.
- Attribute-Based Access Control (ABAC): ABAC is a more granular approach to authorization where access is granted based on attributes associated with the user, resource, and environment. This allows for more dynamic and flexible access control policies.
- OAuth: OAuth is an open standard for authorization that enables users to grant third-party applications limited access to their resources without sharing their credentials. It uses tokens to represent the user’s authorization and allows delegated access control.
Common Misconceptions
There are several common misconceptions surrounding authentication and authorization. Let’s clarify a few of them:
- Misconception: Authentication and authorization are the same thing.
Clarification: Authentication and authorization are distinct concepts. Authentication verifies identity, while authorization determines access rights.
- Misconception: Once authenticated, a user can access all resources.
Clarification: Authorization comes into play after authentication. A user’s access is still restricted based on their assigned permissions or roles.
- Misconception: Two-factor authentication is the same as two-step verification.
Clarification: While often used interchangeably, two-factor authentication requires two different types of factors (e.g., password and fingerprint), whereas two-step verification can involve two steps of the same factor (e.g., password and OTP).
Authentication and Authorization in APIs
API security is crucial in today’s interconnected digital ecosystem. Authentication and authorization are vital in securing APIs and protecting sensitive data.
Best practices for API security include:
- Using strong authentication methods such as API keys, OAuth, or JWT (JSON Web Tokens) to verify the identity of API clients.
- Implement granular authorization controls to limit access to specific API resources based on the client’s permission or scope.
- Encrypting data in transit using secure protocols like HTTPS to prevent unauthorized interception.
- Regularly monitoring and auditing API usage to detect and respond to potential security breaches.
Case Studies:
- In 2018, Facebook experienced a major data breach that affected millions of users due to improper API authorization controls. Third-party applications could access user data without proper consent, highlighting the importance of robust API authorization mechanisms.
- In 2020, a popular online learning platform suffered an API security breach, allowing unauthorized users to access sensitive student data. This incident emphasized the need for strong authentication and authorization measures in APIs handling personal information.
Advanced Topics
- Authentication vs Authorization vs Identification:
Identification is the process of claiming an identity, while authentication verifies that identity. Authorization, as discussed earlier, is granting or denying access to resources based on the authenticated identity.
- OAuth Authentication vs Authorization:
OAuth is an authorization framework that enables users to grant third-party applications access to their resources without sharing their credentials. It separates the authentication process from the authorization process.
In OAuth, authentication is typically handled by the resource owner (user) through their identity provider (e.g., Google, Facebook). After successful authentication, the third-party application (client) receives an access token, which it can use to request authorization to access specific resources on behalf of the user.
The benefits of OAuth include:
- Improved security by eliminating the need for users to share their credentials with third-party applications.
- Granular access control, allowing users to limit the scope and duration of access granted to third-party applications.
- Simplified user experience, as users can use their existing accounts with identity providers to access multiple applications.
Trends and Future
The field of authentication and authorization is constantly evolving, driven by technological advancements and the increasing need for secure access. Some emerging trends and future predictions include:
- Biometric Authentication: Using biometric factors such as fingerprints, facial recognition, and voice recognition for authentication is becoming more prevalent. These methods offer a more secure and convenient alternative to traditional passwords.
- AI-Powered Authentication: Artificial Intelligence (AI) and Machine Learning (ML) techniques are leveraged to enhance authentication processes. AI can analyze user behavior patterns and detect anomalies, providing an additional layer of security.
- Passwordless Authentication: There is a growing trend towards passwordless authentication methods, such as hardware security keys or biometric factors. These methods aim to eliminate the vulnerabilities associated with password-based authentication.
- Continuous Authentication: Instead of relying on a single authentication event, continuous authentication techniques monitor user behavior and context throughout the session. This helps detect and respond to potential security threats in real time.
Conclusion
Authentication and authorization are essential components of secure access in the digital world. Understanding the differences between these concepts is crucial for implementing effective security measures and protecting valuable resources.
Throughout this blog post, we explored the definitions, key differences, and real-world authentication and authorization applications. We delved into various authentication and authorization processes, clarified common misconceptions, and discussed the importance of API security.
As technology advances and new threats emerge, staying informed about the latest trends and best practices in authentication and authorization is crucial. By embracing secure access mechanisms and adopting a proactive approach to security, we can create a more secure digital environment for individuals and organizations.
Remember, authentication verifies identity, while authorization determines access rights. By implementing strong authentication methods and granular authorization controls, we can safeguard our digital assets and maintain the integrity of our systems.
FAQs

Get In Touch