Mastering the Art of Application Architecture: Patterns, Best Practices, and Future Trends
Deepa Desai
Jul 11, 2024
Introduction
In today’s rapidly evolving digital landscape, software application success heavily relies on a well-designed and robust application architecture. It serves as the backbone of any software system, defining how the application will be built, its components will interact, and how it will scale and perform. A well-architected application meets current business requirements and adapts to future changes and challenges.
This comprehensive blog post aims to provide a deep dive into application architecture. We will explore its fundamental concepts, types, patterns, modern approaches, and future trends. Whether you are a software developer, an architect, or a business stakeholder, understanding application architecture principles is crucial for making informed decisions and building successful software solutions.
Throughout this blog, we will cover various aspects of application architecture, including its definition, key components, and the importance of architecture diagrams. We will also delve into specific architectural patterns, such as enterprise patterns and modern web application architectures. Additionally, we will discuss cloud and distributed architectures, application integration strategies, and the critical role of security in application architecture.
By the end of this blog, you will have a solid understanding of application architecture and its practical applications. You will have the knowledge and resources to make informed architectural decisions and design scalable, maintainable applications aligned with business goals. Let’s embark on this journey to unravel the intricacies of application architecture and unlock the potential of well-designed software systems.
What is Application Architecture?
Application architecture refers to the high-level structure and design of a software application. It defines the components, their interactions, and the overall organization of the application. Application architecture is a blueprint that guides the development process and ensures the application meets the desired functional and non-functional requirements.
The primary goal of application architecture is to provide a clear and logical structure for the application, enabling it to be developed, maintained, and scaled effectively. It involves making strategic decisions about the technology stack, separating concerns, and communicating patterns between application components.
Key Components of Application Architecture
Layers and Tiers:
Application architecture is often organized into layers and tiers. Layers represent the logical separation of concerns within the application, while tiers refer to the physical distribution of components.
The common layers in application architecture include:

- Presentation Layer: This layer is responsible for the user interface and interaction. It presents data to the user and handles user input.
- Business Logic Layer: This layer contains the application’s core business rules and logic. It processes data and performs calculations based on business requirements.
- Data Access Layer: This layer interacts with the database or other data storage systems. It handles data retrieval, storage, and manipulation.
3-Tier Architecture:
The 3-tier architecture is a commonly used architectural pattern that separates the application into three distinct tiers:
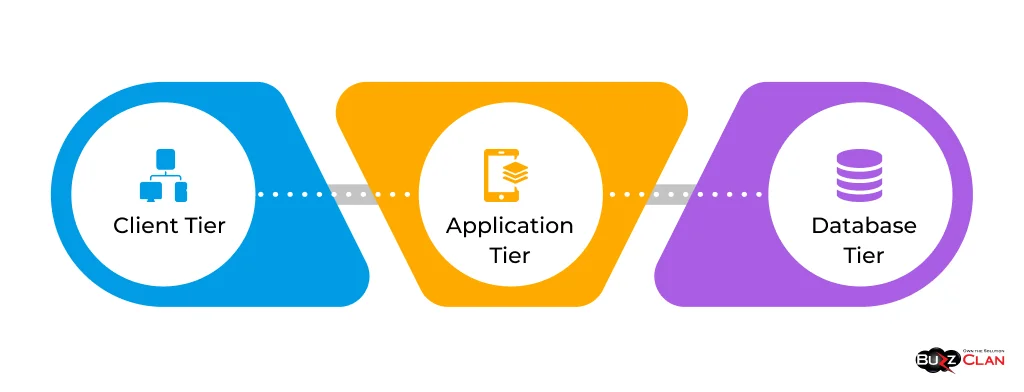
- Client Tier: This tier represents the user interface and runs on the client’s device, such as a web browser or a mobile app.
- Application Tier: This tier contains the business logic and runs on the application server. It processes requests from the client tier and communicates with the database tier.
- Database Tier: This tier is responsible for data storage and retrieval. It typically consists of a database management system (DBMS) running on a separate server.
The 3-tier architecture provides a clear separation of concerns, allowing each tier to be developed, deployed, and scaled independently. It enhances the maintainability, scalability, and flexibility of the application.
Application Architecture Diagrams
Diagrams play a crucial role in visualizing and communicating application architecture. They provide a high-level overview of the system, illustrating the components, their relationships, and the data flow between them. Architecture diagrams help stakeholders understand the application’s structure and behavior, facilitating effective communication and decision-making.
Some common types of application architecture diagrams include:
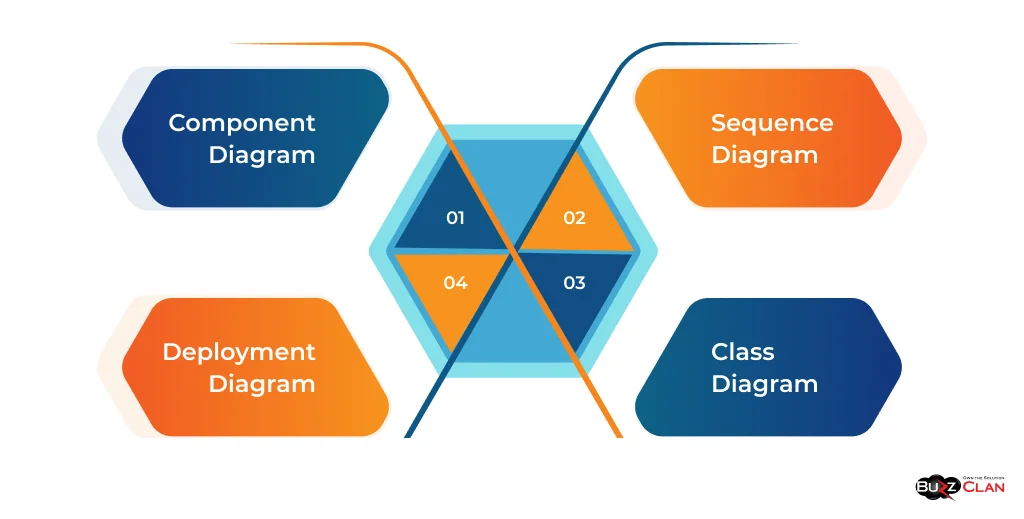
- Component Diagram: It shows the application components and their dependencies.
- Deployment Diagram: It depicts the physical deployment of the application components on hardware infrastructure.
- Sequence Diagram: It illustrates the interaction between components over time, focusing on the sequence of messages exchanged.
- Class Diagram: It represents the static structure of the application, showing the classes, their attributes, and the relationships between them.
Architecture diagrams can be created using various tools and notations, such as UML (Unified Modeling Language), ArchiMate, or informal sketches. The choice of notation depends on the audience and the level of detail required.
Patterns in Application Architecture
Architectural patterns provide proven solutions to common problems in application design. They encapsulate best practices and provide a reusable template for structuring and organizing the application components. Let’s explore some widely used patterns in application architecture.
Enterprise Patterns:
Enterprise application architecture often involves complex business processes, integration with multiple systems, and handling large volumes of data. Some common enterprise patterns include:
- Service-Oriented Architecture (SOA): It organizes the application as a collection of loosely coupled services that can be independently developed, deployed, and composed to form business processes.
- Microservices Architecture: It breaks down the application into small, independently deployable services that communicate with each other through well-defined APIs.
- Event-Driven Architecture (EDA): It focuses on the production, detection, and consumption of events, allowing components to react to system changes in real-time.
Modern Patterns:
With the rise of web and mobile applications, new architectural patterns have emerged to address the specific challenges of these domains. Some modern patterns include:
- Single Page Application (SPA): It provides a fluid and responsive user experience by loading a single HTML page and dynamically updating the content as the user interacts with the application.
- Progressive Web App (PWA): It combines the best of web and mobile apps, offering offline capabilities, push notifications, and a native app-like experience.
- Serverless Architecture: It relies on cloud-based services to handle server-side logic and infrastructure, allowing developers to focus on writing code without worrying about server management.
Web Application Architecture
Web application architecture deals with the design and organization of applications that are accessed through a web browser. It encompasses the client-side (front-end) and server-side (back-end) components and their communication protocols.
Fundamentals:
The fundamental components of web application architecture include:
- Client: The user’s web browser that renders the user interface and handles user interactions.
- Server: The back-end system that processes requests from the client, executes business logic, and interacts with databases or other services.
- Communication Protocols: The protocols used for communication between the client and server, such as HTTP (Hypertext Transfer Protocol) and WebSocket.
Single Page Applications (SPA):
Single-page applications (SPAs) have gained popularity due to their ability to provide a seamless and interactive user experience. In an SPA, the entire application is loaded on a single page, and subsequent interactions are handled through dynamic updates to the page content. SPAs rely heavily on JavaScript frameworks like Angular, React, or Vue.js to handle client-side rendering and communication with the server.
Web Application Firewalls:
Web Application Firewalls (WAFs) play a crucial role in the security architecture of web applications. A WAF sits between the client and the server, analyzing incoming traffic and blocking potential security threats. It helps protect against common web application vulnerabilities, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Cloud and Distributed Architectures
Cloud computing has revolutionized how applications are developed, deployed, and scaled. Cloud platforms offer various services and infrastructure options that enable organizations to build and run applications efficiently.
Cloud Application Architecture:
Cloud application architecture focuses on designing applications that leverage the benefits of cloud computing. Some key principles of cloud application architecture include:
- Scalability: The ability to scale resources up or down based on demand, ensuring optimal performance and cost-efficiency.
- Elasticity: The capability to automatically adapt to changing workloads by provisioning or releasing resources as needed.
- Resilience: Designing applications to be fault-tolerant and recover from failures quickly.
- Loose Coupling: Building applications as a collection of independent services that can be developed, deployed, and scaled separately.
Distributed Systems:
Distributed systems have multiple components running on different machines, working together to achieve a common goal. Distributed application architecture designs and coordinates these components to ensure reliable and efficient operation.
Key considerations in distributed systems include:
- Communication: Defining the protocols and mechanisms for communication between components, such as REST APIs or message queues.
- Consistency: Ensuring data consistency across distributed components, often using techniques like eventual consistency or strong consistency models.
- Fault Tolerance: Building resilience into the system to handle failures of individual components without impacting the overall functionality.
AWS and Cloud Integration:
Amazon Web Services (AWS) is a popular cloud platform that provides a wide range of services for building and running applications. AWS offers various architectural patterns and best practices for designing cloud-native applications.
Some common AWS services used in application architecture include:
- Amazon EC2: Elastic Compute Cloud for running virtual servers.
- Amazon S3: Simple Storage Service for storing and retrieving data.
- Amazon RDS: Relational Database Service for managed database instances.
- AWS Lambda: Serverless compute service running code without provisioning servers.
- Amazon CloudFront: Content Delivery Network (CDN) for distributing content globally.
Integrating applications with AWS and other cloud platforms requires careful consideration of security, scalability, and performance. Architects should follow best practices and leverage cloud-native services to build robust and efficient applications.
Application Integration Architecture
In today’s interconnected business landscape, applications rarely operate in isolation. They often need to exchange data and functionality with other systems within and outside the organization. Application integration architecture focuses on the strategies and techniques for enabling seamless communication and data flow between applications.
Integration Strategies:
There are various strategies for integrating applications, each with its advantages and considerations:
- Point-to-Point Integration: Direct integration between two applications, often using APIs or file-based data exchange.
- Enterprise Service Bus (ESB): A centralized integration platform that acts as a mediator between applications, facilitating communication and data transformation.
- API-led Integration: Exposing application functionality through well-defined APIs, allowing other systems to consume and integrate with the application.
- Event-Driven Integration: Using event-driven architectures to enable real-time data exchange and triggering of actions based on events.
The choice of integration strategy depends on factors such as the number of applications involved, the complexity of data transformations, and the real-time requirements of the integration scenario.
Application Security Architecture
Security is a critical aspect of application architecture. It involves designing and implementing measures to protect the application and its data from unauthorized access, misuse, and attacks. Application security architecture encompasses various techniques and best practices to ensure the application’s confidentiality, integrity, and availability.
Importance of Security:
Securing applications is crucial for several reasons:
- Protecting Sensitive Data: Applications often handle sensitive information, such as personal data, financial records, or intellectual property. Ensuring the confidentiality and integrity of this data is essential.
- Maintaining Trust: Security breaches can erode user trust and damage an organization’s reputation. Implementing robust security measures helps build and maintain user confidence.
- Compliance: Many industries have specific security regulations and standards that applications must adhere to, such as GDPR, HIPAA, or PCI-DSS. Failure to comply can result in legal and financial consequences.
Key aspects of application security architecture include:
- Authentication and Authorization: Implementing mechanisms to verify user identities and control access to application resources based on user roles and permissions.
- Data Encryption: Encrypting sensitive data both in transit and at rest to protect against unauthorized access.
- Secure Communication: Encrypting communication between the client and server using secure protocols, such as HTTPS.
- Input Validation: Validating and sanitizing user input to prevent common vulnerabilities, such as SQL injection or cross-site scripting (XSS) attacks.
- Logging and Monitoring: Implement logging and monitoring mechanisms to detect and respond to security incidents promptly.
Specific Use Cases
Application architecture varies based on specific requirements and constraints for different industries and domains. Let’s explore a few examples:
Industry Examples:
- Financial Services: Applications in the financial sector, such as stock trading platforms or banking systems, require high performance, security, and reliability. They often involve complex business logic, real-time data processing, and integration with external financial systems.
- E-commerce: E-commerce applications must handle high traffic, secure payment processing, and personalized user experiences. They typically involve a multi-tier architecture focusing on scalability, performance, and integration with payment gateways and inventory management systems.
- Healthcare: Healthcare applications, such as electronic health record (EHR) systems or telemedicine platforms, must comply with strict data privacy and security regulations. They often involve complex data models, integration with medical devices, and support for interoperability standards like HL7 or FHIR.
Technology-Specific Examples:
- React Application Architecture: React is a popular JavaScript library for building user interfaces. It often follows a component-based approach, focusing on reusability, performance, and state management using libraries like Redux or MobX.
- .NET Application Architecture: .NET is a Microsoft framework for building enterprise applications. It typically follows a layered approach, with concerns separated between the presentation, business logic, and data access layers. It leverages the rich ecosystem of .NET libraries and tools for building scalable and maintainable applications.
Enterprise Application Architecture
Enterprise application architecture involves designing and organizing large-scale, complex applications that support the entire organization. It also involves integration, scalability, security, and alignment with business goals.
Layers and Integration:
Enterprise application architecture often consists of multiple layers, each responsible for a specific set of concerns:
- Presentation Layer: This layer handles user interaction and presents data to users through various channels, such as web, mobile, or desktop interfaces.
- Business Logic Layer: This layer encapsulates the application’s core business rules, processes, and decision-making logic.
- Data Access Layer: This layer manages interactions with databases and other data storage systems, providing a consistent data retrieval and manipulation interface.
- Integration Layer: Facilitates communication and data exchange between enterprise applications, systems, or services.
These layers work together to deliver a cohesive and integrated enterprise application architecture. The integration layer enables seamless data flow and interoperability between disparate systems.
Tools and Resources
Architects and developers can leverage various tools and resources to support the design and implementation of application architecture. Let’s explore some essential books, reading materials, and online resources.
Books and Reading Materials:
- “Patterns of Enterprise Application Architecture” by Martin Fowler: This book is a classic guide to enterprise application architecture, covering many patterns and best practices for designing and building enterprise applications.
- Robert C. Martin’s “Clean Architecture: A Craftsman’s Guide to Software Structure and Design” presents a practical approach to building maintainable and scalable software systems, emphasizing the importance of clean architecture principles.
- “The Architecture of Open Source Applications” by Amy Brown and Greg Wilson: This book provides insights into the architectural decisions and trade-offs made in real-world open-source applications, offering valuable lessons for architects and developers.
Online Resources:
- Microsoft Application Architecture Guide: Microsoft provides a comprehensive guide to application architecture, covering best practices, patterns, and case studies for building modern applications on the Microsoft platform.
- AWS Architecture Center: Amazon Web Services (AWS) offers a wealth of resources, including reference architectures, best practices, and whitepapers, for designing and deploying applications on the AWS cloud platform.
- Software Engineering Institute (SEI) Architecture Resources: The SEI provides a collection of resources, including articles, tutorials, and webinars, on various aspects of software architecture and its application in practice.
These resources offer valuable insights, practical guidance, and real-world examples to help architects and developers make informed decisions and design effective application architectures.
Future Trends in Application Architecture
As technology evolves and business needs change, application architecture must adapt to keep pace with the latest trends and innovations. Let’s explore some of the future trends shaping the application architecture landscape.
AI and ML Integration:
Artificial Intelligence (AI) and Machine Learning (ML) transform how applications are built and operated. Integrating AI and ML capabilities into application architecture enables intelligent decision-making, personalization, and automation. Applications can leverage AI and ML techniques for tasks such as predictive analytics, natural language processing, and image recognition, enhancing user experiences and business outcomes.
Serverless Architectures:
Serverless architectures are gaining traction as a way to build and deploy applications without managing underlying infrastructure. In a serverless model, the cloud provider dynamically allocates resources and executes code responding to events or requests. This approach enables developers to focus on writing business logic while the cloud provider handles scalability, availability, and infrastructure management. Serverless architectures offer benefits such as reduced operational complexity, cost efficiency, and faster time to market.
Edge Computing:
Edge computing brings computation and data storage closer to the data source rather than relying solely on centralized cloud servers. By processing data at the edge, applications can achieve lower latency, improved performance, and enhanced data privacy. Edge computing architectures are particularly relevant for Internet of Things (IoT) scenarios, where real-time processing and decision-making are critical. As the volume of data generated by edge devices grows, edge computing will play an increasingly important role in application architecture.
These trends highlight the need for application architects to stay agile, embrace new technologies, and design architectures that can adapt to the changing landscape. By incorporating AI and ML capabilities, leveraging serverless architectures, and harnessing the power of edge computing, organizations can build applications that are intelligent, scalable, and responsive to the needs of their users.
Conclusion
Throughout this blog, we have explored the key components of application architecture, including layers, tiers, and the importance of architecture diagrams. We have also delved into specific architectural patterns, such as enterprise patterns and modern web application architectures, highlighting their benefits and considerations.
Cloud and distributed architectures have emerged as powerful paradigms for building scalable and resilient applications. By leveraging cloud platforms like AWS and adopting distributed system principles, organizations can create applications that can handle high traffic volumes and adapt to changing business needs.
Application integration and security are critical aspects of application architecture that cannot be overlooked. Architects must carefully consider the strategies for integrating applications and ensuring the security of sensitive data and user interactions.
We have also explored specific use cases and industry examples, showcasing how application architecture varies based on domains’ unique requirements and constraints. Enterprise application architecture, in particular, requires a holistic approach that considers integration, scalability, and alignment with business goals.
To support the design and implementation of effective application architectures, architects and developers can leverage various tools and resources, including books, online guides, and reference architectures from leading technology providers.
Looking ahead, emerging trends such as AI and ML integration, serverless architectures, and edge computing are shaping the future of application architecture. These trends present opportunities and challenges for architects, requiring them to stay agile, embrace new technologies, and design architectures that adapt to the evolving landscape.
In conclusion, application architecture is a critical discipline that plays a vital role in the success of software applications. By understanding the principles, patterns, and best practices of application architecture, organizations can build applications that are scalable, maintainable, and aligned with business objectives. As technology advances, architects and developers must stay informed, adapt to new trends, and continuously refine their architectural approaches to deliver value to their users and stakeholders.
FAQs

Get In Touch
Follow Us

Get In Touch
Follow Us
Table of Contents
- Introduction
- What is Application Architecture?
- Key Components of Application Architecture
- Application Architecture Diagrams
- Patterns in Application Architecture
- Web Application Architecture
- Cloud and Distributed Architectures
- Application Integration Architecture
- Application Security Architecture
- Specific Use Cases
- Enterprise Application Architecture
- Tools and Resources
- Online Resources:
- Future Trends in Application Architecture
- Conclusion
- FAQs