User and Entity Behavior Analytics: Advanced Implementation Guide for Modern Security Operations
Sunita Singhania
Jul 25, 2025
In the ever-evolving cybersecurity landscape, organizations are constantly seeking innovative solutions to protect their digital assets from increasingly sophisticated threats. User and Entity Behavior Analytics (UEBA) has emerged as a powerful tool in the modern security arsenal, leveraging advanced analytics and machine learning to detect anomalous behaviors that may indicate security compromises. This comprehensive guide delves into the intricacies of UEBA implementation, exploring its architecture, deployment strategies, and operational considerations.
The Evolution of Security Analytics
The cybersecurity paradigm has undergone a significant transformation over the past decade, driven by traditional security approaches’ limitations and threats’ growing complexity. To understand UEBA’s value proposition, it’s crucial to examine conventional security methods’ shortcomings and the challenges they face in today’s threat landscape.
Limitations of Traditional Security
Traditional security approaches have long relied on a set of static methodologies that are increasingly inadequate in the face of modern threats:
- Signature-based detection mechanisms
- Static rule sets and thresholds
- Perimeter-focused security models
- Manual correlation of security events
- Reactive incident response procedures
These conventional methods consistently fail to address several critical areas:
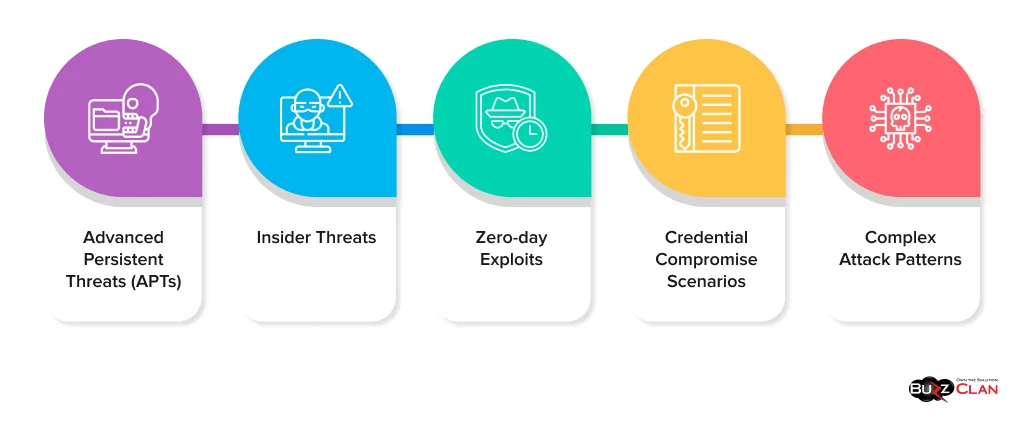
- Advanced Persistent Threats (APTs): Sophisticated, long-term attacks that evade traditional detection methods.
- Insider Threats: Malicious activities originating within the organization often use legitimate credentials.
- Zero-day Exploits: Attacks that leverage previously unknown vulnerabilities for no signatures exist.
- Credential Compromise Scenarios: Situations where attackers gain access to valid user credentials.
- Complex Attack Patterns: Multi-stage attacks span various systems and time frames.
The limitations of these approaches have paved the way for more advanced, behavior-based analytics solutions like UEBA.
UEBA Core Architecture and Components
At its core, UEBA is built on a sophisticated architecture designed to ingest, process, and analyze vast amounts of data from diverse sources. Understanding this architecture is crucial for successfully implementing and operating UEBA systems.
Data Ingestion Layer
The foundation of any UEBA system begins with comprehensive data collection across multiple sources. This layer gathers data from various endpoints and systems within the organization.
Primary Data Sources:
Authentication Systems
- Active Directory logs
- LDAP servers
- Single sign-on platforms
- Multi-factor authentication systems
- Password management tools
Network Infrastructure
- Firewall logs
- Network flow data
- VPN access records
- DNS queries
- DHCP logs
- Proxy server data
Application Layer
- Web application logs
- Database access records
- API gateway logs
- Cloud service audit trails
- SaaS application usage data
Security Tools
- SIEM event data
- EDR/XDR telemetry
- DLP alerts
- IDS/IPS logs
- Email security logs
The diversity and volume of these data sources provide UEBA systems with a comprehensive view of user and entity activities across the organization’s digital ecosystem.
Data Processing Pipeline
Once data is ingested, it must be processed and normalized to ensure consistent analysis. This stage is critical for maintaining data quality and preparing it for advanced analytics.
Data Normalization
UEBA systems implement sophisticated normalization processes to ensure consistent analysis:
Schema Standardization
- Field mapping and normalization
- Data type conversion
- Timestamp normalization
- Entity resolution
- Attribute standardization
Enrichment Processes
- Threat intelligence integration
- Asset context addition
- User role mapping
- Geographic location data
- Business context incorporation
Data Quality Management
- Validation rules enforcement
- Deduplication processes
- Missing data handling
- Anomaly filtering
- Data integrity checks
These processes ensure that data from disparate sources is transformed into a consistent format, enriched with relevant context, and maintained at a high-quality standard for accurate analysis.
Analytics Engine Architecture
The heart of UEBA lies in its analytics engine, which is responsible for creating behavioral baselines and applying advanced analytics to detect anomalies.
Behavioral Baseline Creation:
Individual Profile Development
- Activity pattern analysis
- Resource usage profiling
- Access pattern mapping
- Communication behavior analysis
- Transaction pattern recognition
Group Behavior Modeling
- Peer group identification
- Role-based behavioral analysis
- Department-level baseline creation
- Location-based pattern recognition
- Project team behavior mapping
Advanced Analytics Components:
Statistical Analysis
- Time series analysis
- Frequency distribution
- Correlation analysis
- Pattern recognition
- Trend identification
Machine Learning Models
- Supervised learning classifiers
- Unsupervised anomaly detection
- Deep learning networks
- Reinforcement learning systems
- Ensemble methods
These components establish normal behavior patterns and identify deviations that may indicate security threats.
Implementation Frameworks and Methodologies
Implementing UEBA requires careful consideration of deployment models and integration strategies. Organizations must choose between on-premises and cloud-based deployments, each with its considerations.
Deployment Models
On-premises Implementation:
Infrastructure Requirements
- Processing capacity planning
- Storage architecture design
- Network bandwidth allocation
- High availability configuration
- Disaster recovery planning
Security Controls
- Access control implementation
- Data encryption requirements
- Network segmentation
- Monitoring and logging
- Backup and recovery systems
Cloud-based Deployment:
Cloud Platform Selection
- Service level requirements
- Geographic distribution
- Data sovereignty compliance
- Cost optimization
- Scaling capabilities
Integration Architecture
- API gateway implementation
- Service mesh configuration
- Container orchestration
- Microservices architecture
- Event-driven processing
The choice between on-premises and cloud deployment depends on data sensitivity, regulatory requirements, existing infrastructure, and organizational preferences.
Integration Patterns
Effective UEBA implementation requires seamless integration with existing security tools and enterprise systems.
Security Tool Integration:
SIEM Integration
- Bi-directional data flow
- Alert correlation
- Case management integration
- Workflow automation
- Reporting synchronization
Identity Management
- Directory service integration
- Access management systems
- Privileged account monitoring
- Authentication framework
- Role-based access control
Enterprise System Integration:
Business Applications
- ERP system integration
- CRM data incorporation
- HR system connectivity
- Email system integration
- Document management systems
Cloud Services
- SaaS application monitoring
- Cloud infrastructure visibility
- Container platform integration
- Serverless function monitoring
- API security integration
These integration patterns ensure that UEBA systems can access comprehensive data sources and provide actionable insights into existing security and business processes.
Advanced Analytics Capabilities
The power of UEBA lies in its advanced analytics capabilities, which leverage machine learning and statistical analysis to identify anomalous behaviors.
Machine Learning Implementation
Supervised Learning Models:
Classification Algorithms
- Random Forests for Threat Classification
- Support Vector Machines for access pattern analysis
- Gradient Boosting for Risk Scoring
- Neural Networks for Behavior Classification
- Decision Trees for alert prioritization
Regression Models
- Linear Regression for trend analysis
- Polynomial Regression for pattern prediction
- Time Series Forecasting for behavior prediction
- Logistic Regression for risk assessment
- Multiple Regression for impact analysis
Unsupervised Learning Applications:
Clustering Algorithms
- K-means for peer group identification
- DBSCAN for anomaly detection
- Hierarchical Clustering for behavior grouping
- Gaussian Mixture Models for pattern discovery
- Spectral Clustering for relationship mapping
Dimensionality Reduction
- Principal Component Analysis
- t-SNE for visualization
- Autoencoders for feature extraction
- Factor Analysis for Pattern Identification
- UMAP for behavioral mapping
Deep Learning Architectures:
Neural Network Models
- Recurrent Neural Networks (RNNs)LSTM for sequence analysis
Convolutional Networks
- Pattern recognition
- Feature extraction
- Temporal convolution
- Multi-dimensional analysis
- Transfer learning applications
These advanced analytics capabilities enable UEBA systems to detect subtle anomalies and complex attack patterns that would be impossible to identify with traditional rule-based approaches.
Operational Considerations
Implementing UEBA is not just about technology; it also requires careful consideration of operational aspects to ensure optimal performance and effectiveness.
Performance Optimization
System Performance:
Processing Optimization
- Query optimization
- Caching strategies
- Index management
- Parallel processing
- Resource allocation
Storage Management
- Data retention policies
- Archival strategies
- Storage tiering
- Compression techniques
- Cleanup procedures
Alert Management
Effective alert management is crucial for maximizing the value of UEBA and minimizing alert fatigue.
Alert Prioritization
- Risk-based scoring
- Context-aware prioritization
- Impact assessment
- Urgency evaluation
- Response automation
False Positive Reduction
- Machine learning refinement
- Threshold adjustment
- Pattern validation
- Context enrichment
- Alert correlation
These operational considerations ensure that UEBA systems remain efficient, effective, and manageable in real-world security operations environments.
Compliance and Governance
UEBA implementations must adhere to various regulatory requirements and support governance processes.
Regulatory Compliance:
Data Protection
- GDPR Compliance
- CCPA requirements
- PCI DSS controls
- HIPAA regulations
- SOX compliance
Audit Requirements
- Access logging
- Change tracking
- Investigation documentation
- Report generation
- Evidence preservation
Ensuring compliance with these regulations is critical for organizations operating in regulated industries or handling sensitive data.
Future Trends and Innovation
The field of UEBA is rapidly evolving, with new technologies and approaches emerging to address the ever-changing threat landscape.
Emerging Technologies
Advanced AI Integration:
Artificial Intelligence
- Autonomous response capabilities
- Natural language processing
- Cognitive computing
- Automated investigation
- Predictive analytics
Extended Detection and Response (XDR)
- XDR integration
- Unified security platforms
- Automated response orchestration
- Cross-platform correlation
- Threat hunting automation
Cloud Evolution:
Cloud-Native Capabilities
- Container Security – Kubernetes monitoring
- Serverless Security – Function monitoring
These emerging technologies promise to enhance the capabilities of UEBA systems further, enabling more sophisticated threat detection and response mechanisms.
Best Practices for UEBA Implementation
To maximize the effectiveness of UEBA, organizations should adhere to the following best practices:
- Define Clear Use Cases: Identify specific security scenarios and use cases that UEBA will address within your organization.
- Start with High-Value Assets: Focus initial UEBA implementation on protecting the most critical assets and sensitive data.
- Ensure Data Quality: Invest in data cleansing and normalization processes to ensure high-quality input for analytics.
- Continuous Tuning: Regularly review and adjust UEBA models and thresholds to improve accuracy and reduce false positives.
- Cross-Functional Collaboration: Involve stakeholders from IT, security, and business units in the UEBA implementation process.
- Integrate with Existing Workflows: Ensure UEBA insights are seamlessly incorporated into existing security operations and incident response processes.
- Provide Adequate Training: Educate security analysts and relevant personnel on interpreting and acting upon UEBA alerts.
- Implement Gradual Rollout: Start with a pilot program and gradually expand UEBA coverage across the organization.
- Establish Governance Framework: Develop clear policies and procedures for UEBA usage, data handling, and privacy considerations.
- Measure and Report on ROI: Define key performance indicators (KPIs) to measure the effectiveness and ROI of UEBA implementation.
Conclusion
User and Entity Behavior Analytics represents a significant advancement in cybersecurity. It offers organizations the ability to detect and respond to sophisticated threats that evade traditional security measures. By leveraging advanced analytics, machine learning, and a comprehensive view of user and entity behaviors, UEBA provides a powerful tool for modern security operations.
Successful implementation of UEBA requires careful consideration of architecture, deployment models, integration strategies, and operational aspects. Organizations must also stay abreast of emerging trends and continuously refine their UEBA capabilities to address evolving threats.
As cyber threats grow in complexity and scale, UEBA will play an increasingly critical role in helping organizations maintain a robust security posture. By following the guidelines and best practices outlined in this guide, organizations can harness UEBA’s full potential to enhance their threat detection and response capabilities.
FAQs

Get In Touch