Can We Trust GenAI For Zero Trust Architecture? Here’s What the Experts Revealed in Our AUA Session
Sunita Singhania
Jun 11, 2025
Today’s enterprise security teams are stretched thin.
Alerts flood in from every direction.
Attack surfaces expand faster than teams can respond.
And trust that was once built on firewalls and network zones now depends on dynamic, real-time decisions about users, data, and devices.
It’s a lot to keep up with!
Especially when the rules of the game keep changing.
That’s exactly why we brought together industry experts for a live AUA session to talk candidly about the role GenAI can play for Zero Trust architecture.
Not as a silver bullet. Not as a replacement for human judgment. But as a force multiplier for teams under pressure.
Led by our own security strategist, Sachin Jain, CTO, BuzzClan, and hosted by Abhi Garg, CRO, BuzzClan, the session cut through the noise and got real about what’s working, what’s not, and what’s next.
We’ve rounded up the key takeaways from the session — the real, unfiltered insights that security leaders are using to adapt faster and work smarter.
AI for Zero Trust: A New Era of Adaptive Cybersecurity
Zero Trust is built on a clear principle: “Never trust, always verify.”
Every request must be validated. Every action must be scrutinized.
But the rise of Generative AI complicates this equation.
After all, GenAI itself relies on trust in the training data it was fed, in the models that power it, and in the outputs it generates.
So how do we use AI for Zero Trust architecture without compromising the very foundation of that architecture?
Let’s break it down.
Extend Zero Trust to the AI Layer
The key isn’t to make exceptions for GenAI. It’s to hold it to the same standards as every other component in your system. That means:
- Verifying the integrity of training data and ensuring it’s free from manipulation or bias.
- Auditing model behavior and outputs, especially in high-stakes decision environments.
- Applying real-time guardrails — such as content filtering, access controls, and human-in-the-loop checks — to avoid overreliance on unchecked AI outputs.
In other words, AI should be treated as an untrusted entity until proven otherwise. Zero Trust doesn’t stop at users and devices — it now includes the AI systems themselves.
Evolving Threat Detection for GenAI-powered Insider Threats
Today’s adversaries aren’t just getting smarter — they’re getting automated.
With GenAI in their arsenal, they can easily and quickly create well-crafted phishing emails, subtle privilege escalations, or clean-looking data exfiltration scripts. These are no longer the blunt-force attacks of the past. They’re precise, adaptive, and increasingly difficult to detect using traditional behavioral analytics.
Good news?
GenAI can help close that gap by:
- Detecting intent-level anomalies, not just behavioral ones.
- Identifying context drift — when a user’s actions deviate subtly from expected business patterns.
- Spotting synthetic behaviors, like auto-generated content or automated queries designed to evade detection.
But detection is only part of the equation.
Human analysts bring the essential business context, risk awareness, and domain-specific knowledge needed to interpret these anomalies and make final decisions around mitigation, escalation, or containment.
Balancing Speed With Intelligence
A common concern with using GenAI is latency, as it processes vast amounts of data in real-time.
Sachin Jain, CTO of BuzzClan, broke this down into several practical strategies:
- Deploy lightweight AI models at the edge: Instead of routing data to centralized servers for heavy processing, organizations can use trimmed-down GenAI models deployed closer to where data is generated — at the edge. This enables near real-time security decisions without massive compute delays.
- Cache decisions where appropriate: Once a decision has been made, for instance, verifying a user’s identity or assessing a behavioral pattern, caching can be used to avoid re-running the full inference every time. This reduces load without compromising trust.
- Asynchronous verification models: In some cases, transactions can be flagged after the fact. If a system detects anomalous behavior retrospectively, it can trigger alerts, reverse actions, or initiate remediation workflows without slowing down the front-line experience.
As Sachin summed it up during the session:
“You get what you pay for. If you need millisecond decisions, you need edge computing, caching, and lightweight inference. If it’s low risk, async verification might work.”
Using RAG to Enable Context-Aware, Trustworthy AI
Once AI systems are operating within a Zero Trust model, the next step is making them more context-aware. That’s where Retrieval-Augmented Generation (RAG) comes in.
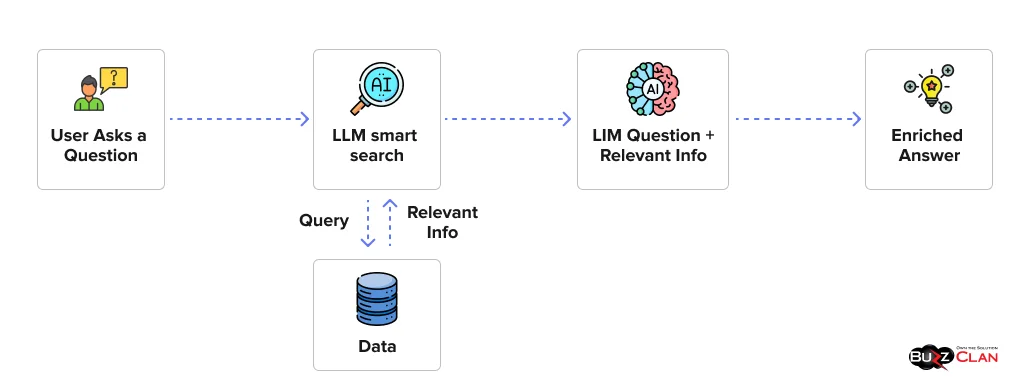
Rather than letting GenAI hallucinate or rely solely on opaque training data, RAG connects the AI model to a verifiable, business-specific knowledge base. This means you’re giving your AI system a secure, read-only window into company policies, known threat patterns, incident response plans, and system logs without hardcoding any of that into the model itself.
This offers two key advantages:
- Grounded Outputs: The AI’s responses are tethered to trusted, curated data sources, which can be version-controlled, access-restricted, and monitored.
- Dynamic Adaptation: As your organization’s environment evolves, so does the information the model retrieves without retraining the entire model.
Of course, RAG must be implemented with the same Zero Trust rigor:
- Limit what data the model can access.
- Log and monitor retrieval patterns.
- Sanitize sensitive outputs before they’re passed downstream.
RAG helps blend GenAI with security assurance by aligning the AI’s scope with your organization’s existing controls and context.
Integrating GenAI Into Existing Zero Trust Architecture Without Disruption
Using AI for your existing Zero Trust architecture doesn’t mean tearing down what already works. You want to add intelligence—strategically, incrementally, and with measurable outcomes.
Here’s how organizations can approach it:
Use AI as an Enabler, Not a Substitute
Start with low-friction use cases, for example, alert enrichment, anomaly scoring, or risk-based prioritization. This avoids disrupting core Zero Trust controls like identity verification or least privilege enforcement, while still adding value quickly.
Quantify ROI with operational and security metrics
Track improvements in incident response time, false positive reduction, and analyst workload. AI should lead to fewer missed threats, faster resolutions, and better analyst efficiency. These are the metrics that justify the investment.
Address the talent gap with a hybrid approach
Upskilling internal teams builds long-term maturity, but it takes time. Many companies are partnering with experienced vendors to kickstart implementations while training internal staff in parallel. It’s important to realize that you don’t want to become AI experts overnight; you want to become intelligent consumers of AI.
This phased, value-driven approach helps organizations scale GenAI adoption in Zero Trust environments while staying grounded in operational reality.
Final Thoughts
Zero Trust is constantly evolving. And GenAI acts as a catalyst, provided it is implemented thoughtfully.
From verifying the verifiers (your AI models) to identifying threats that would otherwise go unnoticed, GenAI can elevate your cybersecurity Zero Trust architecture by making it smarter, faster, and more adaptive.
It’s crucial to monitor how AI is trained, deployed, and monitored. It requires strong guardrails, clear metrics, and a mindset shift: to treat AI not as a magic wand, but as a trusted co-pilot.
As Sachin Jain aptly summed up, “This isn’t about doing everything with AI — it’s about knowing where it fits best.”